Over the past 24 hours, we’ve intercepted yet another spam campaign impersonating Citibank in an attempt to socially engineer Citibank customers into thinking that they’ve received a Merchant Billing Statement. Once users execute the malicious attachment found in the fake emails, their PCs automatically join the botnet operated by the cybercriminal/cybercriminals.
More details:
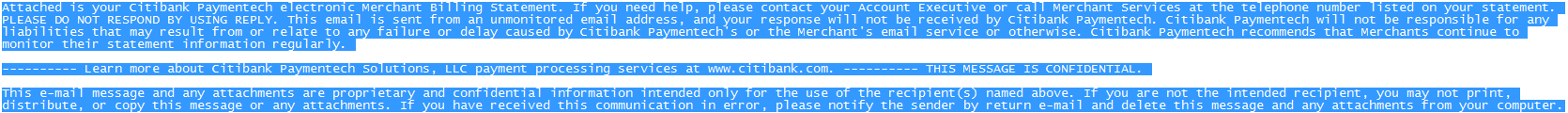
Sample screenshot of the spamvertised email:
Detection rate for the malicious executable:
MD5: 75a666f81847ccf7656790162e6a666a – detected by 20 out of 46 antivirus scanners as Trojan-Spy.Win32.Zbot.lcnn.
Once executed, the sample drops the following files on the affected hosts:
MD5: d41d8cd98f00b204e9800998ecf8427e
MD5: 758498d6b275e58e3c83494ad6080ac2
MD5: 342b7a0425bb3b671854bc7a4823d378
MD5: 2401466fb91045ac970a1dbb1a468783
It then starts listening on port 16985, allowing the cybercriminals behind the campaign to gain complete access to the host.
The sample also creates the following Mutexes:
Local{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Global{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global{EE3082BB-B2DA-15DD-11EB-B06D3016937F}
Global{EE3082BB-B2DA-15DD-75EA-B06D5417937F}
Global{EE3082BB-B2DA-15DD-4DE9-B06D6C14937F}
Global{EE3082BB-B2DA-15DD-65E9-B06D4414937F}
Global{EE3082BB-B2DA-15DD-89E9-B06DA814937F}
Global{EE3082BB-B2DA-15DD-BDE9-B06D9C14937F}
Global{EE3082BB-B2DA-15DD-51E8-B06D7015937F}
Global{EE3082BB-B2DA-15DD-81E8-B06DA015937F}
Global{EE3082BB-B2DA-15DD-FDE8-B06DDC15937F}
Global{EE3082BB-B2DA-15DD-0DEF-B06D2C12937F}
Global{EE3082BB-B2DA-15DD-5DEF-B06D7C12937F}
Global{EE3082BB-B2DA-15DD-95EE-B06DB413937F}
Global{EE3082BB-B2DA-15DD-F1EE-B06DD013937F}
Global{EE3082BB-B2DA-15DD-89EB-B06DA816937F}
Global{EE3082BB-B2DA-15DD-F9EF-B06DD812937F}
Global{EE3082BB-B2DA-15DD-E5EF-B06DC412937F}
Global{EE3082BB-B2DA-15DD-0DEE-B06D2C13937F}
Global{EE3082BB-B2DA-15DD-09ED-B06D2810937F}
Global{EE3082BB-B2DA-15DD-51EF-B06D7012937F}
Global{EE3082BB-B2DA-15DD-35EC-B06D1411937F}
Global{EE3082BB-B2DA-15DD-B1EA-B06D9017937F}
Global{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
The following Registry Keys/Registry Values:
HKEY_CURRENT_USERSoftwareMicrosoftIbesja
[HKEY_CURRENT_USERIdentities] -> Identity Login = 0x00098053
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> {3DFA1AE4-115C-AD7B-A6BA-A75086AF8442} = “”%AppData%Uczeutapi.exe””
[HKEY_CURRENT_USERSoftwareMicrosoftIbesja] -> 8fb916j = 2D AA 36 D5 F8 C7 A9 7A; dba3gc5 = “MapX1Q==”; 1fadc141 = “4P5X1fOYmnpmmWX7”
It then phones back to the following C&C servers:
1.168.36.175:19755
174.89.51.54:28289
190.73.229.164:12407
194.94.127.98:25549
24.120.165.58:21251
66.63.204.26:29482
72.20.156.250:17157
75.87.65.147:12014
83.21.8.24:10220
85.113.97.137:23397
99.103.42.49:26480
83.213.40.53
190.75.107.92
75.61.139.23
189.223.135.118
81.149.242.235
64.231.249.250
195.169.125.228
99.190.186.102
182.8.170.153
93.63.139.146
190.1.235.59
41.70.190.218
81.88.151.109
90.156.118.144
151.45.10.230
190.17.161.62
68.199.158.93
67.52.7.174
46.40.121.209
212.49.41.106
124.122.199.15
188.14.124.180
186.92.102.126
173.185.182.58
95.91.233.77
5.118.250.166
93.202.97.42
More MD5s are known to have phoned back to the same C&C servers. For instance:
MD5: c8b9b1629fe3f1d784b8fd5b1465150a
MD5: 5024ed66fa3e02f95511a79a514144c4
MD5: fcaadadcdb87e839eb67af02bf9882c4
MD5: 0d5d0889bc06f0d63cb6b97397f11218
MD5: 54403dbf585eb8fb78ab846eb0ab18f0
MD5: 08089785b0242fc8338011321b831225
MD5: 2a8931354bf61749cbf6f24e0db74b89
MD5: cb31ee582ade86cad0bc6d7623d2ffb4
MD5: 77ae7d1b2cf3022e36aabec6299250a1
MD5: 68fa7293bd813541cc246aad52447673
MD5: 28b1c209bdc0154594e26e85da0c0fcf
MD5: 84c420d0bec5aab11d2f0a14d2dae0cc
MD5: 886f553ed58aee042d7d95eaa30e05b3
MD5: 5b02a6ce7c3335163804b3ae751e8157
MD5: a073ab44745fd1ae401136f001c5651b
MD5: c4d9c501e27e069dedd59263031c8083
MD5: 06b89c4124ad2d8671b027a4d9c17650
MD5: 1e670e14b9474b82431fbf9dfc66b2de
MD5: e20a5ed1d6ce0821680e507d7db97256
MD5: 8394b0b6754ab39854bb68862fa90948
MD5: 7f0a7f2cc47adae80ca88d754c6fc9fa
MD5: b49eb68373531cf053cbc3d8a34e93b1
MD5: 9b0c97252a8d69bdd795d50be071a6c8
MD5: fe76d90d3913d01df04c9495fa2722fe
MD5: d9bb2ff8052e54ed8cc223960e2436e6
MD5: f1c9f0e6f84a12f54dc57a3e5afa2c4b
MD5: e15d9045cd38fd340c7322511abc6072
MD5: c274192e65f1795926b0d6e0eb41695b
MD5: b4f7154414adb452f71af868179f5e99
MD5: e401377952b66d8c600e0a56ccdae9d7
MD5: 6078c25813d0fcbff40b62b911672baa
MD5: 765137dbcaa178efc4d81c0b3ed18cd1
MD5: fde19d3fd7367fde018e42222db16d7b
MD5: c003911fd87c141680374c9b186f14ea
MD5: 4a3fd9fe00f4ed1dbfdf1b9e8d2cd835
MD5: c003911fd87c141680374c9b186f14ea
MD5: 3b3b6a60a45870239f19b188bcecb24d
MD5: 4a3fd9fe00f4ed1dbfdf1b9e8d2cd835
MD5: e74cd8aa61a71c97dc9df6244452d3e8
MD5: f4f46785aec169533dda598869b4f652
MD5: 773347409e3c0276409f72f5b54ebba5
MD5: 9e77a332203aa1f6e5f77e3b91990106
MD5: f4a95f23af26ce5d9bd4e9757248e62f
MD5: 0fe5ed4acf78fd887d7468e602ad2917
MD5: 9a08e275eb2503256450e87ab588d2c8
MD5: eb288beb41039421b398a334e6026d54
MD5: 6331be83df34d74e88bae1cf261d9902
MD5: 8145cdf4586697018e30a2a07cd8cee9
MD5: d463e429d88a082c72f1cdf26eb5d8e6
MD5: 39197e008d5f00f577f0072efb66462c
MD5: b8bd69f7b8ee5b3089225ad12735660f
MD5: 2c9eec6c46eb1761b3f4ae62b2aeb15f
MD5: 5bb8a9e2cc46d8162d0db8be014f6398
MD5: 7472a5c90949ff645e226ec48951210b
MD5: 3b0aea6adbe8ec91e6d71547505e2c2c
MD5: 9044defbcb38437f9f219a59bd49d1cc
MD5: 494c1c9616896fb656bd885ad0ab7ca3
MD5: b940fb3dc83345933a3b78aa177afbd3
MD5: 930f22061d02c04f69d8c4599cce0b54
MD5: 6078b4a1221653e425d9f91ea333a563
MD5: af288964ea76a531858679cf6178726d
MD5: 3304558040f63556f872870896b6e52b
MD5: 54c884c93357d49354792a1fc0d8e124
MD5: 9155ecf1478f60c375b4f7584cfb8006
MD5: f2ed432cf7817f3df29afc21f9f1a085
MD5: fb543cef3e2fa90713014fbc866937df
MD5: 8c7d14930299c319c08a535d0d9d5ba0
MD5: 3527b667829c8c65746770589cbbf67b
MD5: f059eeea22a879b77ac5088377a4ebf4
MD5: 29d442849d88648e0dc0e1a7dd67565d
MD5: 7dca26120ce7bde79de3c230f267dad6
MD5: b5337fc7eee78398a8343cc87c93e6a3
MD5: b5337fc7eee78398a8343cc87c93e6a3
MD5: b92c3bb6ebd037120ce0b16757da5188
MD5: 7fb2b4ed0be7d9c89568b7d7dcada0c6
MD5: 9fa09623f675bd4a4fc0776c593ba40e
MD5: e0d2c82d502a1e825b006c416fad865d
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.