We’ve just intercepted yet another rogue ad campaign, attempting to trick users into installing the EzDownloaderpro PUA (Potentially Unwanted Application). Primarily relying on catchy “Play Now, Download Now” banners, the visual social engineering tactic of this campaign is similar to other PUA related campaigns we’ve previously profiled. Let’s take a look at this new rogue ad campaign, and provide relevant threat intelligence on the infrastructure behind it.
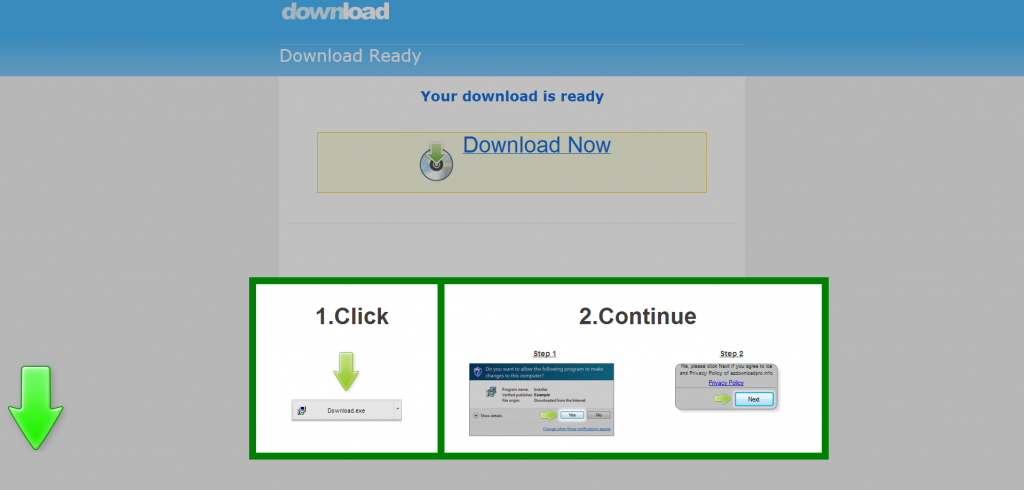
Sample screenshot of the landing page:
Landing URL: lp.ezdownloadpro.info/sspcQA/ssa/ – 46.165.228.246
Domain name reconnaissance of the redirectors:
superfilesdocumentsy.asia/v944/?a=1 – 141.101.117.252; 141.101.116.252
applicationscenterforally.asia/v944/?INm – 108.162.197.34; 108.162.196.34
op.applicationscenterforally.asia/sspcQA/ssa/
Known to have responded to the same IP (46.165.228.246), are also the following domains:
amu.downurfiles.info
downloadkeeper.info
driveridentifier-download.com
ezdownloadpro.info
iframe.applicationsforentirey.asia
iframe.applicationsforeveryy.asia
iframe.filesaredirecty.asia
iframe.filesareonliney.asia
iframe.superfilesdatay.asia
lp.ezdownloadpro.info
lp.livetrafficall.info
op.alllinuxapplicationsy.asia
op.applicationsforcompletey.asia
op.applicationsforentirey.asia
op.applicationsforeveryy.asia
op.applicationsgroupforally.asia
op.bestfilesarey.asia
op.bestfilesdatay.asia
op.documentsguidey.asia
op.documentssitey.asia
Known to have responsded to (141.101.117.252) are also the following domains:
2upl.com
amu.domainforcompany.info
andyrohr.com
bookmarkspiral.com
filecm.net
hackstore.net
happysky.heartbrea.kr
icephoenixbot.com
krazywap.ws
octavis.net
Malicious MD5s known to have been downloaded from the same IP (141.101.117.252):
MD5: fd4195ef1af7fb49a673633ed57b87ab
MD5: c0d9713acfc46c2a466a9de77292636d
MD5: d3119ed48cb5896d41aeae4b51f2667a
MD5: c6799f5425fbe038778c4c4a22b35a41
MD5: 840fa1e6c0f81f6da1a347ecb3b2db2e
MD5: c27d4537d24aa55df9837479da2ae111
MD5: c77fc69c7b96c53ce762b87c98831327
MD5: dce1c89d7a267b2a4ae925b5a387e5cd
MD5: a868964e1fe66e4a7638f46ba7844b52
MD5: 2acc54f86694e8d7674e8e1afff86aa1
MD5: 5f078de83a9ce3ee2d9d2fe174cd234c
MD5: 0426e6c1fe2aa8681c683428bb3d2dd7
MD5: efcd92d3be23e624bca2db8515f0df20
MD5: 30ac6dd3290ab3c9281e81c2cba2097e
MD5: 9b35dcacd42e6ba1c596a8bc0425d646
Known to have responded to the same IP (108.162.197.34) are also the following domains:
4agent.info
advancedchirocenter.com
albertomolteni.altervista.org
applicationscenterforally.asia
asoiaf.westeros.org
br.singlesfind.us
buker.ru
chaochui88.com
client.ferocitybooter.net
habbokekos.net
hentaimate.com
horny-locals.com
img.b2bage.com
onvideogames.net
op.applicationscenterforally.asia
papermashup.com
pdiva.ro
pinoyhideout.com.ph
prestamosdinerolosangeles.com
sdx.cc
The following MD5 is also known to have been downloaded from the same IP (108.162.197.34):
MD5: bc44e23e46fa4c3e73413c130d4f2018
Detection rate for the sample ‘pushed’ by the rogue Download page: MD5: e8c9c2db3514f375f74b60cb9dfcd4ef – detected by 12 out of 47 antivirus scanners as PUP.Optional.InstalleRex; Installerex/WebPick (fs)
Once executed, the sample phones back to:
r1.stylezip.info – 198.7.61.118
c1.stylezip.info – 198.7.61.118
i1.stylezip.info – 198.7.61.118
Known to have responded to the same IP (198.7.61.118) are also the following domains:
c1.storebox1.info
c1.stylezip.info
c1.yourfilesdatak.asia
c2.storebox1.info
c2.stylemy.info
creditzipmy.us
downloads-fast.info
downloads4u.info
i1.storebox1.info
i1.stylezip.info
i1.yourfilesdatak.asia
nlstorage.info
r1.storebox1.info
r1.stylezip.info
r2.storebox1.info
r2.stylemy.info
storagenl.info
storebox1.info
storebox3.info
stylemy.info
The following MD5s are also known to have phoned back to the same IP (198.7.61.118) over the past 24 hours
MD5: df0961738c4f5848673f2c73fe9c7e4f
MD5: 69b6c2491627d41e6e2291eafd4b4942
MD5: 03c068aef9d8e9902c32f57142460402
MD5: 530a72084a90b2d97ee7eb6e5893cb1c
MD5: dc367e6991b56f1470b742b94854997d
MD5: cb86d60a248dd0d61d07840513a92b76
MD5: cacd889e777031adbdebd4f9a04fedb8
MD5: 2529463456de5e69d315842a322c4342
MD5: 7108933a95f91e2b0c094c259e4fbdbd
MD5: f35bf9fb0a6eaa3b256e9454f334719a
MD5: 330c40c3bf6b55f8cd425d03e2b4f157
MD5: c8a835831bb9ae1c5f7b335af6adf4f7
MD5: 12cab1cc907765bf141233608fa1ded7
MD5: 4dad0b23f4e7a133aa867df9d6adf3dd
Detection rate for the original EzDownloadpro executable: MD5: 292b53b745e3fc4af79924a3c11fcff0 – detected by 5 out of 48 antivirus scanners as Win32:InstalleRex-U [PUP]; MalSign.Skodna.Pick; PUP.Optional.EZDownloader.A
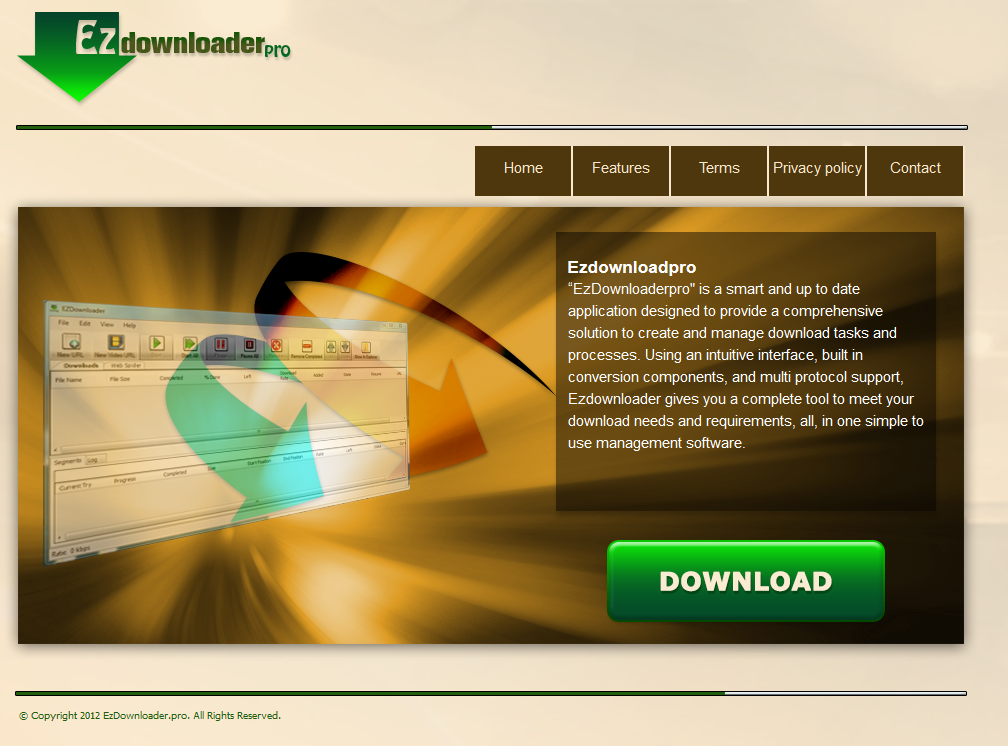
Sample screenshot of EzDownloadpro’s official Web site:
Unique PUA MD5s served based on multiple requests to the same URL (applicationscenterforally.asia/v944/?INm):
MD5: 0e570830dc3b1b8bad9689ed6a310654
MD5: d4bfbf9f28c81386bfb4b68b8f9b76f1
MD5: 3bb72e9c5eefce176ef6dddea858ef82
MD5: 7985860dc060792ba77e06f312739b79
MD5: 4b829aa6df0904bc0aba7652a73ec71c
MD5: 335bca4c2c3f4c980b4c485be4e13a00
MD5: c400bf0affbb376298fb93e5b8aacf59
MD5: 9244841ab24c8769438f22c0b5c2c053
MD5: 9ae15b4efd424fb7640e9066d0abfe1a
MD5: 20d83dd867bedf1f03ccdc0b5b8d720f
Webroot SecureAnywhere users are proactively protected from these threats.