Whether it’s abusing the ‘Long Tail’ of the Web by systematically and efficiently exploiting tens of thousands of legitimate Web sites, or the quest to compromise few, but high-trafficked, high page rank empowered Web sites, compromised shell accounts are an inseparable part of the cybercrime ecosystem.
Aiming to fill in a niche in the market segment for compromised/hacked shells, a newly launched service is offering a self-service type of underground market proposition, whose inventory is currently listing over 6000 compromised/hacked shells internationally.
More details:
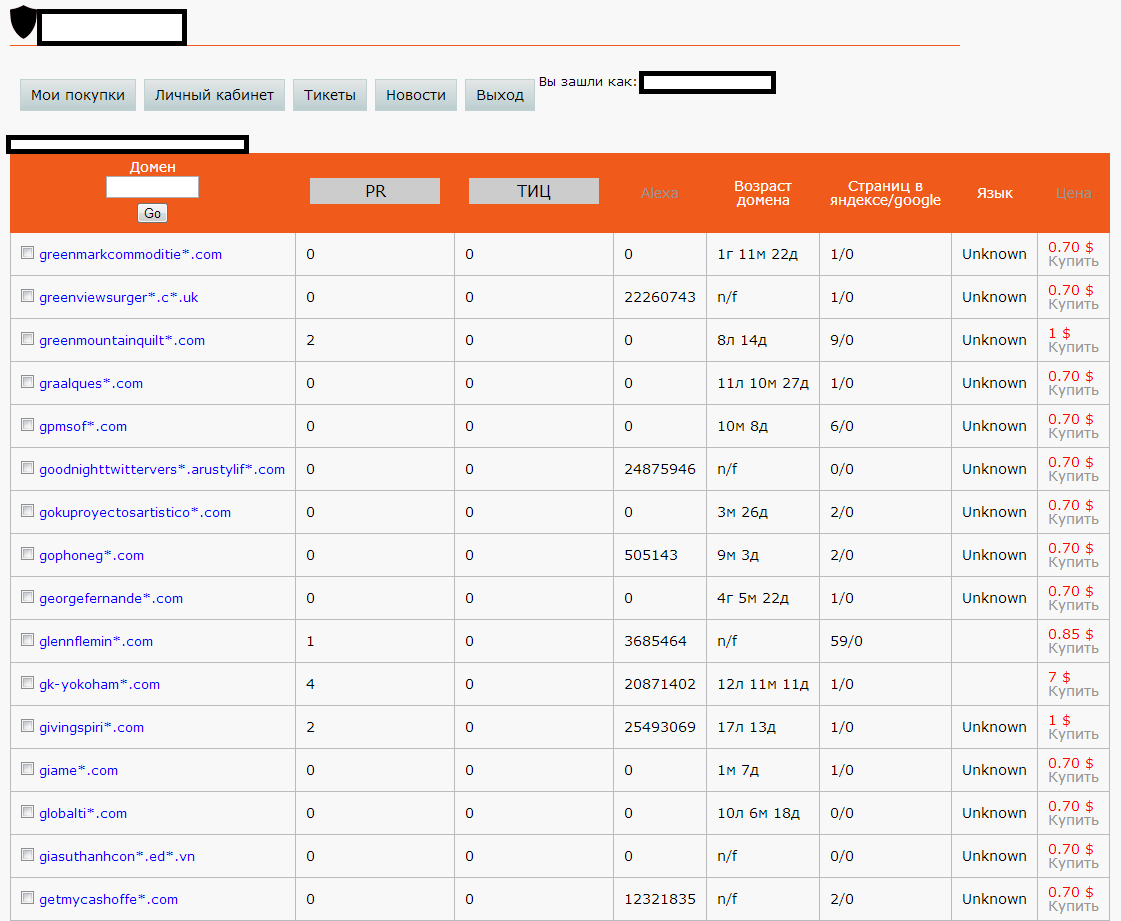
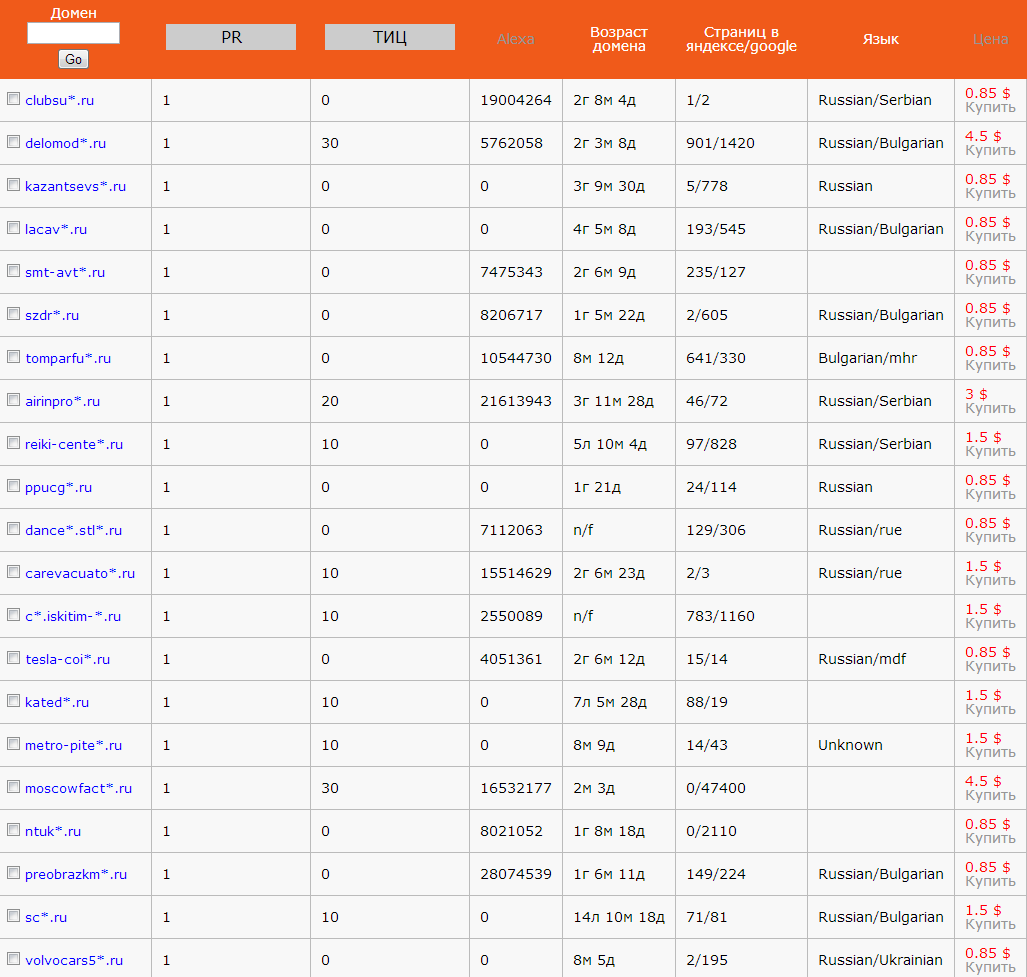
Sample screenshots of the ‘inventory’ of the service:
Potential customers are allowed to search by a specific TLD, as well as the option to filter the search results based on the price, page rank, ‘age’ of the domain, Alexa ranking, language, and number of pages indexed by Google.
Throughout the last couple of years, multi-tasking cybercriminals started abusing access to these compromised sites in multiple fraudulent/purely malicious ways. From blackhat SEO (search engine optimization), to the direct hosting of malware and phishing pages on the compromised sites, the vibrant underground market segment for compromised shells continues to facilitate the (commercial) exchange of access to compromised Web sites. Due to the overall availability of DIY botnet generating tools, we expect that this market segment will continue flourishing, with cybercriminals finding more ‘creative’ and customer-oriented ‘solutions’ to automate the buying/selling process.
Consider going through the following posts if you’re interested in knowing more about the monetization techniques observed over the last couple of years, in terms of compromised shells as means for abusing access to a particular Web site:
- p0rn.gov – The Ongoing Blackhat SEO Operation
- Monetizing Web Site Defacements
- Underground Multitasking in Action
- Compromised Sites Serving Malware and Spam
- Web Site Defacement Groups Going Phishing
- Blackhat SEO Campaign at The Millennium Challenge Corporation
To find more about Dancho Danchev, follow him on Twitter.






there’s some one out there claiming to be netflix saying that your account was stoped or closed and they need your ss no. credit card and address to reopen it do not give them it.
Superb, what a blog it is! This web site presents useful
data to us, keep it up.
I love what you guys are up too. Such clever work and reporting!
Keep up the terrific works guys I’ve included you guys to my personal blogroll.
Hey Josh, I’m wondering could you maybe share the name of this “hacked shell” marketplace, it appears client the dentist has been featured on it, and need to take the necessary measures. Please let me know, my email is madeleine8686@hotmail.com.
OH and also the comment above me appear to be SPAM ( hint: Kitchen Worktops ) 🙂
Hi Madeleine,
To be completely honest, this article was written over 3 years ago by someone who is no longer affiliated with Webroot, so I’m not exactly sure who here I could ask that would know the name exactly of the site in question. Sorry about that 🙁 I would advise contacting your Web Hoster directly if you believe there is any foul play going on.
Oh, and thanks for notifying me of the spam comment ?
Regards,
Josh P.
Social Media Coordinator