By Israel Chavarria
Recently we have seen a spike of this ransomware in the wild and it appears as though its creators are not easily giving up. This infection takes your computer hostage and makes it look as though the authorities are after you, when in reality this is all just an elaborate attempt to make you pay to unblock your computer.
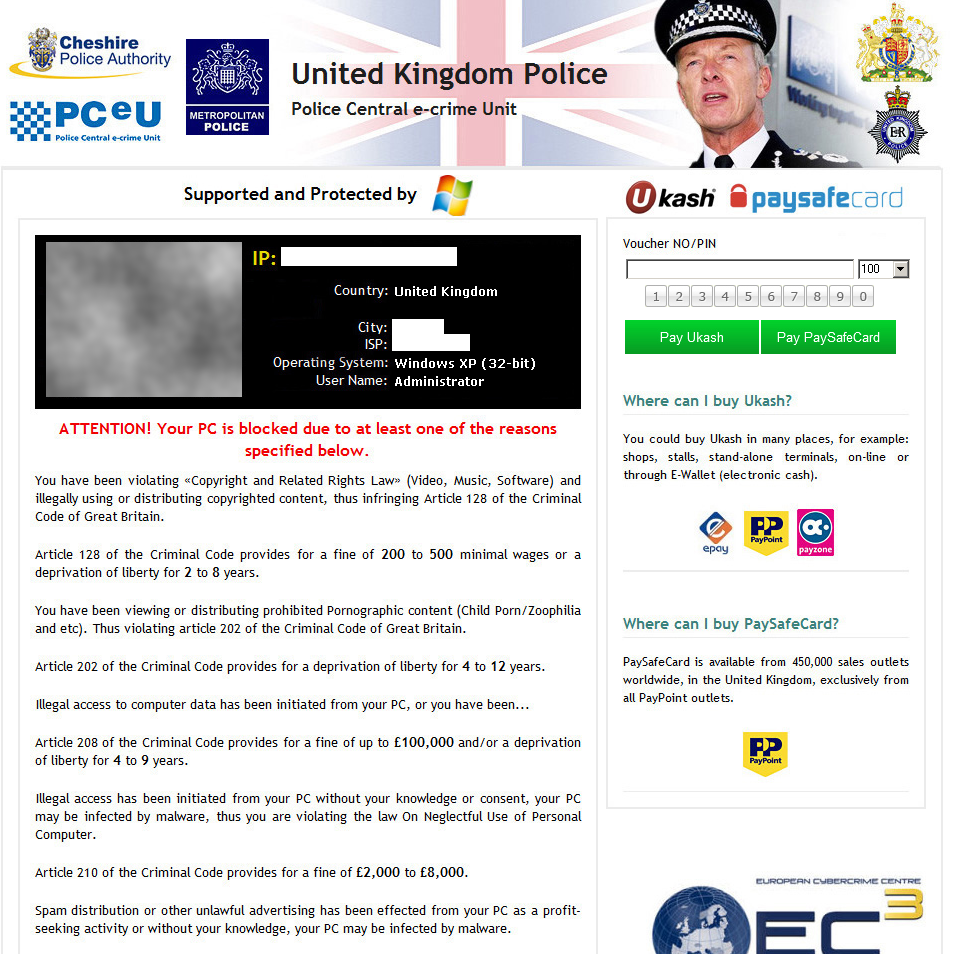
Once infected, a warning similar to the one below will take up your entire screen in such a way that you can’t get around it, thus effectively blocking you from accessing your files, programs or anything else on your computer. To further scare you into believing that you’ve been caught in illegal activity, your IP address, rough location, internet service provider, operating system and webcam image may be displayed.
To ensure maximum profits, the malware writers made sure that everyone understood their warning and payment instructions by localizing the infection around the world. Here are just a few examples:
We should mention that there are variants of this infection that will encrypt your files so even after the infection is removed, documents, pictures and many other files on the hard drive will be inaccessible. Once the files are encrypted it can be very difficult or impossible to restore the original unencrypted versions. To avoid data loss, we strongly suggest periodically backing up your data.
Webroot proactively protects you from this infection but if you happen to be hit with this ransom, there are a number of ways to get around it.
Recovery
If you have already tried all Safe Mode options and you were blocked by the infection you may want to try a system restore first. If however, you are able to access Safe Mode with Networking installing Webroot SecureAnywhere and running a scan would be a wise first step.
System Restore:
- Windows 8: http://windows.microsoft.com/en-us/windows-8/windows-startup-settings-including-safe-mode
Windows Vista/7: http://windows.microsoft.com/en-us/windows7/what-are-the-system-recovery-options-in-windows-7
Windows XP: http://support.microsoft.com/kb/304449
For advanced users, manual removal of this infection can be achieved by using the recovery options, a Windows repair CD, or a live Linux CD/USB to remove the files and/or edit the registry. Again, there are a number of ways to go about this so we won’t go into all the details here but rather provide you a general guide on what to look for.
The infection executable may be located in the AppData, Temp, or User Profile directories and typically loads by adding itself to the Run keys or by modifying the Winlogon Shell entry. In some cases it may load using only a shortcut that’s placed in the Startup folder.
Webroot support is always available to help with removal and questions regarding this infection. Please visit the Webroot support web site for more detail at: https://www.webroot.com/support/.