Malware-infected hosts with clean IP reputation have always been a desirable underground market item. On the majority of occasions, they will either be abused as distribution/infection vector, used as cash cows, or as ‘stepping stones’, risk-forwarding the responsibility, and distorting the attribution process, as well as adding an additional OPSEC (Operational Security) layer to the campaign of the malicious attacker.
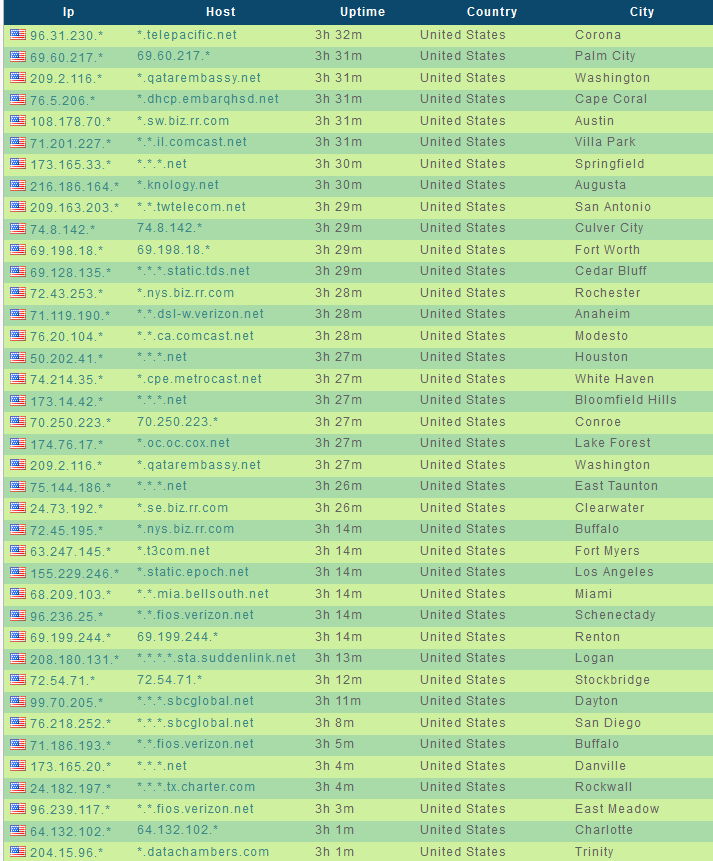
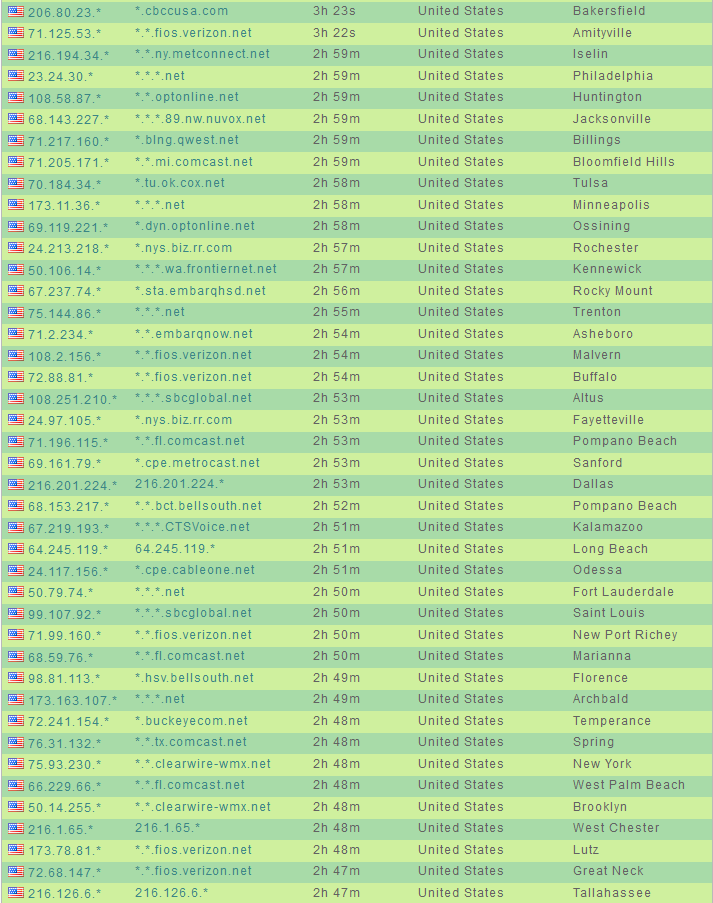
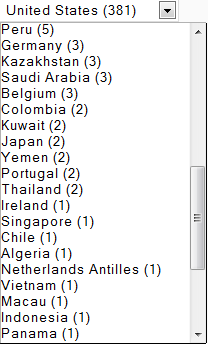
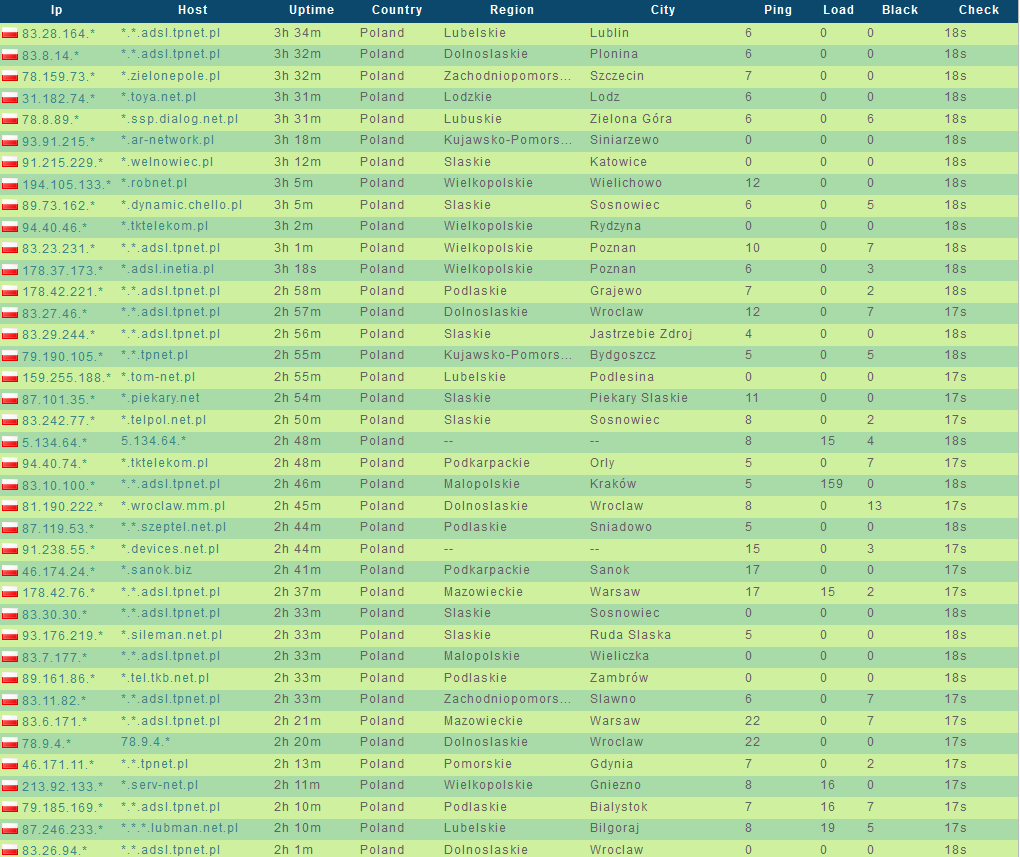
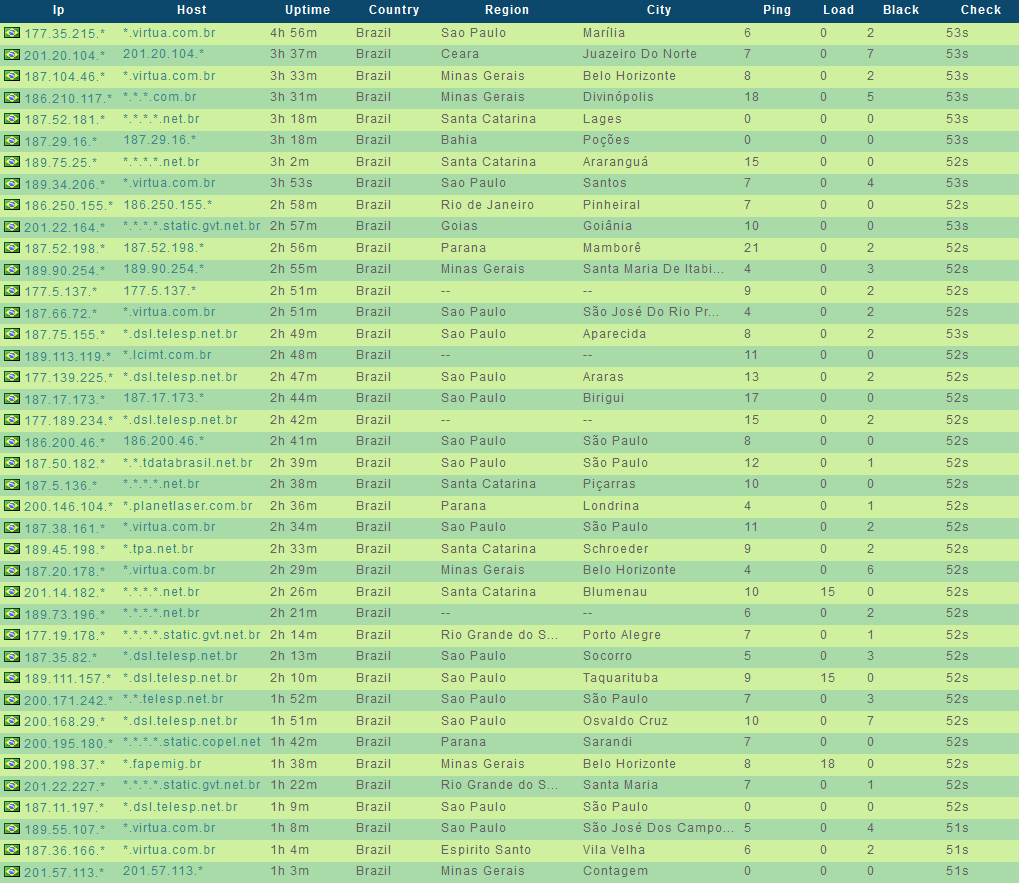
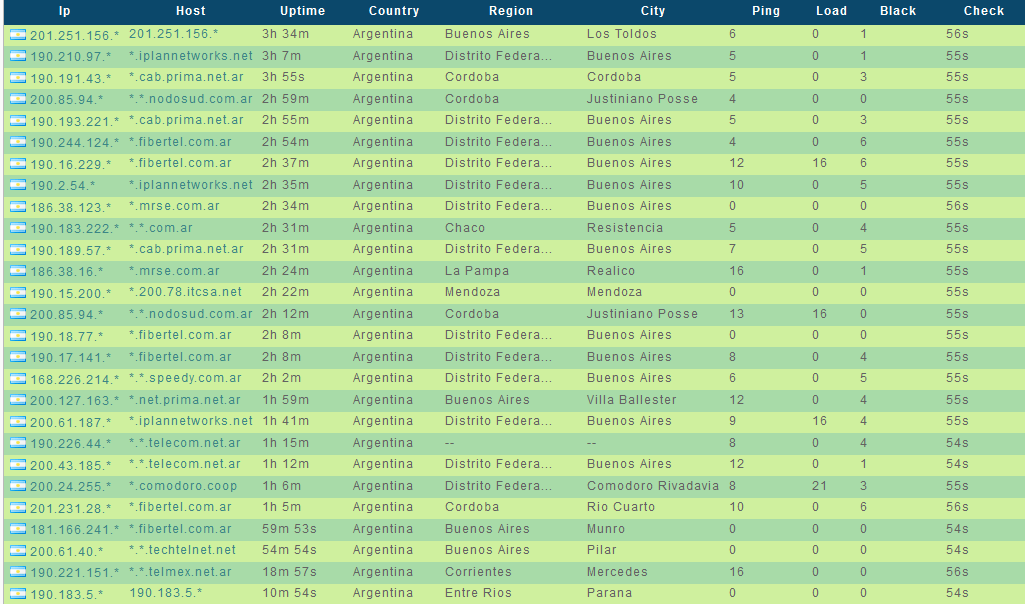
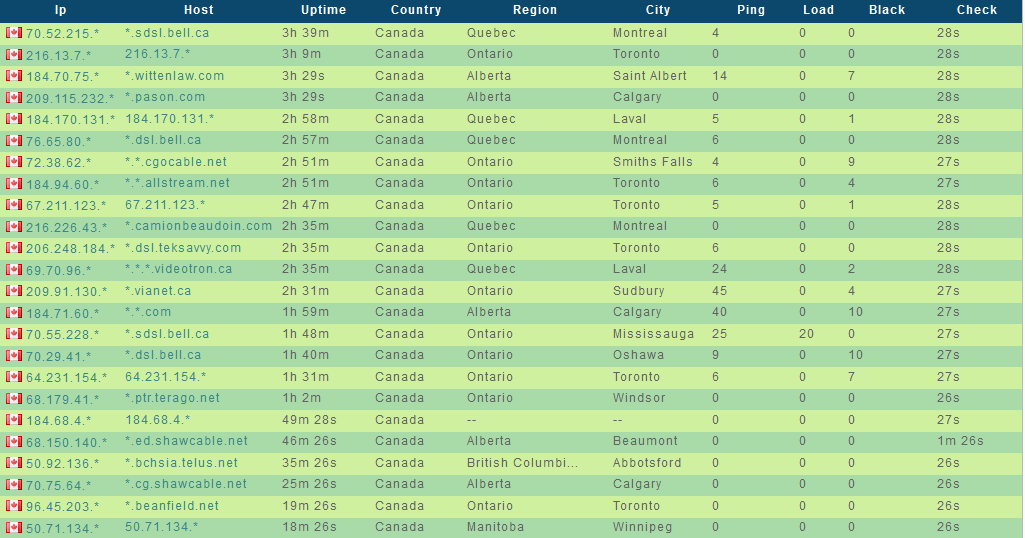
A newly launched ‘malware-infected hosts as stepping stones’ service, is offering access to Socks5-enabled malware hosts, located primarily in the United States, allowing virtually anyone to route their fraudulent/malicious traffic through these hosts.
More details:
Sample screenshots listing the ‘infected-hosts inventory’ of the service:
The service is also offering a Jabber based bot for interacting with it. The prices are as follows:
- 150 socks 5 enabled hosts for 1 month – $25
- 300 socks 5 enabled hosts for 1 month – $40
- 600 socks 5 enabled hosts for 1 month – $50
- 900 socks 5 enabled hosts for 1 month – $60
- 1500 socks 5 enabled hosts for 1 month – $90
The concept of using malware-infected hosts as stepping stones has been around for years, empowering virtually everyone to engineer political/cyber tensions between multiple nations, taking into consideration the fact that any given attack pattern can be made to look like as if it’s originating from a specific country, thanks to the commercial availability of these services.
We expect to continue observing a steady supply of such services, in particular the inevitable re-emergence of the ‘on demand’ market concept, allowing the easy acquisition of Socks 5 enabled hosts in any given country that’s requested by the customer.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.