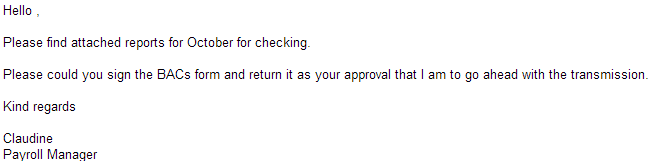
Have you received a casual-sounding email enticing you into signing a Billing Address Code (BAC) form for October, in order for the Payroll Manager to proceed with the transaction? Based on our statistics, tens of thousands of users received these malicious spam emails over the last 24 hours, with the cybercriminal(s) behind them clearly interested in expanding the size of their botnet through good old fashioned ‘casual social engineering’ campaigns.
Sample screenshot of the spamvertised email:
Detection rate for the spamvertised malicious attachment: MD5: 36a685cf1436530686d1967b4a9d6680 – detected by 20 out of 46 antivirus scanners as Win32/TrojanDownloader.Waski.A.
Once executed, the sample starts listening on ports 7442 and 1666.
It then creates the following Mutexes on the affected hosts:
Local\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local\{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Global\{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global\{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global\{9D48A1E2-9183-66A5-11EB-B06D3016937F}
Global\{9D48A1E2-9183-66A5-75EA-B06D5417937F}
Global\{9D48A1E2-9183-66A5-4DE9-B06D6C14937F}
Global\{9D48A1E2-9183-66A5-65E9-B06D4414937F}
Global\{9D48A1E2-9183-66A5-89E9-B06DA814937F}
Global\{9D48A1E2-9183-66A5-BDE9-B06D9C14937F}
Global\{9D48A1E2-9183-66A5-51E8-B06D7015937F}
Global\{9D48A1E2-9183-66A5-81E8-B06DA015937F}
Global\{9D48A1E2-9183-66A5-FDE8-B06DDC15937F}
Global\{9D48A1E2-9183-66A5-0DEF-B06D2C12937F}
Global\{9D48A1E2-9183-66A5-5DEF-B06D7C12937F}
Global\{9D48A1E2-9183-66A5-95EE-B06DB413937F}
Global\{9D48A1E2-9183-66A5-F1EE-B06DD013937F}
Global\{9D48A1E2-9183-66A5-89EB-B06DA816937F}
Global\{9D48A1E2-9183-66A5-F9EF-B06DD812937F}
Global\{9D48A1E2-9183-66A5-E5EF-B06DC412937F}
Global\{9D48A1E2-9183-66A5-0DEE-B06D2C13937F}
Global\{9D48A1E2-9183-66A5-09ED-B06D2810937F}
Global\{9D48A1E2-9183-66A5-51EF-B06D7012937F}
Global\{9D48A1E2-9183-66A5-35EC-B06D1411937F}
Global\{9D48A1E2-9183-66A5-A9E8-B06D8815937F}
Global\{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global\{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
Drops the following MD5s: MD5: cf8ab39c0a2561eb9df2c22496d20b3b; MD5: 75fe668007e66601724af592f8ca8985; MD5: 6abdc5f7f9599e3971af4202cf4ed4da.
And phones back to the following C&C servers:
offensivejokescolin.com – 38.102.226.253
85.100.41.9
113.161.95.98
172.245.217.122
93.177.152.17
114.24.192.181
63.227.34.28
76.70.9.123
206.190.252.6
60.244.87.31
70.27.195.251
217.36.122.144
173.239.143.42
86.135.144.6
69.95.46.22
85.24.208.124
86.147.226.12
79.129.27.234
94.64.239.197
58.252.57.193
194.250.81.234
62.23.247.20
75.99.113.250
82.91.203.169
178.23.32.115
85.206.22.117
31.192.48.109
187.188.136.31
178.192.71.93
213.96.69.3
The following malicious MD5s are also known to have phoned back to the same C&C servers:
MD5: 3752b2f92671cd051a77b04fd2fed383
MD5: 6bafe2fc65cf34ae6f103121d9325416
MD5: 4ae6a46a228da040fe25db0f419ae727
MD5: ed52d9f9fcc60d12166905e359c99020
MD5: 74e5acef47b9c57c7756cf130e8d4805
MD5: 1888be386f701199b282840cc0c5354f
MD5: 1b2590ee13cf6bda134a162708f8270a
MD5: adb1e09a26a6b22090b23432f0547ba3
MD5: 9b57ac8d44cede55be2079a4b400fffd
MD5: b1e332efb4e83189c7f5e84bc93e205b
MD5: 6c67f2add5a6eacb4c69f9efdbbb8cde
MD5: e65c0fd804992ea7e246f2385e32a0e1
MD5: bba80e9fabb476830d5216f1fa264489
MD5: 4dfa5221aae9945989fd815342d19c12
MD5: 49969b7e553ee03707f1e3ef333c2406
MD5: 86680fde2ef1ab2681262d39369999e8
MD5: 8b45bf7f9f4104c1e15cca8eb7f80581
MD5: c7d1a47b80f7910a03db8fa9791d2aec
MD5: b899ba5037db4babda49603603912bb9
MD5: d3cd3c07a4f82ed30bbc0af597f5391a
MD5: a6cb214dc74fb7aadb22e732720daff0
MD5: 7b821616bf2a78472286d61c19e03bd1
MD5: 9f257f99a479d2f7b19c21255719a995
MD5: bc89a2185ab2f317a5a58e7a7c35daa8
MD5: 916c95e50ec4d6010a2818de50a94ff5
MD5: 32cfae63aa9be58e32829fe6c4f89a85
MD5: e40b6d4953b7923d52b0315429d16c10
Webroot SecureAnywhere users are proactively protected from these threats.