Thanks to the ease of generating a botnet, in 2013, stolen accounting data on a mass scale is a no longer a hot underground item, it’s a commodity, one that’s being offered by virtually all participants in the cybercrime ecosystem.
What happens once a Skype account gets compromised? There are several possible scenarios. The cybercriminals that (automatically) compromised it will either use the Skype credit for their own purposes, start spreading malware to the friends/colleagues of the compromised victim, or feed the accounting data into their arsenal of tools and tactics for launching TDoS (Telephony Denial of Service) services.
In this post, I’ll profile a novice cybercriminal’s underground market proposition, consisting of a DIY Skype ring flooder+training+a small amount of credit on a Skype account available in the package, and emphasize on why this particular release will never gain any market share, compared to the sophisticated and publicly available managed services.
More details:
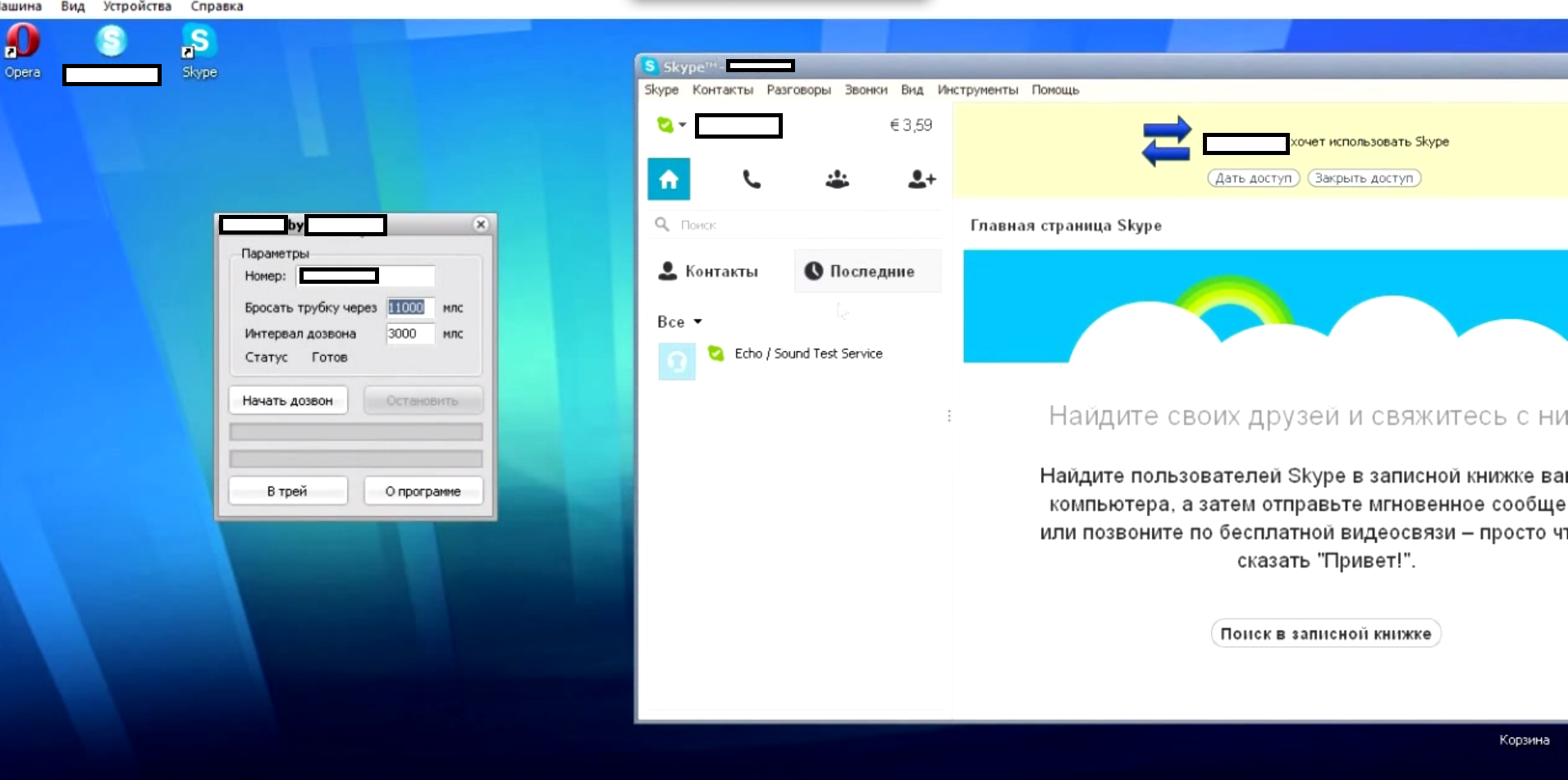
Sample screenshot of the DIY Skype rings flooder in action:
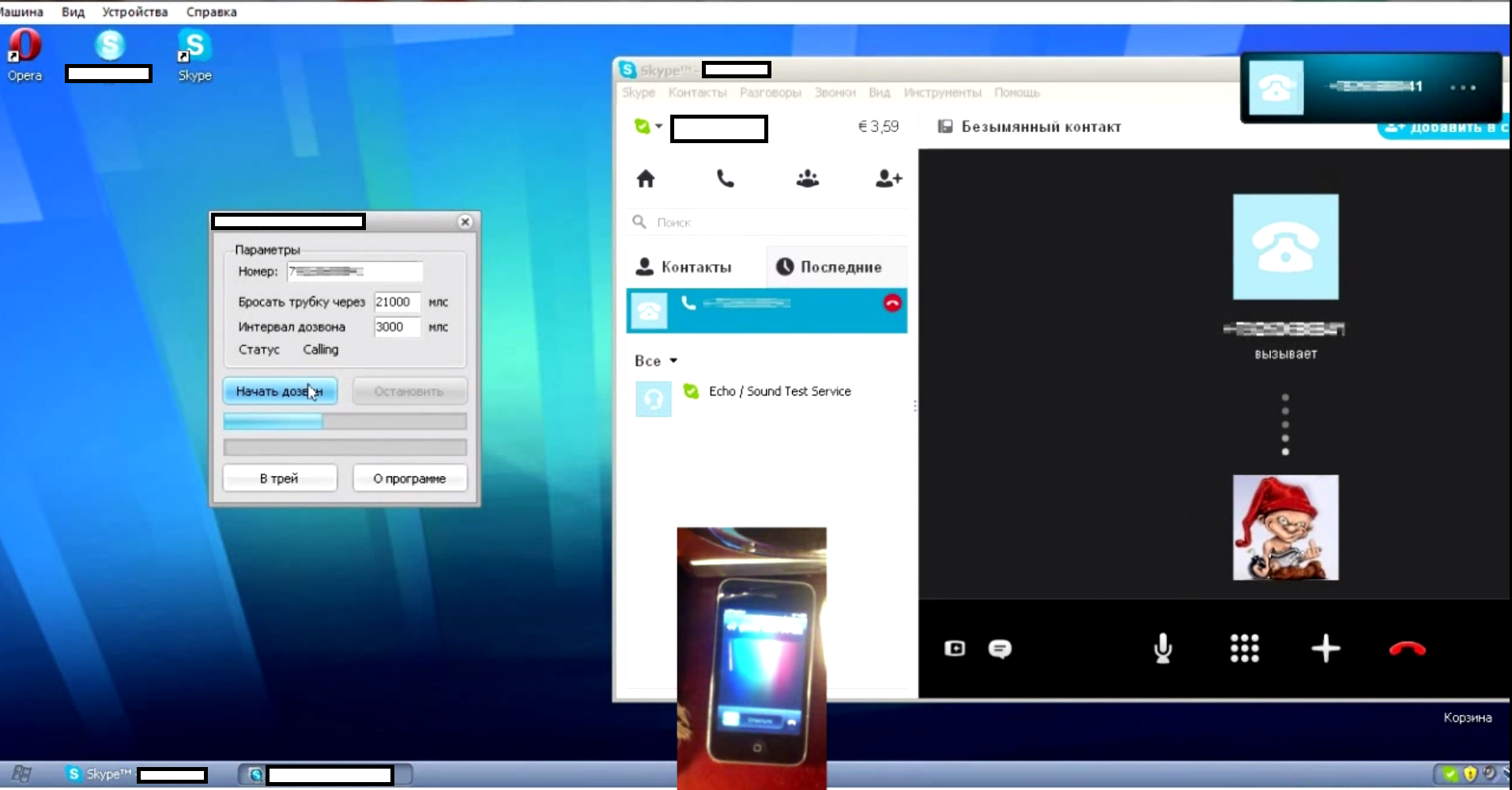
Second screenshot of the DIY Skype rings flooder in action:
The ring flooder works in a fairly simple way. Once the program detects a running Skype application, it will automatically start dialing any given number within a particular interval. It doesn’t support multiple accounts, or malware-infected hosts as anonymization proxies, making it a low level threat with a surprisingly high price, in this case, 490 rubles ($15.67).
Ring-based DIAL (Digitally Initiated Abuse of teLephones) type of attacks are just the tip of the iceberg, given the fact that cybercriminals also have access to SMS-based DoS (Denial of Service) attack tools, like the ones we’ve been profiling in previous posts:
- Russian cybercriminals release new DIY SMS flooder
- New Russian DIY SMS flooder using ICQ’s SMS sending feature spotted in the wild
- Cybercriminals abuse major U.S SMS gateways, release DIY Mail-to-SMS flooders
- Cybercriminals abuse Skype’s SMS sending feature, release DIY SMS flooders
What’s the driving force behind the author’s decision to charge this rather high price for his release? It’s due to the fact that he’s still thinking that underground market transparency doesn’t exist, allowing him to change a premium for a low quality “product”. And with underground marketplace transparency now an every day reality for the average cybercriminal, combined with vouching/invite-only registration model, escrow services, and Q&A oriented done on behalf of a community’s administrators before verifying the trusted nature of the deal, the entire ecosystem is empowered with the information flow generated by all the fraudulent and malicious activity going on online.
With some of the market participants already ‘vertically integrating’ in order to occupy a bigger market share of this emerging market segment, next to ring or SMS based TDoS/DIAL attacks, we expect them to continue capitalizing on the numerous malicious opportunities presented to them, and start targeting a victim’s voice mail in an automated fashion.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.