By Tyler Moffitt
We’ve seen quite a few audio ads infecting users recently. We think it’s a good idea to go over an in-depth look at how they infect your computer and how to remediation them.
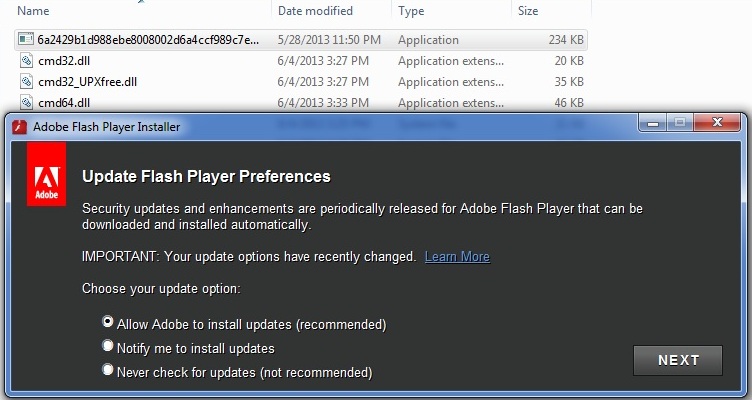
As you can see in this first picture, this is another Adobe Flash spoof that launches its signature update window.
You might not be able to see, but the “f” is a little off on the tiny icon at the top left. Either way it looks quite legitimate. It doesn’t matter what option you check; once you click “NEXT” you’ll get this next window.
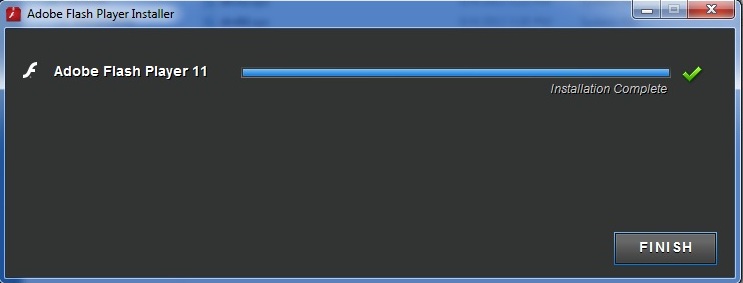
So far this seems completely official and harmless. It even takes it’s time progressing the loading bar. However, once you click “Finish” everything closes down and the computer reboots. The command force quits all applications so you won’t have time to save anything or cancel the shutdown. Once the computer reboots there is no final closing message from “Adobe”, but everything seems normal for a few minutes. After about three to five minutes the computer slows down to a crawl and Audio ads start playing in the background. By now users start to worry about foul play with their computer so here’s a look at what’s going on at this point.
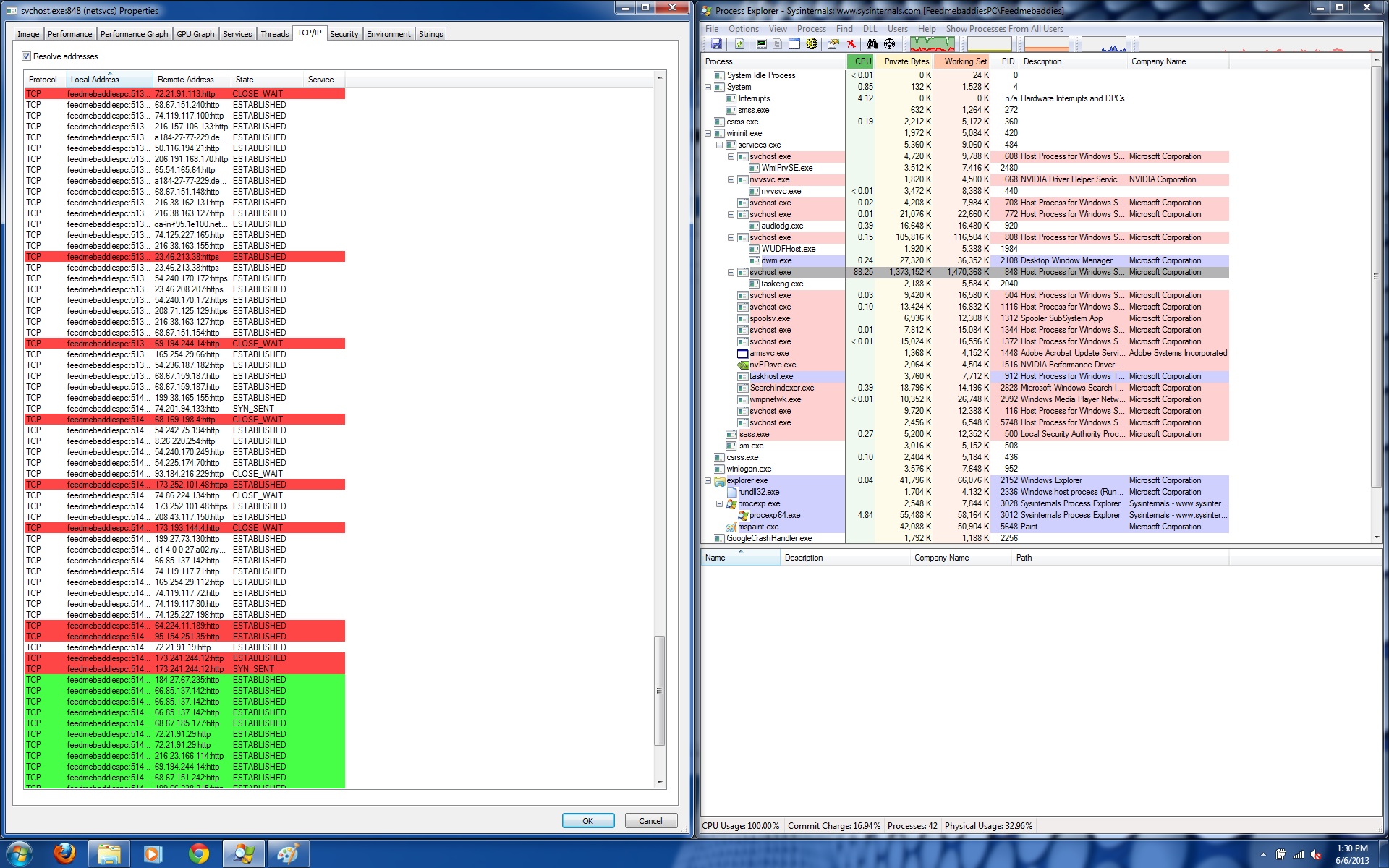
The audio streams are not being run by an audio application or an internet browser session, but instead a hijacked “svchost.exe” that’s using 88.25% CPU. If we take a look at its network communication we find that it’s establishing and closing over a hundred different connections at once. This is why the audio ads aren’t coherent and are basically just multiple advertisement streams all at once which makes for quite an annoying sound. You can give it a listen by clicking below.
[soundcloud url=”http://api.soundcloud.com/playlists/6977174″ params=”” width=” 100%” height=”300″ iframe=”true” /]
The motivation is for this virus, other than being very obnoxious, is that the hundreds of IP addresses being resolved from the PC will generate a tick on the visit counter and generate ad revenue.
To remove this sample is actually quite simple. Since this starts as soon as the computer starts if you take a look at the startup entries you should find something similar to this.
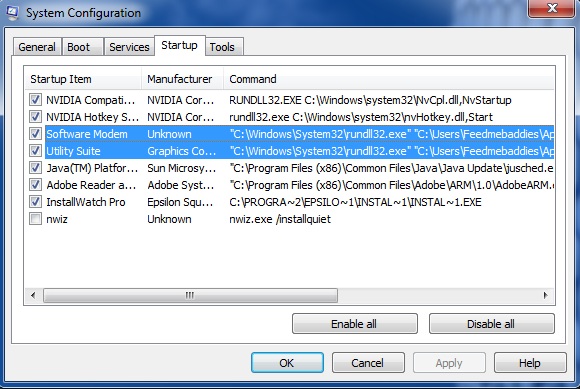
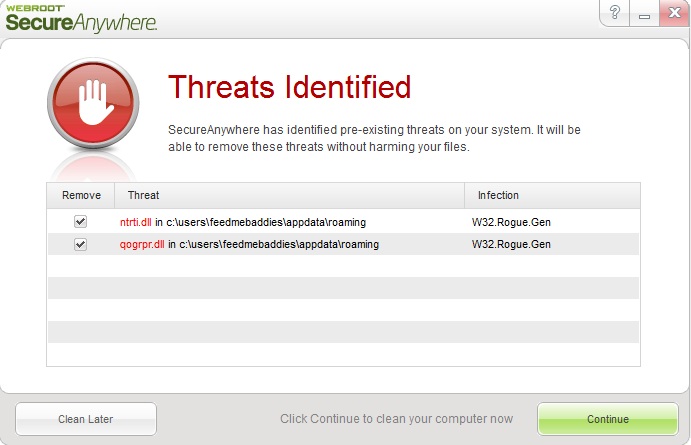
Software Modem and Utility Suite are the culprit. If you read the full command they are located in appdata and point to two randomly named DLLs called “qogrpr.dll” and “ntrti.dll” This is extremely suspicious.
All you need to do is delete the files in appdata and then remove the run keys from startup. The full registry key and directory location from are below.
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun]
“qogrpr”=””C:\Windows\System32\rundll32.exe” “C:\Users\”youruserfolder”\AppData\Roaming\qogrpr.dll”,GetGlobals”
“ntrti”=””C:\Windows\System32\rundll32.exe” “C:\Users\”youruserfolder”\AppData\Roaming\ntrti.dll”,NewMember”
As always, you can install Webroot SecureAnywhere and we’ll remove it with ease.
That’s it for this variant of the Audio ads. There are also other variants that use rootkits to infect the MBR. Please contact Webroot Support if additional assistance is needed in remediating this infection.