Our sensors just picked up a rogue advertisement served through the Yieldmanager ad network, which exposes users to fake Adobe Flash Player HD ads, ultimately dropping a copy of the potentially unwanted application (PUA)/adware, known as Somoto Better Installer.
More details:
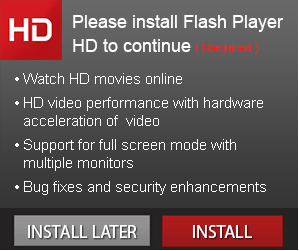
Sample screenshot of the actual advertisement:
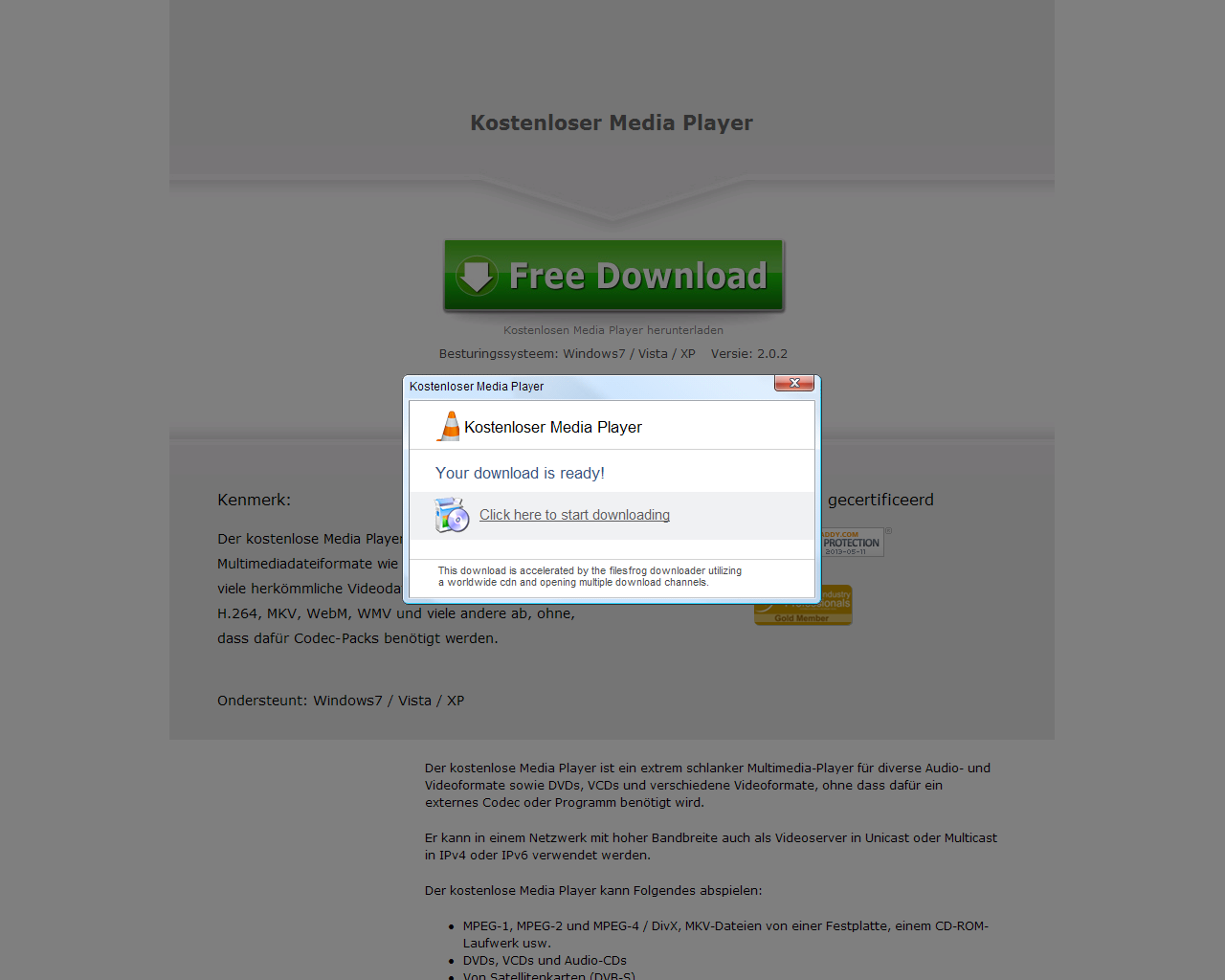
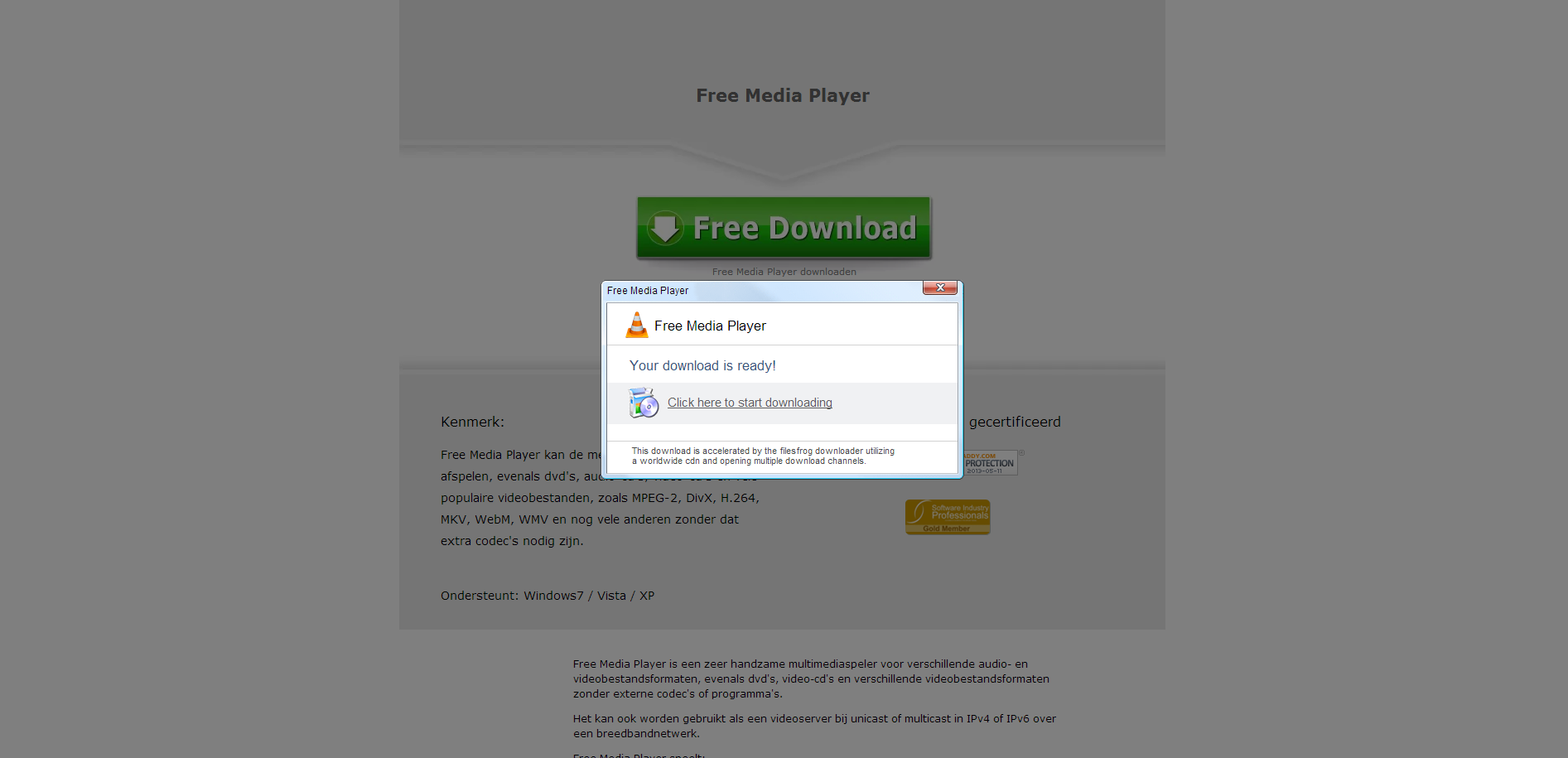
Surprisingly, once users click, they’re presented with a rogue Free Media Player page, instead of of a Adobe Flash Player HD themed page. Users who fall victim to the social engineering scam will end up installing multiple potentially unwanted applications.
Yieldmanager ad URL:
hxxp://ad.yieldmanager.com/clk?3,eJyljd1ugkAQhZ.GO0qWv7Bk04tBpEpZBbOVyN2yQkWxEt10I0.fJbS-QE8mZ07mJ5.lENygA8duhZE4uNwVxHLqwKu9qmkqAxFCHOT7VuBbXmAsH4mEZLt4z-d1MogQRqX9huUw6XO01ZQzPHoI9-Ir-92fXiib0ry33yj8Q7dd-AfVPKXREYbMN7uOueHzKhIPGoFaX1Z2WiTHDVtIyuKOtsgri48hZfFpP8TnkgFaR9u2zJ-fr4ZxlLKfOTCzY11KKZPfJe.4d6ubKa4XPf0Bx21b5Q==,
Landing domain:
hxxp://www.softigloo.com – 78.138.105.151. Responding to the same IP is also the following typosquatted domain – hxxp://down1oads.com
Detection rate for the sampled malware:
MD5: 3ee49800cc3c2ce74fa63e6174c81dff – detected by 8 out of 46 antivirus scanners as Somoto BetterInstaller; Adware.Somoto
MD5: b57cc4b5aecd69eb57063f4de914d4dd – detected by 8 out of 46 antivirus scanners as 8 out of 46 antivirus scanners as Somoto BetterInstaller; TROJ_GEN.F47V0429
Once executed, MD5: b57cc4b5aecd69eb57063f4de914d4dd creates the following files on the affected hosts:
C:DOCUME~1<USER>~1LOCALS~1Tempnsh2.tmp
C:DOCUME~1<USER>~1LOCALS~1Tempbiclient.exe
C:DOCUME~1<USER>~1LOCALS~1Tempconfig.ini
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.0
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.2
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.5
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.4
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.3
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.6
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.7
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe.1
C:DOCUME~1<USER>~1LOCALS~1Tempbundlesweetimsetup.exe
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.0
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.1
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.2
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.3
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.4
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.5
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.6
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe.7
C:DOCUME~1<USER>~1LOCALS~1TempDeltaTB.exe
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.0
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.2
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.1
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.3
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.4
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.5
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.6
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe.7
C:DOCUME~1<USER>~1LOCALS~1TempLollipopInstaller_somoto_14693.exe
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.2
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.3
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.4
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.5
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.0
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.1
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.6
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe.7
C:DOCUME~1<USER>~1LOCALS~1TempLyricsPal.exe
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.0
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.1
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.2
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.3
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.4
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.7
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.5
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe.6
C:DOCUME~1<USER>~1LOCALS~1Temp7z920.exe
Creates the following Mutexes:
CTF.LBES.MutexDefaultS-1-5-21-1275210071-920026266-1060284298-1003
CTF.Compart.MutexDefaultS-1-5-21-1275210071-920026266-1060284298-1003
CTF.Asm.MutexDefaultS-1-5-21-1275210071-920026266-1060284298-1003
CTF.Layouts.MutexDefaultS-1-5-21-1275210071-920026266-1060284298-1003
CTF.TMD.MutexDefaultS-1-5-21-1275210071-920026266-1060284298-1003
Makes the following DNS requests:
bi.bisrv.com (78.138.97.8)
installercdn.filebulldog.com (54.239.158.183)
static.bisrv.com (78.138.97.8)
cdn.bisrv.com (54.239.158.151)
cdn.bispd.com (78.138.127.129)
installercdn.betterinstaller.com (54.239.158.63)
installer.betterinstaller.com (78.138.97.8)
download.filesfrog.com (78.138.127.7)
And initiates the following TCP connections:
78.138.97.8:80
54.239.158.55:80
78.138.127.129:80
54.239.158.183:80
54.239.158.247:80
78.138.127.7:80
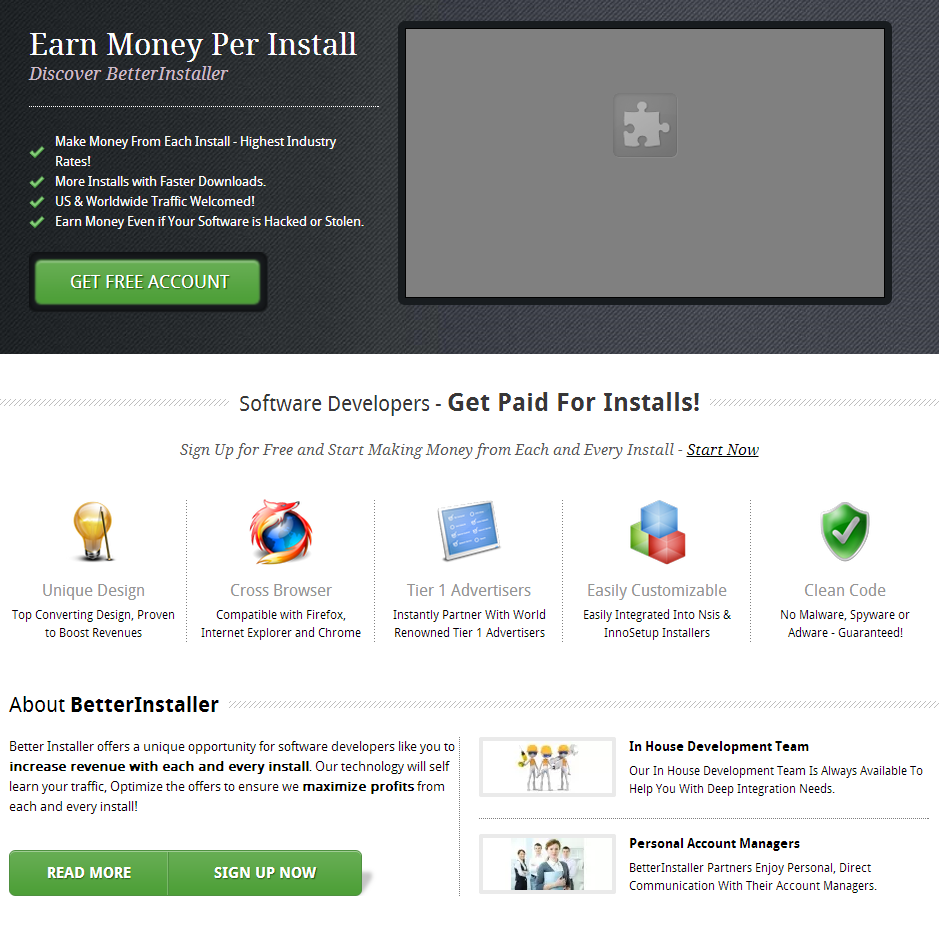
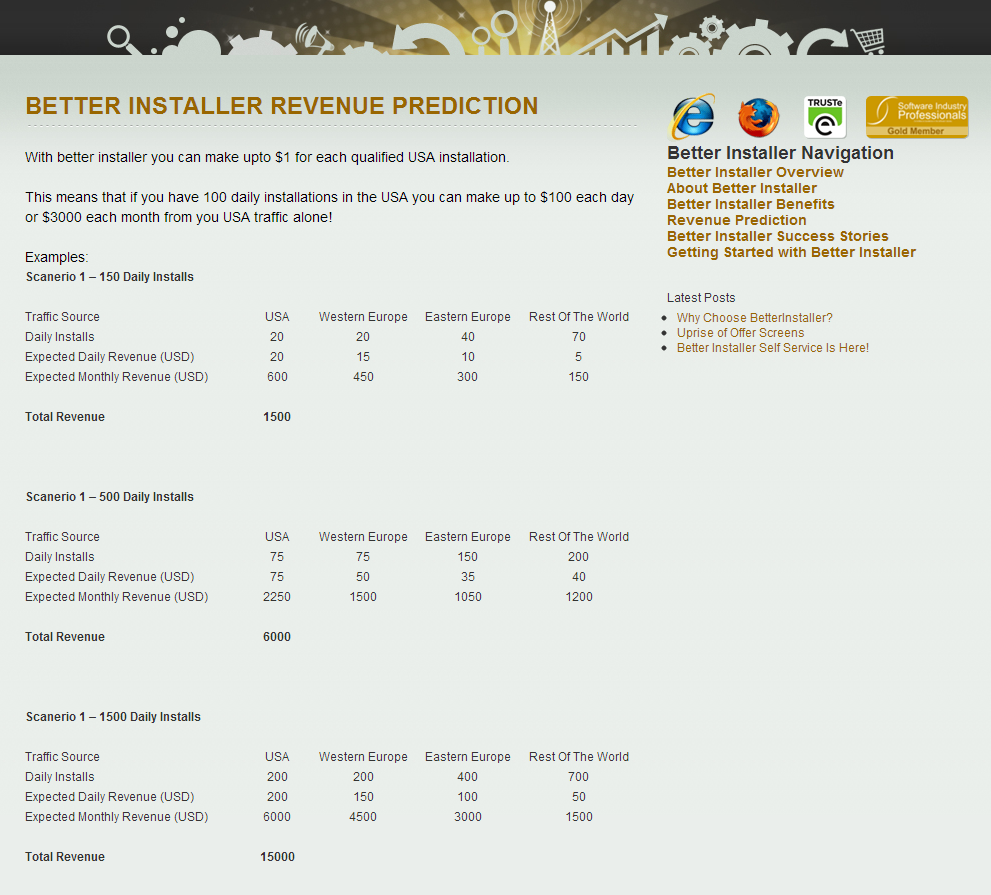
The affiliate network participant that’s abusing the Yieldmanager ad network is currently earning revenue through the Somoto’s BetterInstaller PPI (Pay-Per-Install) revenue sharing network:
We’ll be definitely keeping an eye on this PPI revenue-sharing network, especially on the deceptive advertising done on behalf of its participants.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.






Can I get rid of this? It’s everywhere and I HATE it!!
Thank you for the article.