By Tyler Moffitt
Recently we have seen an increase in fake installer scams attempting to trick computer users into installing disguised rootkits directly on their machines. In this post, we want to highlight how a scam like this can be installed and infect a machine, including behavior to watch out for as well as how to remedy the situation if it were to arise.
In the case of this infection, we are utilizing a bogus Adobe Flash Player installer. Normally, this file would be downloaded from a website after a message stating “You need the latest version of Flash to view this video” appears. The file being downloaded would have a random name, such as ‘flashplayerinstallerxxxx.exe’.
For educational purposes, we will show how this file reacts with a system without Webroot installed.
After execution, the file launches as a bogus Adobe flash player installer. During this process, it deletes the source executable that was initially dropped.
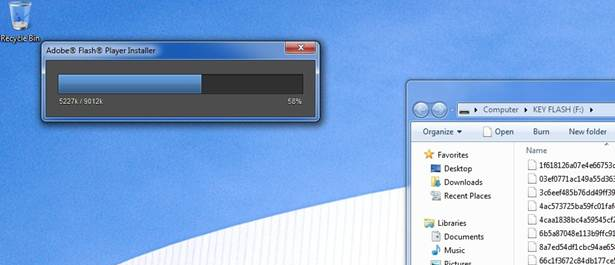
After the fake Adobe Flash update finishes loading, it will display a message (see screenshot below). Note that it doesn’t matter what version of Adobe flash player you have; even if you have no flash player installed, it will still report this message.
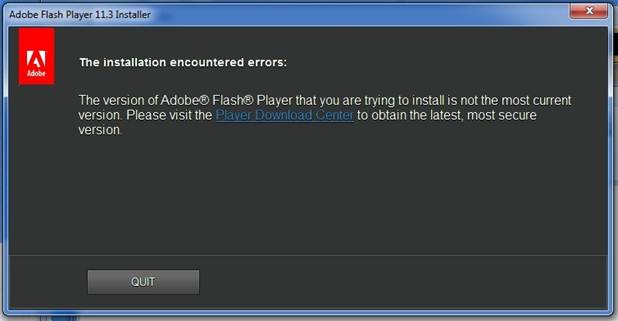
After about 10 minutes, the program will download components and get everything into place for infection. Then a new svchost.exe protected process will launch and start taking huge amounts of the CPU. This process cannot be killed.
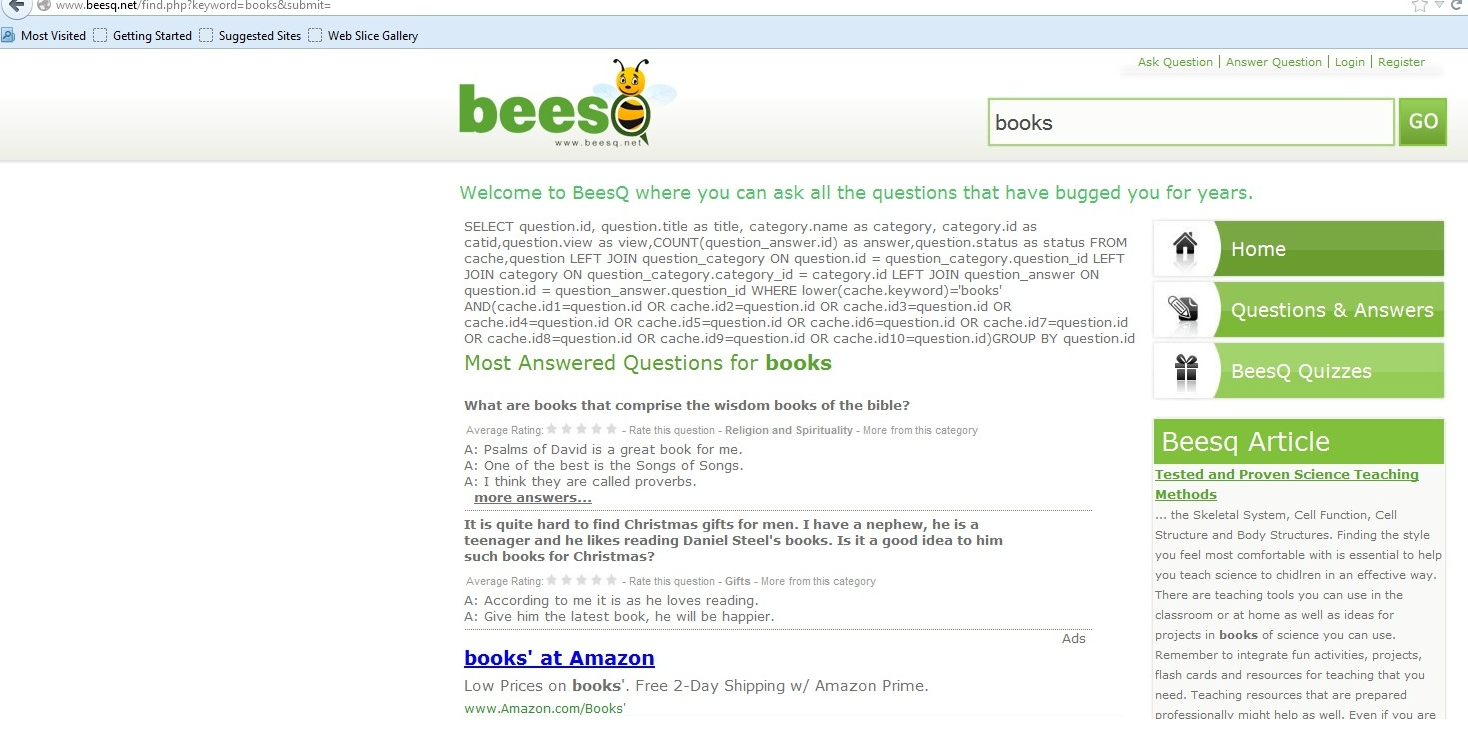
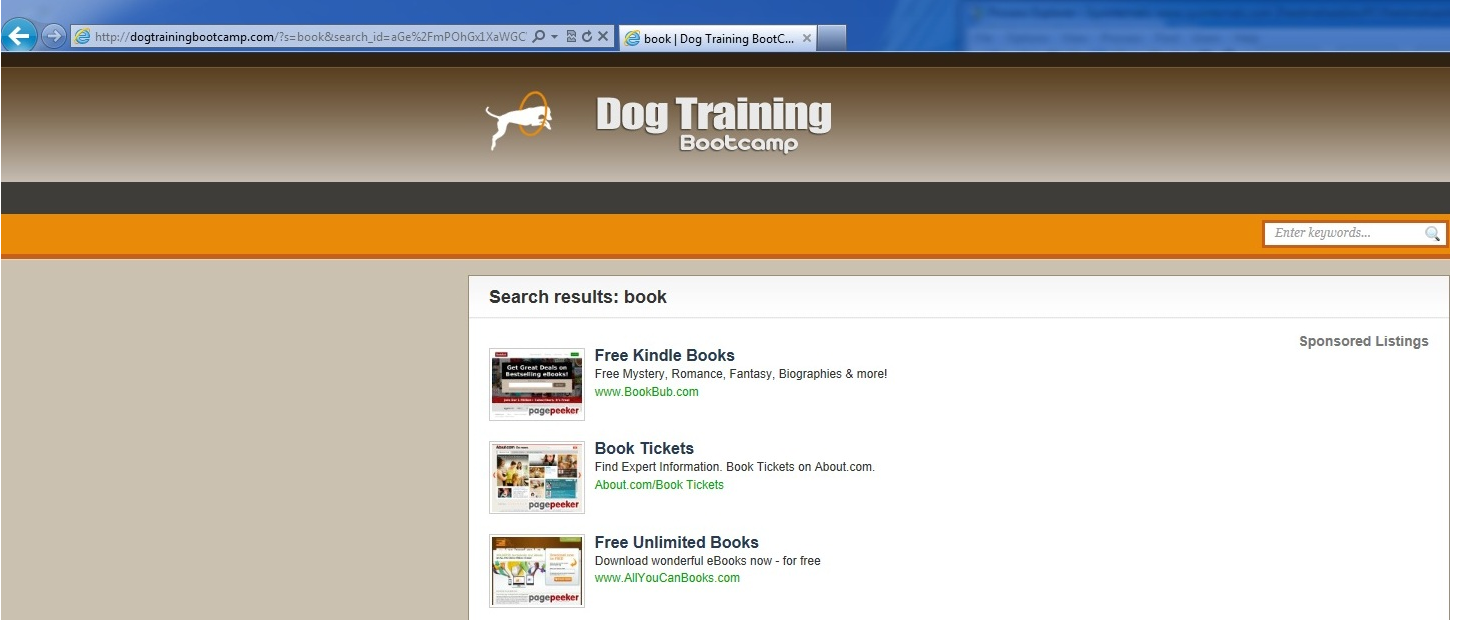
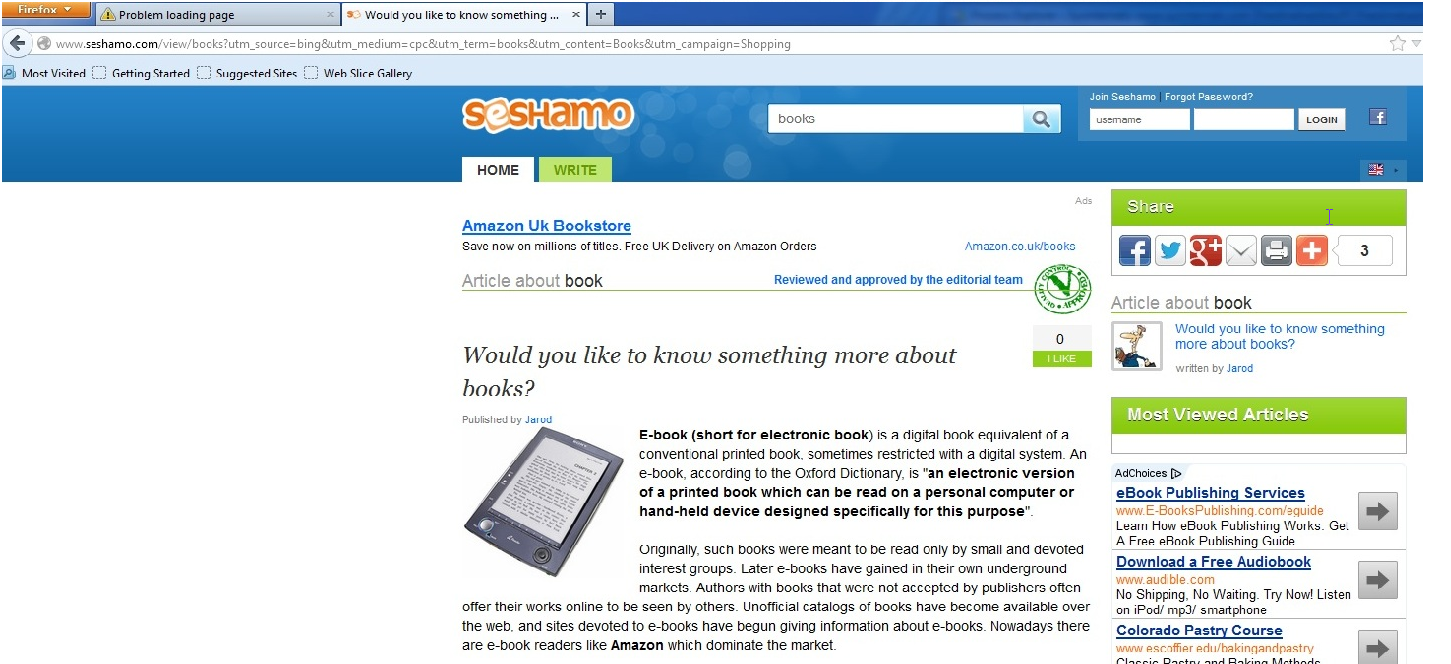
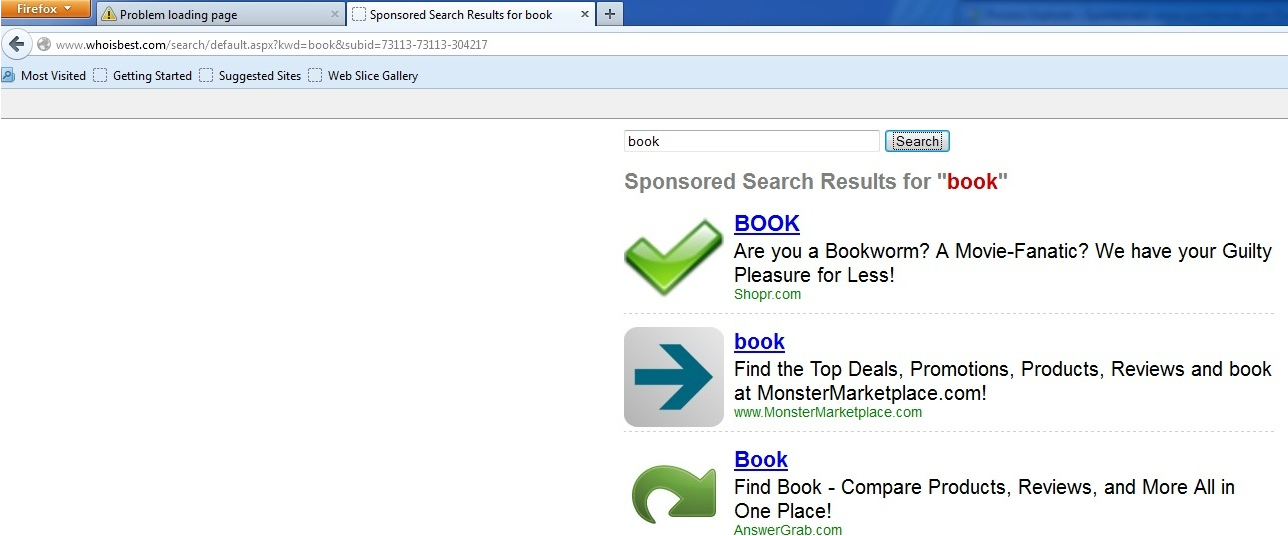
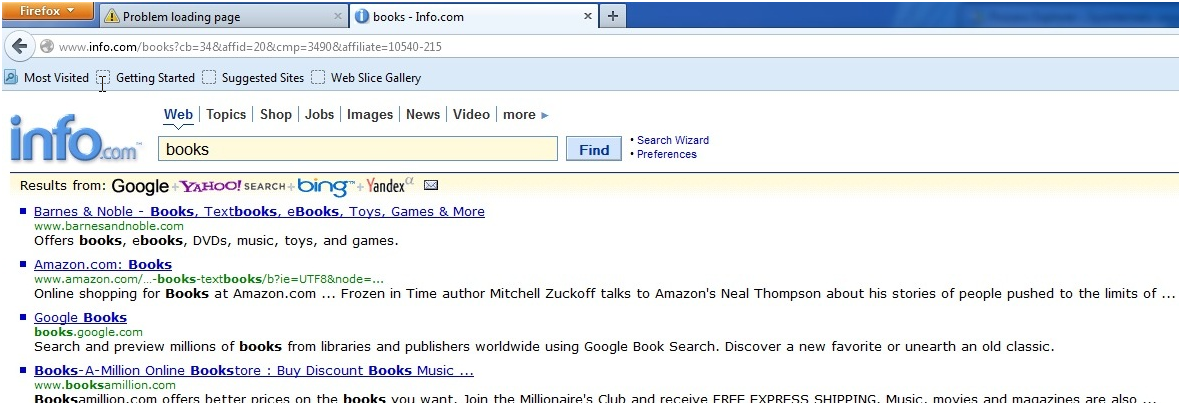
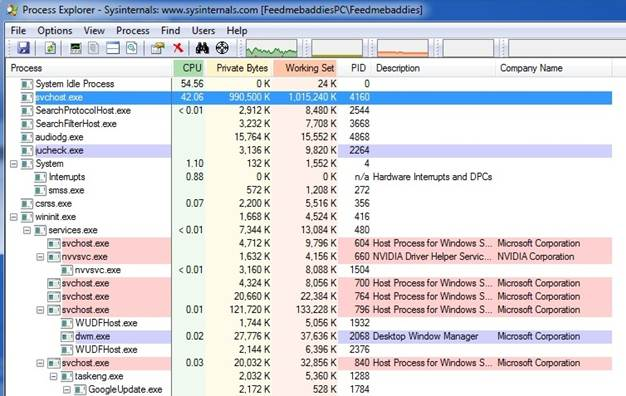 With the infection installed, all redirects are from Google search engine results. For this demonstration, we used Firefox and Internet Explorer, typed in “books”, and only clicked on the first 2 links (Amazon and NYTimes).
With the infection installed, all redirects are from Google search engine results. For this demonstration, we used Firefox and Internet Explorer, typed in “books”, and only clicked on the first 2 links (Amazon and NYTimes).
Since this is a rootkit, there are no toolbars/extensions/BHO’s added to the browser. There are also no modified proxy settings or modified hosts files. What is interesting about this rootkit sample is that the redirects do not happen every time. The action will occur about once every three attempts, where the user will get redirected to a series of sites that are shown below.
The number of redirects caps out around 4-5 and then everything will seem normal until a restart of the browser. This erratic action can make it extremely difficult to troubleshoot. It can also prove to be very frustrating for a user to explain as it is not consistent and once the redirection occurs enough times, the issue stops for the rest of the browsing session. We have seen instances where consumers have just been “living with it” for months.
Here are the loops of redirect sites:
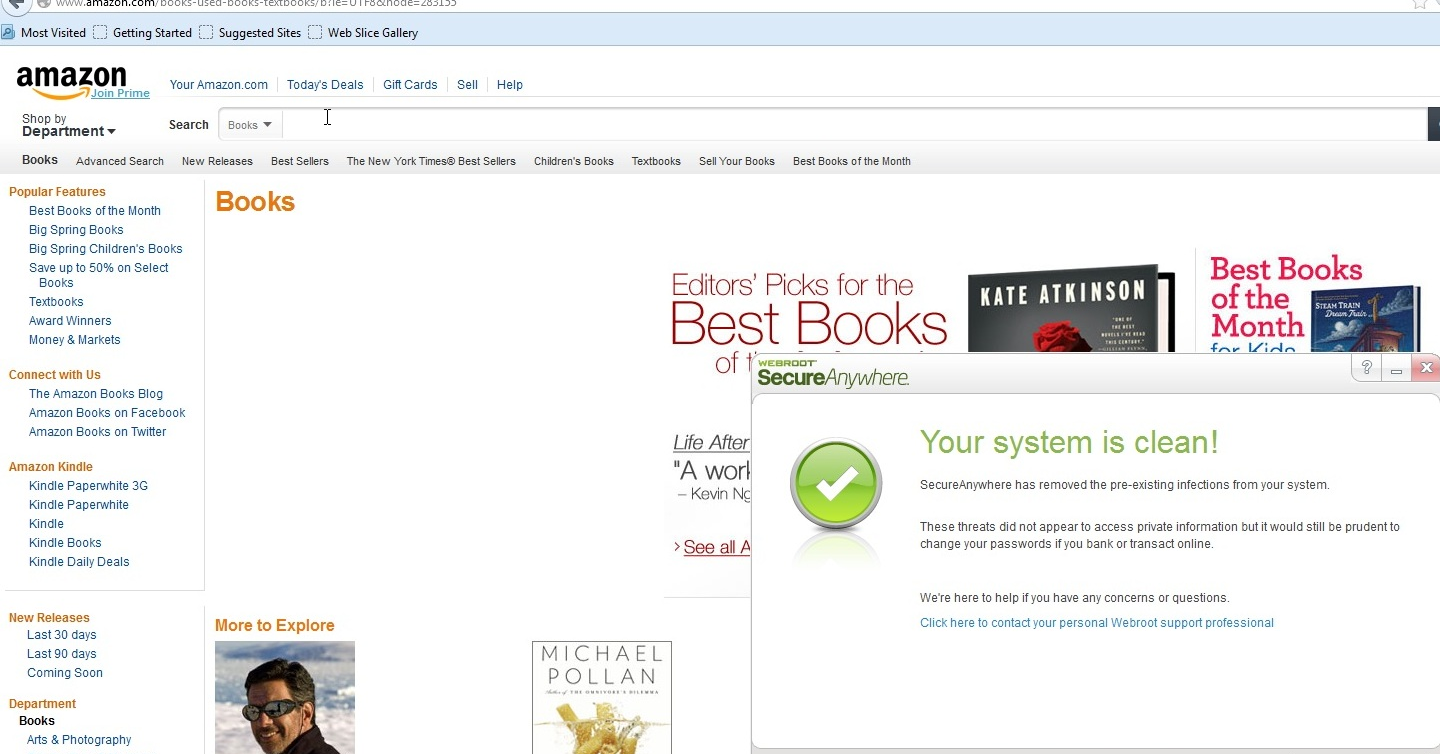
This is not an issue that any user should have to live with, however. After the infected code was running, we did a fresh install of Webroot SecureAnywhere onto the machine, which immediately detected and removed the infection. Below are screenshots of Webroot’s alert and threat removal in progress. Utilizing Webroot’s technology, a user is protected from malicious actions such as this, decreasing stress and improving the overall web experience.
As always, with these types of scams being so easy for the user to miss, there are a number of things users need to remember.
- Only install updates of software directly from the manufacturer’s website or from the software itself
- Check the URL of the websites you are visiting to ensure they match where you want to be
- Do not give out personal information (such as credit card information) through websites you do not know
- If in doubt, shut down your PC and contact Webroot
Removal:
Webroot SecureAnywhere automatically blocks the installation of this infection. If the PC has no AV software installed, booting into Safe Mode with networking and installing Webroot SecureAnywhere will remove the threat. Manually removing this threat is possible; however, there may be some system damage that will need to be repaired.
Webroot support is always available to help with removal and questions regarding this infection. Please visit the Webroot support web site for more detail at: http://www.webroot.com/support/.






Hi – this is a good and informative article – especially since the fake Adobe Installer looks and mimics the regular Adobe Updater as well as it seems to from the screenshots. As a System Admin that has purchased Webroot Corporate and deployed Webroot company-wide to our 31 locations, I appreciate an article like this. One request would be though to make the screenshots either larger (especially of the Fake Adober Installer) – or make them clickable so that we can see these in full quality to be able to see exactly what they look like. A LOT of Fake/Rogue Malware and Rootkits will have silly mispellings and things of that nature – but I can’t really tell by looking at those smaller shots if these do or not. The fact that the updates seem to ‘fail’ is a red-flag though. You would think they would just ‘act’ like it succeeded – and then if an actual Adobe Update came up with the same update later – a user would just ‘think’ it did not install correctly the last time. Thanks.
Webroot SecureAnywhere automatically blocks the installation of this infection. If the PC has no AV software installed, booting into Safe Mode with networking and installing Webroot SecureAnywhere will remove the threat. Manually removing this threat is possible; however, there may be some system damage that will need to be repaired Diablo 3 Gold
Tyler, what you have done here; showcasing what exactly a redirect virus can do to your computer, is brilliant!
It’s quite mind-blowing to not only see how these infections work, but to also stop and take into consideration the quantity of computers that have been affected by RootKit infections over the years, and the number that still get infected even right up to this day.
What’s really alarming however, is the intensity of a decent amount of these infections – now they are ordinarily used to play host to numerous viruses on top of the initial redirect infection.
I gave up the ghost when my computer first became infected, and chose to reinstall my operating system. At any rate, when I unfortunately got infected the second time around, the Webroot SecureAnywhere software that you folks provide here solved my problem while saving me a lot of time and headaches.
I would like to know how to remove a redirect that continues even though I have webroot installed?
Webroot cleared up my problems on my machine, however any time I use the internet I get redirects. Much of the time I get the warning that a malicious attack is ahead, and often I get the yellow webroot warning in the filter extension when sites are potential issues. I’ve accepted the issue, but I get tired of fighting the instant bog down any time I use the internet. It only occurs on initial launch and once I get to the page I’m in search of I no longer have problems during that session.
Specifically I want to know if there is something I can look for or change in my browser settings to eliminate it? Thank you.
Hello, Cynthia.
Absolutely. Redirects like this typically make their way onto your Computer by means of installing other Software, typically third-party. The location of where they hide can vary and requires manual remediation to fully resolve.
Lucky for you, that’s what we do! Please use the contact information below to reach our Advanced Malware Removal (AMR) Team.
They’ll get that redirect completely taken care of for you in just about no time completely free of charge.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator