Happy New Year, everyone! Despite the lack of blog updates over the Holidays, we continued to intercept malicious campaigns over the same period of time, proving that the bad guys never take holidays. In this post, I’ll profile two prolific, social engineering driven type of malicious spam campaigns that we intercepted over the Holiday season, and naturally (proactively) protected you from.
More details:
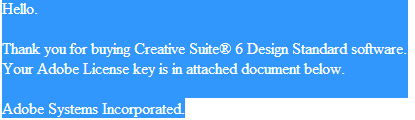
The first campaign successfully impersonates Adobe’s License Service Center, in an attempt to trick users into thinking that they’ve successfully purchased a Creative Suite 6 Design Standard software license key.
Sample screenshot of the first spamvertised campaign:
Detection rate for the spamvertised attachment: MD5: 10dbbaaceda4dce944ebb9c777f24066 – detected by 40 out of 48 antivirus scanners as TrojanDownloader:Win32/Kuluoz.D.
The second campaign, attempts to trick users into thinking that they’ve received a notice to appear in court.
Sample screenshot of the spamvertised attachment:
Detection rate for the spamvertised attachment: MD5: c77ca2486d1517b511973ad1c923bb7d – detected by 38 out of 47 antivirus scanners as TrojanDownloader:Win32/Kuluoz.D; Backdoor.Win32.Androm.bket.
Once executed the sample phones back to:
hxxp://109.169.87.141/798475540DFA75FE5945D24FA5CBF9A5578EB29359 (picasa.com.fidelidadeciel0.com is also known to have responded to 200.98.141.0)
Two more MD5s are known to have responded to the same C&C IP in the past, namely:
MD5: c77ca2486d1517b511973ad1c923bb7d
MD5: c1c56f3ae9f9da47e1c0ebdb2cffa2a3
Webroot SecureAnywhere users are protected from these threats.