One of the most common myths regarding the emerging TDoS (Telephony Denial of Service) market segment, portrays a RBN (Russian Business Network) type of bulletproof infrastructure used to launch these attacks. The infrastructure’s speculated resilience is supposed to be acting as a foundation for the increase of TDoS services and products. Fact or fiction? Keep reading.
In this post, we’ll profile a SIP-based, API-supporting fake caller ID/SMS number supporting DIY service, and discuss its relevance in the overall increase in TDoS underground market propositions.
More details:
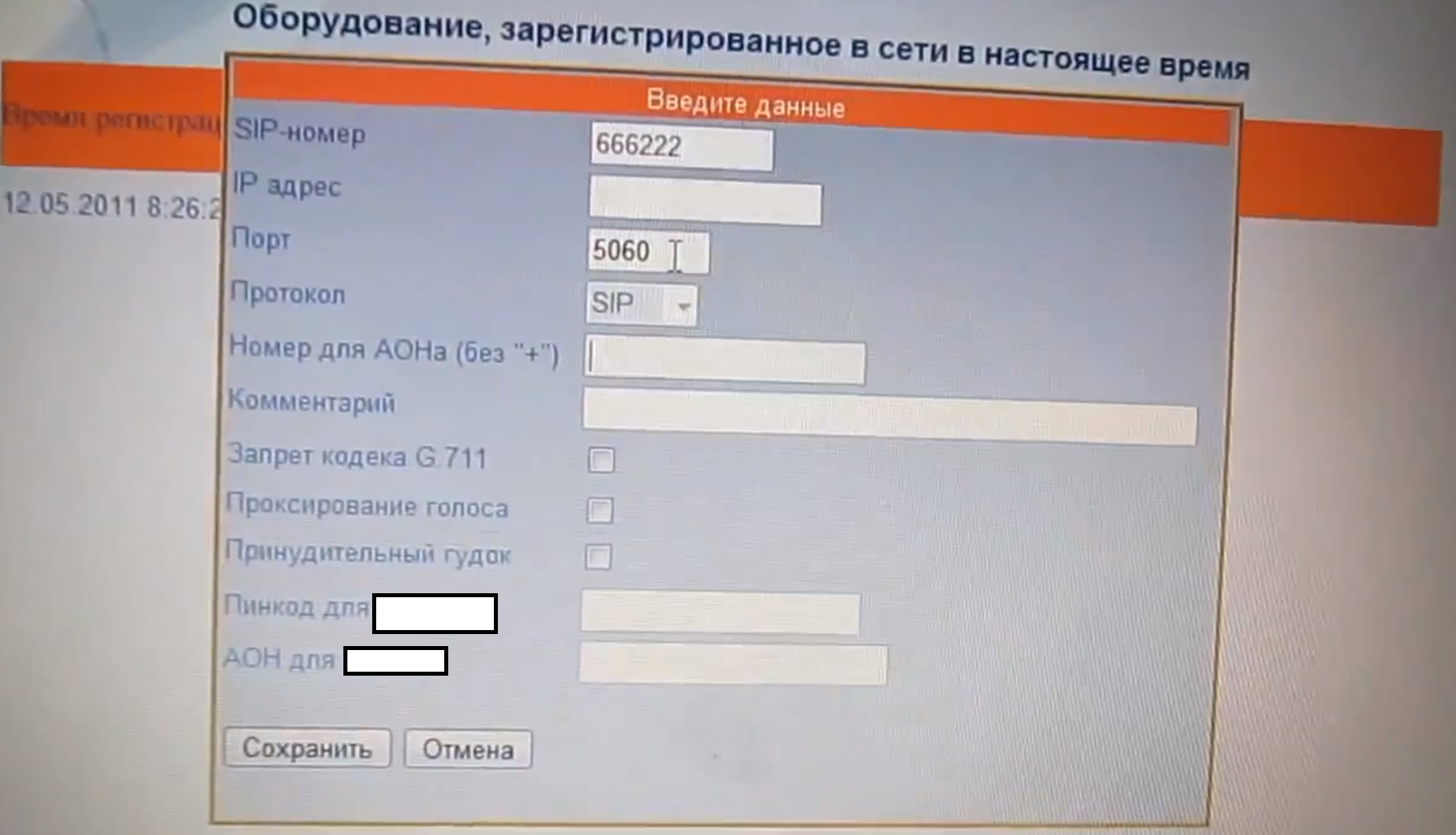
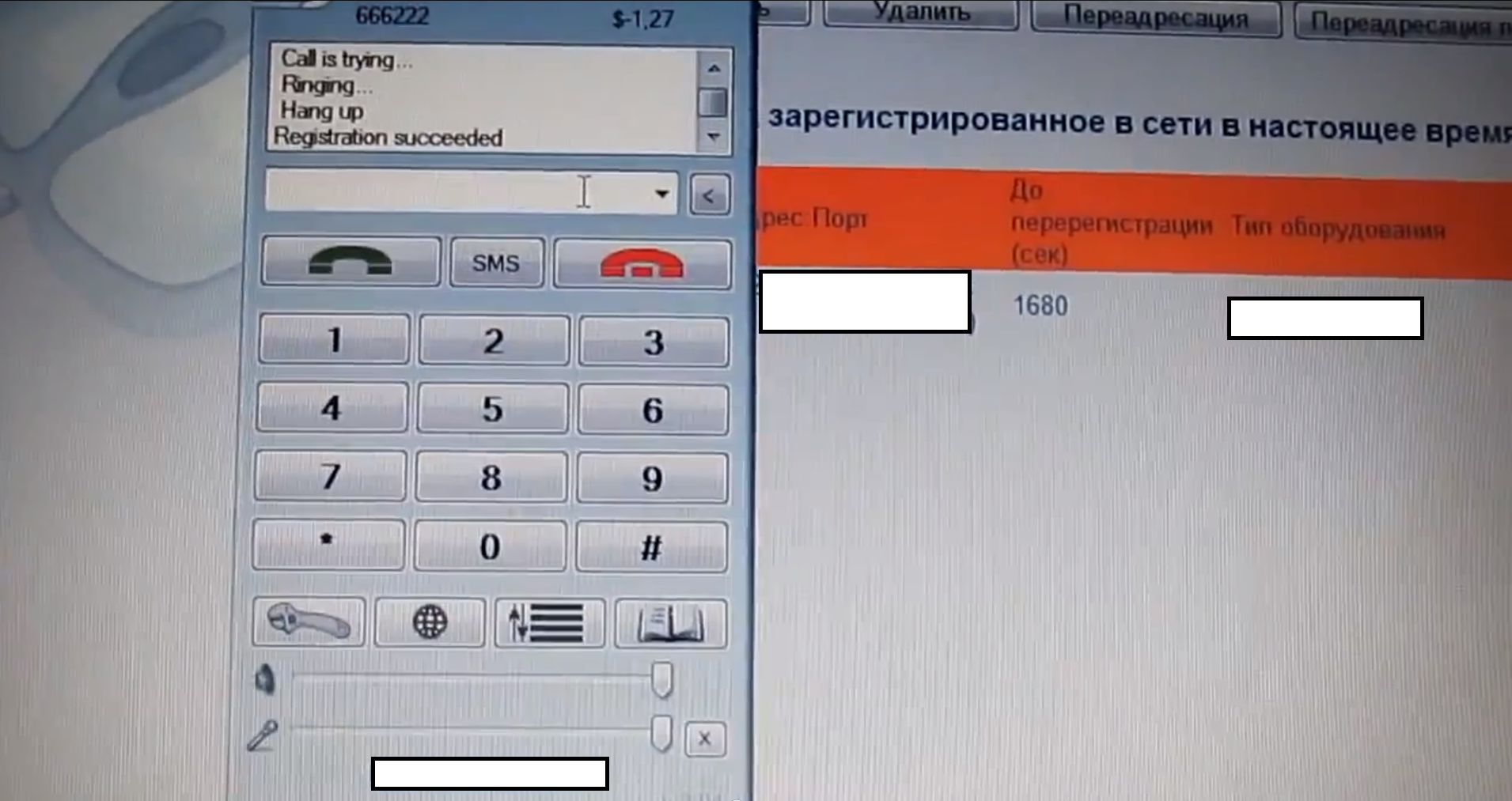
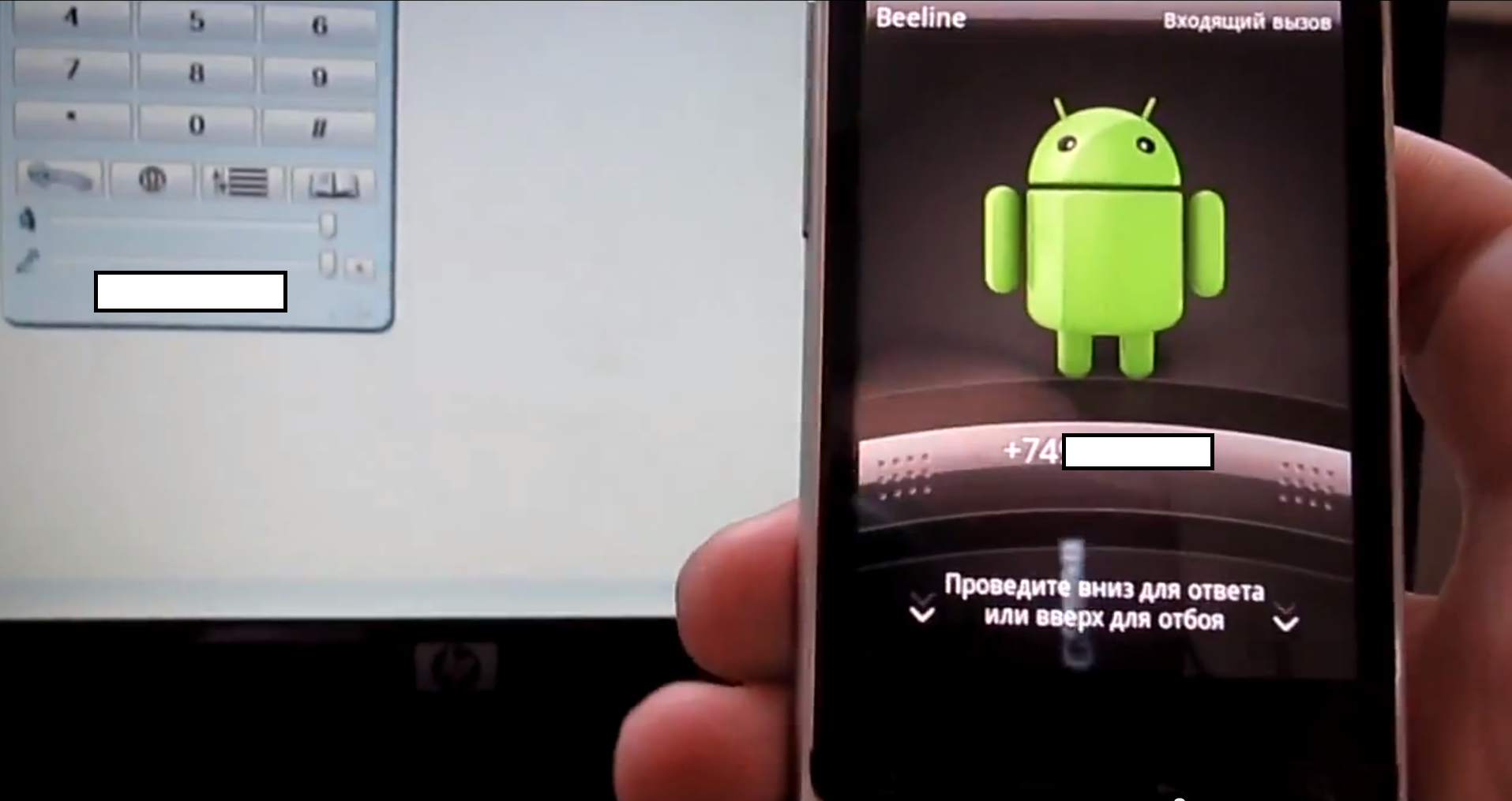
Sample screenshots of the service in action:

Although the featured screenshots offer a fake caller ID service verification on behalf of the cybercriminals operating the service — advertised publicly since 2011 — that’s just the tip of the iceberg, due to the standardized nature of SIP, as well as the availability of an API allowing virtually anyone to build custom TDoS (Telephony Denial of Service) attack tools while using their infrastructure.
What’s ultimately driving the rise of the TDoS (Telephony Denial of Service) underground market segment? Is it the existence of bulletproof infrastructure exclusively utilized for malicious and fraudulent purposes, or the systematic abuse of legitimate infrastructure in an attempt by the vendors of these services to blend with it in an attempt to make it harder to detect their activities?
Not surprisingly, based on our research, it’s currently a combination of both, with the abuse of legitimate services offered by SIP providers and mobile carriers, as well as the systematic introduction of bulletproof SIP infrastructure. We believe that due to the industry’s current ‘catch up mode’ in regard to this emerging DoS (Denial of Service) vector, cybercriminals will continue successfully launching these attacks, utilizing both legitimate and purely malicious infrastructure, to achieve their objectives.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.