By Dancho Danchev
Utilizing basic site ‘stickiness’ and visitor retention practices, over the years, cybercrime-friendly communities have been vigorously competing to attract, satisfy, and retain their visitors. From exclusive services available only to community members, to DIY cybercrime-friendly tools, the practice is still a common way for the community administrators to boost the underground reputation of their forum.
However, there are certain communities that will use the underground reputation of their forum to boost their sales, by releasing private DIY cybercrime-friendly tools, and promoting them under the umbrella of the community brand.
In this post, I’ll profile a HTTP/SMTP-based keylogger that’s been commercially available to members of a cybercrime-friendly community since 2011.
More details:
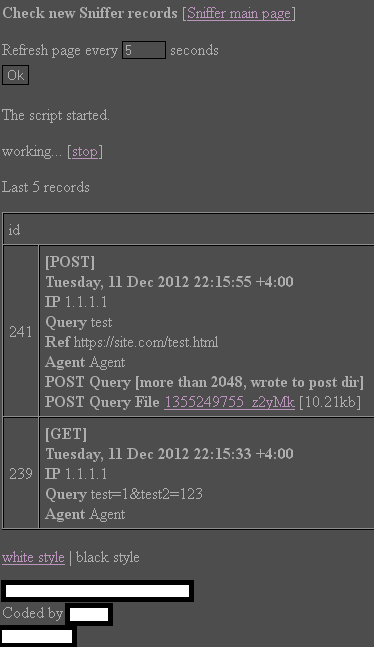
Sample screenshot of the HTTP/SMTP based keylogger in action:
Second screenshot of the HTTP/SMTP based keylogger in action:
Third screenshot of the HTTP/SMTP based keylogger in action:
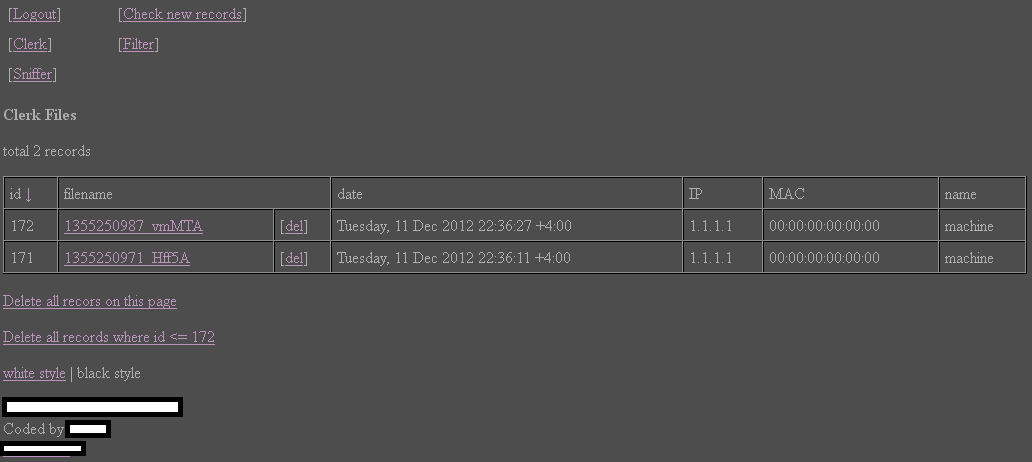
Sample HTTP/SMTP based keylogger log reading utility:
Some of the key features of the keylogger include the ability to automatically copy clipboard content in the log file, log infected PC information, write a separate log for each and every process, support for all languages, anti debugging capabilities, encrypted log files, uploading logs over HTTP or sending them to the cybercriminal behind the campaign over SMTP. What’s also worth emphasizing on regarding this particular keylogger is that the DIY builder is coded for each and every customer individually in an attempt to prevent detection by the security community.
The price? 60 WMZ (WebMoney) or ~$70.00 US
Despite the OPSEC-aware coder behind the keylogger, its lack of efficiency-centered and sophisticated log parsing capabilities will definitely prevent it from becoming a major tool in the arsenal of the modern cybercriminal.
What would happen if Webroot SecureAnywhere somehow “misses” a keylogging variant? Find out by watching this informative video.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.