While the authors/support teams of some of the market leading Web malware exploitation kits are competing on their way to be the first kit to introduce a new exploit on a mass scale, others, largely influenced by the re-emergence of the DIY (do-it-yourself) trend across the cybercrime ecosystem, continue relying on good old fashioned social engineering attacks.
In this post, I’ll profile a beneath-the-radar type of DIY Java-based botnet building tool, which is served through the usual unsigned, yet malicious Java applet.
More details:
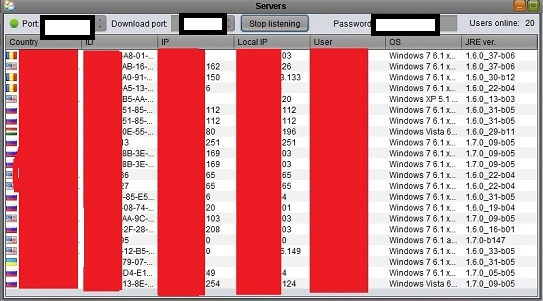
Sample screenshot of the DIY Java-based RAT botnet in action:
Some of its features include:
– The server size is 22kb
– Coded in Java, works on any OS (Linux, Mac, Windows)
– Uses two ports
– Uses no dependencies
– Any kind of file can be downloaded and executed on the affected hosts
– Infected hosts can also be redirected to any URL
– Can also be converted to DDoS bots
– Can also be sent a fake error message
– Can also be accessed using remote shell
– Can also be password protected
Although the release received some negative feedback insisting that the auto start-up feature does not work, other users are pointing out that they don’t need it to work, as they’ll basically just drop another executable on the affected hosts, as soon as they gain access to them.
We’ll continue monitoring its development, and post updates as soon as new developments emerge.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.