Thanks to the fact that users not only continue to use weak passwords, but also, re-use them across multiple Web properties, brute-forcing continues to be an effective tactic in the arsenal of every cybercriminal. With more malicious underground market releases continuing to utilize this technique in an attempt to empower potential cybercriminals with the necessary tools to achieve their objectives, several questions worth discussing emerge in the broader context of trends and fads within the cybercrime ecosystem.
What’s the current state of the brute-forcing attack concept? Is it still a relevant attack technique, or have cybercriminals already found more efficient, evasive and effective tactics to compromise as many Web sites/servers as possible? Let’s discuss the relevance of the attack concept in 2013, by profiling a recently released WordPress/Joomla brute-forcing and account verification tool.
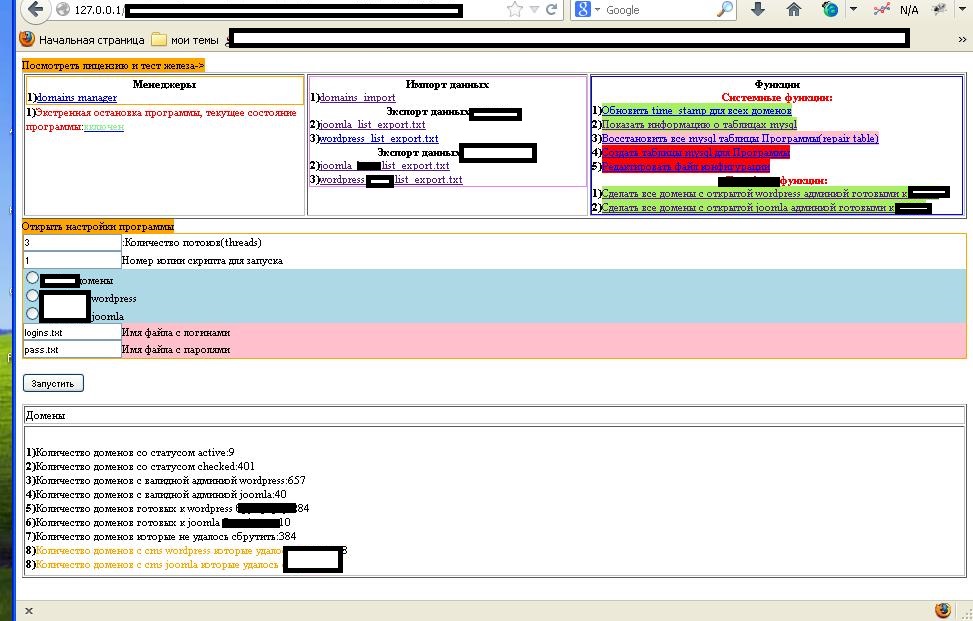
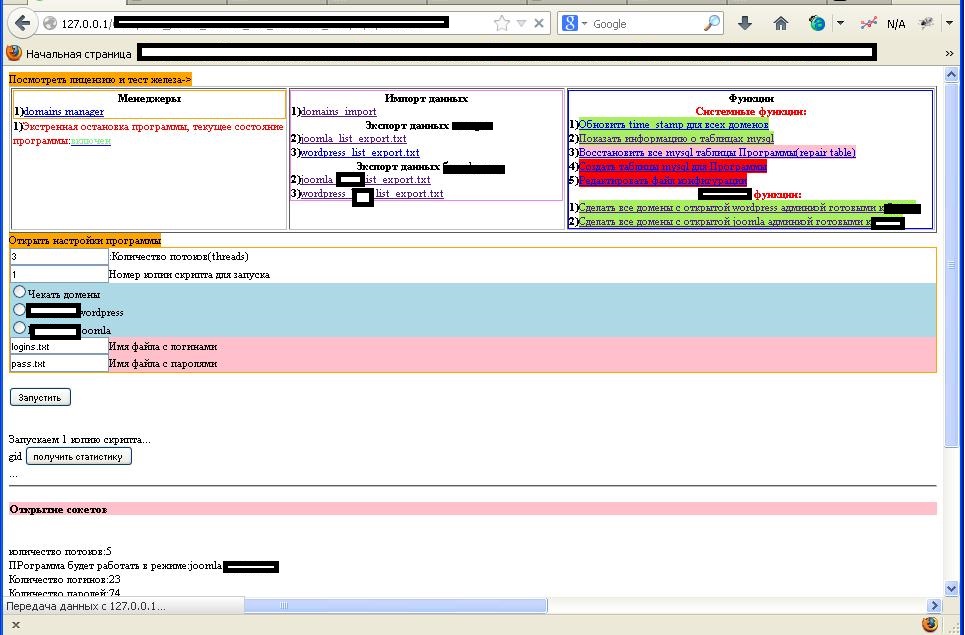
More details:
Sample screenshots of the Web-based tool in action:
The Web-based tool not only verifies the validity of the WordPress/Joomla sites, but also has the capacity to launch brute-forcing attacks against them once its user loads a list of user names and popular passwords. According to its author, it can support 200 simultaneous connection attempts and is capable of testing 50 to 80 password combinations per second.
This tool is just the tip of the iceberg on an ever-green market segment within the cybercrime ecosystem that continues to push new releases capable of launching brute-forcing attacks against any given Web property. Despite this fact, it’s worth emphasizing on the actual relevance of these tools in 2013, taking into consideration the following factors:
- CAPTCHAs slow down the brute-forcing process and make it cost-ineffective – since the tool profiled in this post doesn’t support proxies (which are basically malware-infected hosts), it means that there’s a high probability that the brute-forcing approach will trigger a CAPTCHA challenge, meaning that the cybercriminal using it would now have to outsource the CAPTCHA solving process, increasing the cost of launching the attack. As far as those tools which support proxies are concerned, a potential cybercriminal will once again end up in a situation of increased operational costs, due to the fact that he’d have to purchase the high priced clean proxies, compared to a situation where he’d be syndicating proxies that are getting abused by virtually anyone due to their free nature
- major Web properties increasingly enforce a ‘strong password’ policy to their new/current users, introduce two-factor authentication – in a practice that’s signalling a ‘wake up to reality’ moment, in recent years, major Web properties started either enforcing a ‘strong password’ policy, or assessing the strength of the password through ‘password strength meters’ in an attempt to alert their users to the potential security threats due to their choice. Both of these practices can significantly decrease the effectiveness of an ongoing brute-forcing attack.
- compromised WordPress/Joomla accounting data as a service has been available for years – while not exclusively available for WordPress/Joomla platforms, due to the nature of these ‘logs on demand’ type of services, virtually anyone can order WordPress/Joomla accounting data, with the cybercriminal behind the service, basically data mining his botnet’s infected population. The availability of this service, has resulted in a short TTM (Time-to-Market) initial campaign launching phases, due to the fact that a potential cybercriminal would no longer need to figure out a way to set up the foundation for a successful campaign.
- efficient exploitation through search engines’ reconnaissance is a daily routine – we’ve already emphasized on the existence of this practice, in our previous ‘New version of DIY Google Dorks based mass website hacking tool spotted in the wild‘ post, and highlighted the commercial availability of these easy to use and highly efficient automatic Web site exploitation tools.
- active exploitation of server farms continues to take place – yet another factor that we believe is contributing to the overall demise of ‘brute-forcing your way in’ type of attack tactics, is the emergence of sophisticated platforms attempting to infect as many Web sites as possible, through a direct server farm compromise.
So is this the end of ‘brute-forcing your way in’ as a tactic? Not necessarily. It’s just that thanks to the dynamics of the cybercrime ecosystem, the tactic is getting largely replaced by other, more efficient, evasive and cost-effective approaches to compromise as many Web sites as possible.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Reblogged this on Simple PHP Blog.