We’ve just intercepted yet another campaign serving deceptive ads, this time targeting German-speaking users into downloading and installing the privacy-invading ‘FLV Player’ Potentially Unwanted Application (PUA), part of Somoto’s pay-per-install network.
More details:
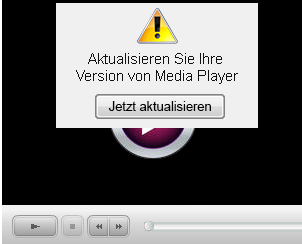
Sample screenshot of the actual rogue ad telling users that they should update their current media player:
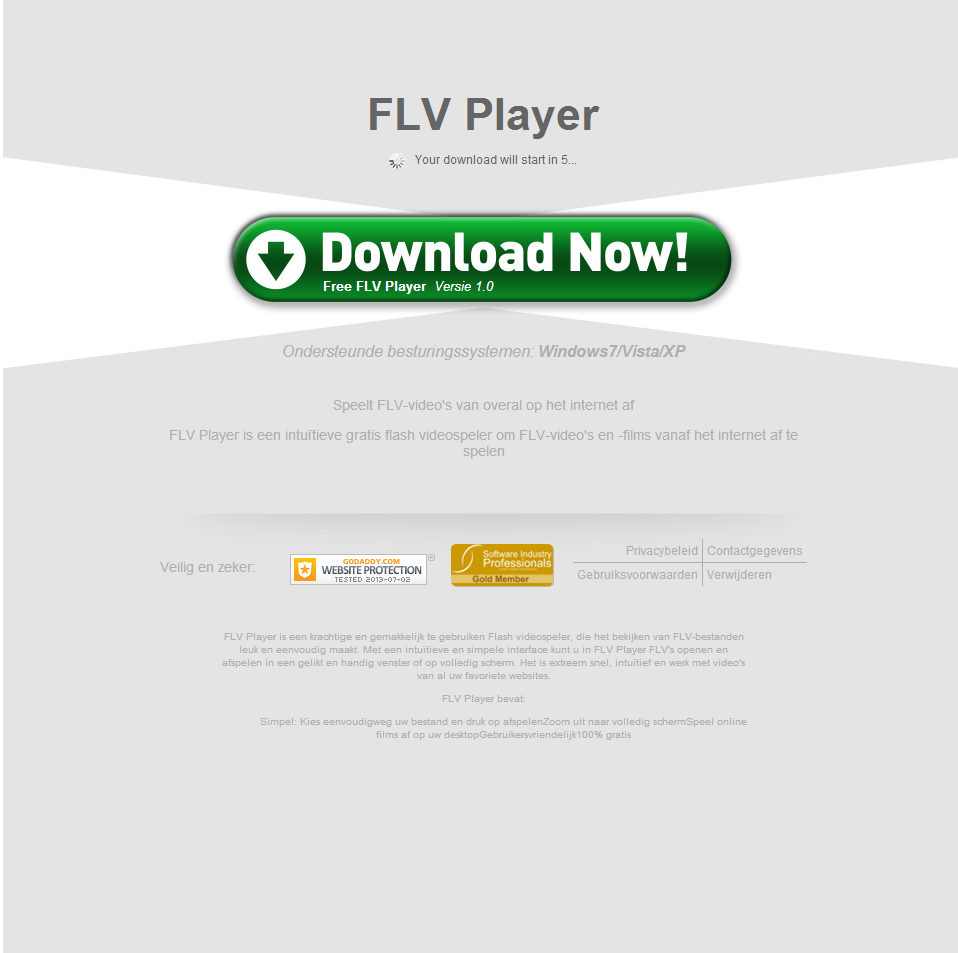
Sample screenshot of the landing page:
Detection rate for the PUA: flvplayersetup.exe – MD5: 9905e90b4ff276ec2869121c73f3f585 – detected by 9 out of 46 antivirus scanners as W32/SomotoBetterInstaller.A!Eldorado; Somoto BetterInstaller, BetterInstaller (fs).
Rogue domain name(landing/actual download location) reconnaissance:
softigloo.com – 78.138.105.151
static.bicdn.com – 78.138.97.8
Known to have responded to the same IP (78.138.105.151) are also the following domains and MD5s:
down1oads.com
download.softiglu.com
softigloo.com
softiglu.com
softingo.com
down1oads.com
downxsoft.com
softigloo.com
MD5: 02696da461918bd98324172130947d24
MD5: f2b968c975f27a4d2212c98ecb818912
MD5: b061e2a27452f74226d698e1b3e124bb
MD5: 2da8c25cd6b6f5466b27bd815a1479a6
MD5: 3967c2686efea20264bff333a935c7ba
MD5: 44b0d714486c230be83abf95a5e287ba
MD5: 3ee49800cc3c2ce74fa63e6174c81dff
MD5: f567b39c5f895dd49367ebb87ac071da
MD5: fbd7091a58119d2b5faeac129b27cb2b
MD5: b06882e68a5f7fbd0aff04e52c5e4594
MD5: 32de3ecdcb996cf736d5397a30a53c5a
MD5: f4fef07d24fd8945dbfe9fef0a1613ff
MD5: 236eb0c32b0cf3a9e169b05953228dc0
MD5: 0d2a33231e3ea4377daa9aba69badc07
MD5: a57bc4ee2447fed12459ac1cee627f80
MD5: 62df6881311ab1f0a409cf1c69c89b9c
MD5: 42f0d9fc97c213113b2b4d2b389cfe44
MD5: 122995fd94508909b75ed8c71994f22a
MD5: 438af7514b9e594dd158da10e70433ea
MD5: 7b8af212f537381085a1b3c5705c1b39
MD5: a3f59416f5df841195c9b16d90f648b8
MD5: d109a16eda33c2c28eb2d4ea9756f0f2
MD5: cef1c3188a510cba312db559866342c6
MD5: 47b8f328a8329a9ec587bdd068bf5de6
MD5: 905112ce1821326a82f18704a1383195
MD5: fc33ac0bf70c3474c42415ef278c853f
MD5: 59a4baebdc2ceb7319b63fee00ce90d0
MD5: cc40c65faa0af75998173c2fb0cfdba5
MD5: 724cff49a55ba9cf1e9b083bfb66a827
MD5: b8b3a545da1f2526b23cb2a6d03c7ae4
MD5: cf2dcb2e68004b57e1042f771d206840
MD5: aa2727dba6bc60f472d04c0aa8161747
MD5: 83c43f8544b73d0c055a31b47206dae9
MD5: bdefcb0c16a044bf11c703fc96cef444
MD5: 658015ae6b8d279dd692224c8e83385d
MD5: 3d1b822fde2521b87f987db58d3fb5b6
MD5: de41eb4f1fb34d581f33af9f0f9ef767
MD5: 30499440bf32193d0402b26832e1bcef
MD5: 5e923eb882a7c11ac478d536e57749d8
MD5: 5cf72716cba00cf3f4917edd84efca63
MD5: 74c5e06878c0078511aa7964f05f7e4b
MD5: 079f1b6dd153ef8929f50d4866ec001e
MD5: 21026ab5dbac341df3b9152ecfe665fd
MD5: 511a23b667be0bb47fd17bba2a814c2c
MD5: 78f14f83fe839f8cf51f6419665cf835
MD5: c07607eebbfd1984ad68939e45c2f084
MD5: c5c151614e64f38503e86550bd814c8c
MD5: 17e88f4a4ec08744bb7bc99ba44df8ec
MD5: 36d975016f264ef2a2126d6e382a8a08
MD5: 6e2721e8e13fb50d970de45b93563dbb
MD5: 070535bae755ec97dc0aecd3a08fac28
MD5: f2d70dff1b4df16d741d3cdea11cfb11
MD5: bafb2861ad15ad246c82dfa776a0f2ab
MD5: 28f6738ee180eda2f844e8321505f75e
MD5: 07d105b52ffa608d32cbc0cdacf0c107
MD5: 2acb0a5342cf9aa26800758337692e4a
MD5: ed8e756301a17b77e79ebb8831143c79
MD5: a021208fc741d8c2dd13007a4463ae0a
MD5: 1132e040bb84dc2f19a019def6b78c9d
MD5: 09b477692c95ba8fef4ee04ef8b5af2c
MD5: 156303a754a238d3629773057b05d26e
MD5: fa38b307d402ae7824b9d211f67ecbe2
Known to have responded to the same IP (78.138.105.151) are also the following domains and MD5s:
betterinstaller.com
bi.bisrv.com
bisrv.com
cdn.bicdn.com
download.betterinstaller.com
download.filebulldog.com
inno.bisrv.com
installer.betterinstaller.com
installer.filebulldog.com
logic.bijscode.com
nsis.bisrv.com
static.bicdn.com
static.bijscode.com
static.bisrv.com
static.frogdownload.com
MD5: 236eb0c32b0cf3a9e169b05953228dc0
MD5: f4dfc67d98ce534f67e9b1555712d789
MD5: ec2269d1ca28804a83d987669381dd49
MD5: 5afdab1e14d6766aa4bbce757dd5cd8e
MD5: c5fae0daace184a4de7213aaa536b97c
MD5: 07cb5b6d356e2d9be7ed61060be7bc8f
MD5: 105ea4b69b0974ad25d2a87b6f42257c
MD5: d5529feef9b2d16fe24713cbac281a87
MD5: 3ee49800cc3c2ce74fa63e6174c81dff
MD5: d5529feef9b2d16fe24713cbac281a87
MD5: 3ee49800cc3c2ce74fa63e6174c81dff
MD5: b061e2a27452f74226d698e1b3e124bb
MD5: 38df3d10d94676f6f69574cb4bec0c40
MD5: 3967c2686efea20264bff333a935c7ba
MD5: f5cc40041780eb4c9fc814888b7a4222
MD5: 9a2336760e4ea7afa1ec95ce60fb5702
MD5: 633504a15cb41cc9a17b59c6357e84dd
MD5: 1663cbfe586ea7ead04d0f66d6c5d5db
MD5: 0d2a33231e3ea4377daa9aba69badc07
MD5: 73b8d78c0fc21d6b76b6741ae4f8031c
MD5: f375353f47113765a519ad499c17b5f7
MD5: 02696da461918bd98324172130947d24
MD5: f2b968c975f27a4d2212c98ecb818912
MD5: c73f70ad2bdec056de74e5aee8b3f9da
MD5: 2da8c25cd6b6f5466b27bd815a1479a6
MD5: be411020d35a1508a14c4695982859e8
MD5: 032351e30163424f8ef45e4a21bcba21
MD5: 40547625a1941556030d9a8a13df3423
MD5: f4fef07d24fd8945dbfe9fef0a1613ff
MD5: 302dbd61a937073e71051caf5f63799b
MD5: b39cf9b308a89caa4782f36ebbd86388
MD5: 1685085dd967edbadc28e1ffaf2e8303
MD5: e34013c4cbb146f06fa9ac538d01cdf0
MD5: f9d32dc05a1218671fb900da5aab5f92
MD5: 0ee7c928b7f0576ccdaaa592f6610c40
MD5: 1c6254d3a61d2ce7b3c52b632e858257
MD5: 804be90d92af3a5f9b053d2c0b5fe62f
MD5: 4a2ce589f3874768f44963b4201172b7
MD5: fe3c757c7ec11436593d75886a8f9da8
MD5: e20dc648adb92cb3daae1da8dddea011
MD5: eb68731c0c6d8304baada4fc022451b3
MD5: 3b36c2a34b33ceb018a2f1712ee86feb
MD5: cd89f31c76086b85055e8651ce937a41
MD5: a58078763004a647208feded509295e0
MD5: 6599345307ddfb9d0cbff4d492527e7e
MD5: 3ca6524579ea8c98581d1a8bcbeeeb11
MD5: c202c12afaa1e0868e56b45c6bb95ffe
MD5: d2840f5995b8354cea125c34c8ddd342
MD5: fa169fbf4483defecb52c93d514becfc
MD5: c737bf87d4a814387fe8e30d89177f95
MD5: 1d8fbd1c2687e89e376ea59f9b48aeb1
MD5: 2de265f9f1c0acd3a0b6e412ff9c6154
MD5: f617e93309d81e1c5a5a061ce6447ce3
MD5: 9c9233d298086696bfa4cd3713586bc9
MD5: 5801e93954b2d5a99aaecc8834911fbd
MD5: 9d0db90c23606bd0b73e37b2c680954a
MD5: ff37c8c76052377fd06d454817df089b
MD5: 66f48eb6f0ed289825f23e8028702f5f
MD5: 8b6d59e71b8e408b24221ed1daf42e56
MD5: a75f18253d574ecf521cd9d60e123bb7
MD5: e0b2a6b7d09dc08e09d30972046a875f
MD5: 52ff95d7a160ff7d11e26cc6bda6791c
MD5: 9963c22d3276caefeb5ba68f485a7dd2
MD5: 7e508cf82114f1b7a41ae4782ea83cdd
MD5: 7f6b953cc12bc0ff8a7524b1f1e9d04d
MD5: 1ff7f24c17becad78c4d289e251f8a7e
Despite the fact that our sensors picked up a campaign targeting German users through rogue ads, we’re also aware of multiple cases where malware-infected hosts, belonging to different botnets, are being monetized through Somoto’s pay-per-install affiliate network model.
Sample screenshot of the Somoto toolbar in action:
Sample screenshot of the Somoto pey-per-install network:
Users are advised to avoid installing the rogue ‘FLV Player’.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








i have this problem now,how can i remove it?