Throughout 2013, we not only witnessed the re-emergence of proven mass, efficiency-oriented Web site hacking/exploitation tactics, such as, the reliance on Google Dorks scanning, good old fashioned brute-forcing, but also, the introduction of new concepts, successfully utilizing/standardizing, both, compromised accounting data, and server-farm level access, in an attempt to fraudulently monetize the hijacked traffic from legitimate Web sites.
As we’ve seen on numerous occasions throughout the years, despite sophisticated ‘innovations’, cybercriminals are no strangers to the KISS (Keep It Simple Stupid) principle. Case in point in terms of Content Management Systems (CMSs) is WordPress, whose market share is naturally proportional with attention the platform is receiving from fraudulent/malicious adversaries. In this post, I’ll discuss a DIY type of Python-based mass WordPress scanning/exploiting tool, available on the underground marketplace since July 2013, emphasize on its core features, and overall relevance in a marketplace dominated by competing propositions.
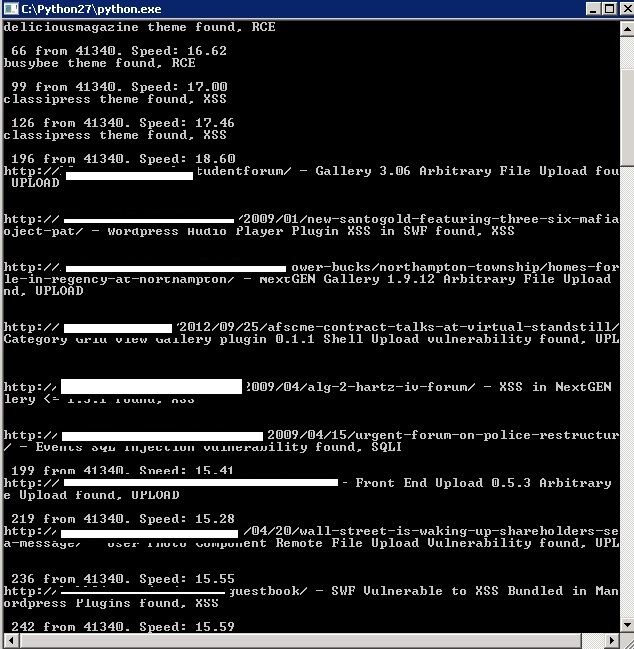
Sample screenshot of the tool in action:
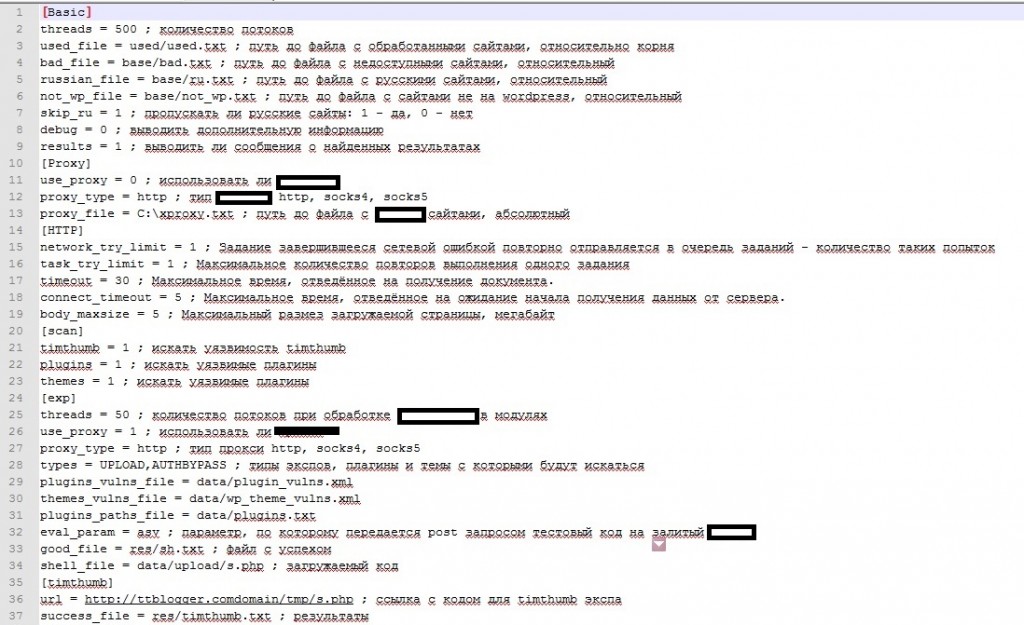
Sample screenshots of the tool’s configuration file:
Sample tool output:
Among the first features worth emphasizing on, is a good old fashioned Russian/Eastern European cybercriminal’s mentality namely the exclusion of Russian/Eastern European traffic from the exploitation process — in direct contradiction with these greed driven underground market propositions — through an option, allowing the tool’s customer to prevent Russian Web sites from being scanned/exploited. In comparison with known tactics relying on the syndication of remotely exploitable vulnerabilities, and utilizing them for scanning/exploitation through the use of botnets, the proxy-supporting DIY tool, has a built-in database of hundreds of publicly available/patched exploits, and is capable of scanning tens of thousands of WordPress installations in a multi-threaded fashion. Relevant examples of such type of mass abuse, include 2010’s mass WordPress exploitation campaigns affecting, GoDaddy and Network Solutions.
Price of the tool? $200.
WordPress user are advised to educate themselves on basic WordPress hardening practices, as well as to inquire whether or not their WordPress hosting provider is issuing security patches in a managed fashion.