Sticking to good old fashioned TTPs (tactics, techniques and procedures), cybercriminals continue mixing purely malicious infrastructures with legitimate ones, for the purpose of abusing the clean IP reputations of networks, on their way to achieving positive ROI (return on investment) for their fraudulent activities. For years, this mix of infrastructures has lead to the emergence of the ‘malicious economies of scale’ concept, in terms of efficient abuse of legitimate Web properties, next to the intersection of cybercriminal online activity, and cyber warfare.
In a series of blog posts, we’ve been emphasizing on the level of automation and QA (Quality Assurance) applied by vendors of cybercrime-friendly tools and services, compromised/hacked Web shells in particular. Largely utilized for the hosting of fraudulent/malicious content, in addition to acting as stepping stones for the purpose of providing a cybercriminal with the necessary degree of anonymity when launching campaigns, the concept continues representing an inseparable part of the cybercrime ecosystem, due to the ever-green public/OTC (over-the-counter) marketplace for high page-ranked Web shells.
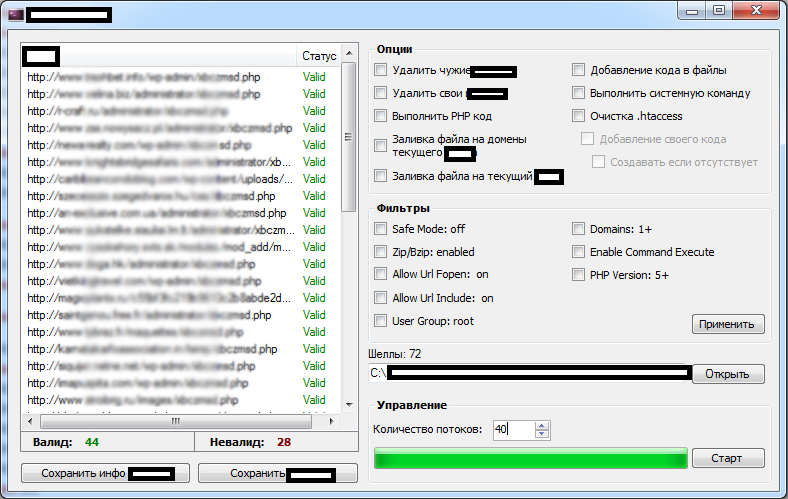
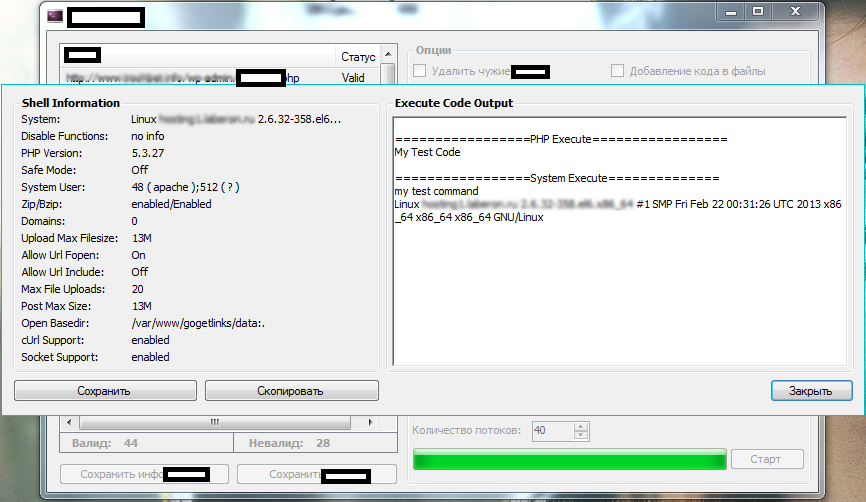
We’ve recently spotted a newly released commercial Windows-based compromised/hacked Web shells management application that empowers potential cybercriminals with the necessary capabilities to maintain and manage their portfolio of Web shells. Let’s take a peek at the application, and discuss some of its features.
More details:
Sample screenshots of the Windows based compromised/hacked Web shells management application:
Some of its core features include:
– Web shell validation
– Signatures-based detection/removal of competing shells
– Domains count on a per compromised/hacked Web shell basis for the purpose of monetizing the data by selling it to prospective buyers
– Removal/modification of .htaccess
Priced at $100, the application’s key differentiation factor is the ability to detect and remove competing shells through a signatures-based process. This once again puts the spotlight on the ‘Tragedy of Commons‘ theory, in the broader context of today’s over-populated underground marketplace, and the flawed notion that specific vendors believe that the more cybercriminals join the ecosystem, the less revenue will flow back their way. Thanks to the ever-green market segment for hacked/compromised Web shells accounting data, as well as the systematic remote exploitation of vulnerable Web applications/CMS (content management systems), cybercriminals remain in a perfect position to continue monetizing these TTPs, for the purpose of launching fraudulent/malicious campaigns.
We’ll continue monitoring the development of the tool.