On a regular basis we profile various DIY (do it yourself) releases offered for sale on the underground marketplace with the idea to highlight the re-emergence of this concept which allows virtually anyone obtaining the leaked tools, or purchasing them, to launch targeted malware attacks.
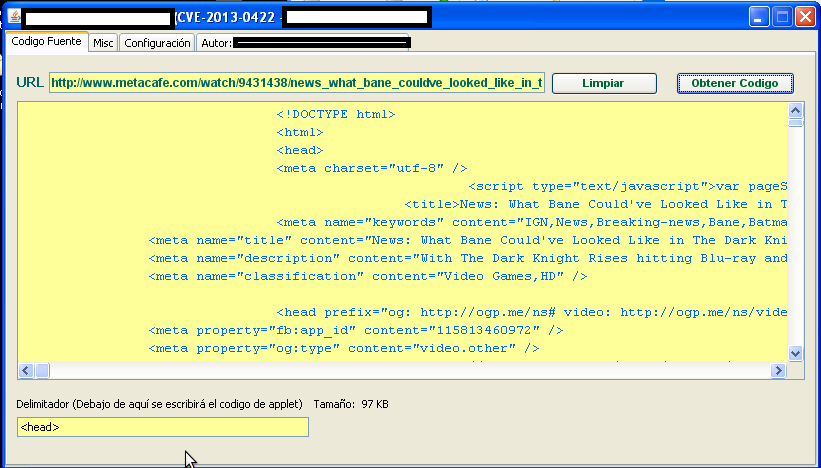
Can DIY exploit generating tools be considered as a threat to the market domination of Web malware exploitation kits? What’s the driving force behind their popularity? Let’s find out by profiling a tool that’s successfully generating an exploit (CVE-2013-0422) embedded Web page, relying on malicious Java applets.
More details:
Sample screenshot of the DIY exploit generating tool:
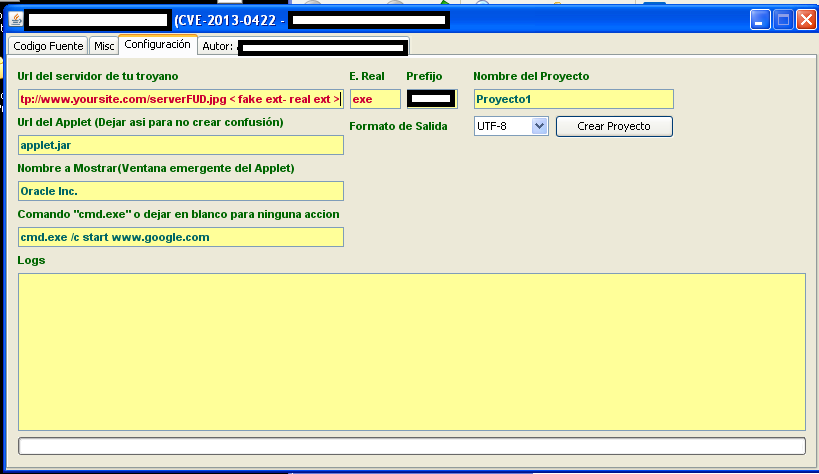
Second screenshot of the DIY exploit generating tools in action:
To use it, a cybercriminal submits a URL and the tool will embeds the exploit based on their preferences. The Web page then functions as a foundation for a successful social engineering attempt. The options provide the ability to choose a URL pointing to a malicious executable, define what happens once the exploitation takes place, and the name of the malicious Java applet.
DIY client-side exploits embedding tools aren’t new however; despite their popularity, they fail to achieve the efficiency levels offered by modern and systematically updated Web malware exploitation kits. What they make fairly easy to accomplish is to empower a potential cybercriminal with an extremely easy to use point’n’click tool, to assist them in targeted malware campaigns.
We’ll continue to monitor the re-emergence of the DIY cybercrime ecosystem market concept, and post updates as soon as new tools and services become available for cybercriminals to take advantage of.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.