Everyday cybercriminals actively take advantage of basic OPSEC (Operational Security) tactics, aiming to risk-forward their fraudulent/malicious online activity to a third-party, while continuously seeking to launching their malicious/fraudulent campaigns in an anonymous fashion. Having successfully matured from, what was once a largely immature market segment to today’s growing market segment, in terms of active implementation of OPSEC concepts, the blackhat market is prone to continue expanding, further providing malicious and fraudulent adversaries with the necessary capabilities to remain beneath the radar of law enforcement and the security industry.
In a series of blog posts we’ve published throughout 2013, we proactively highlighted the emergence of the TDoS (Telephony Denial of Service) attacks in the context of cybercriminals’ growing non-attributable capabilities to target and exploit (basic) vulnerabilities in telephone/mobile systems internationally. Largely relying on fraudulently obtained SIM cards and compromised accounting data at legitimate VoIP providers, as well as active utilization of purely malicious infrastructure, TDoS vendors constantly seek new tactics to apply to their OPSEC procedures.
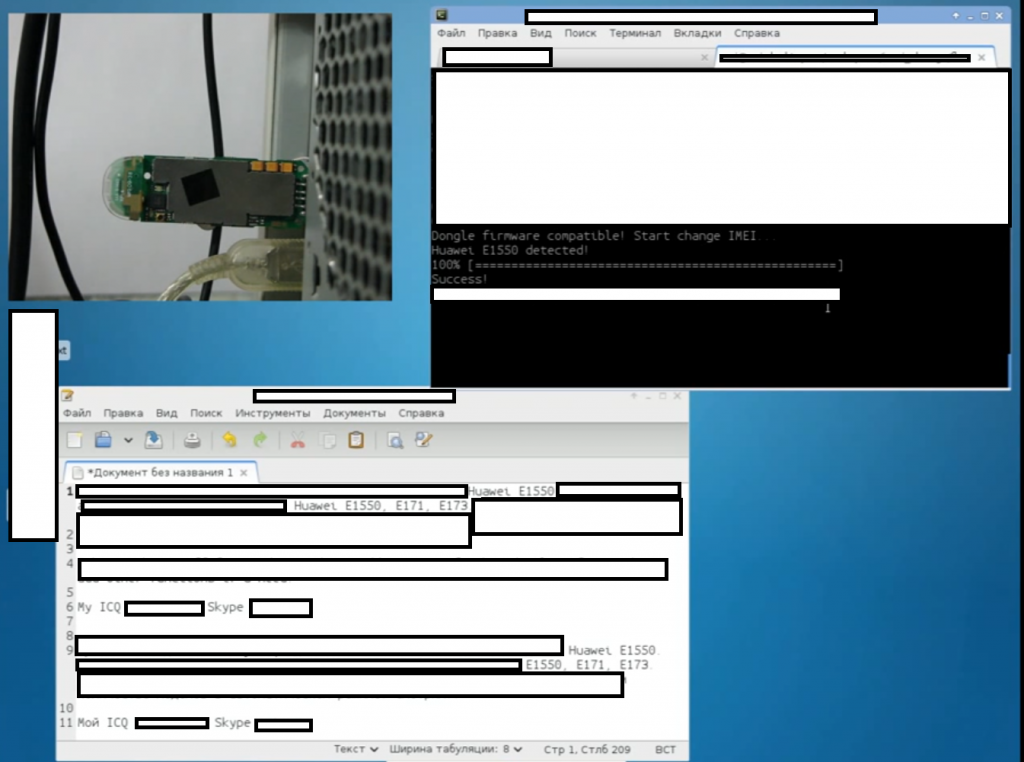
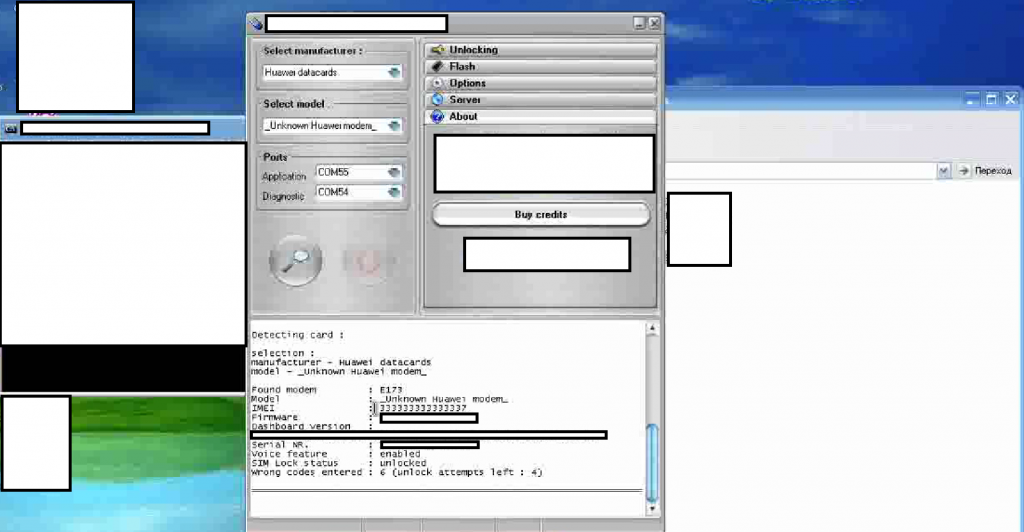
Having proactively profiled the TDoS market segment throughout 2013, we’re also keeping eye on value-added services/features, namely, the modification of a mobile device/USB dongle’s International Mobile Station Equipment Identity (IMEI), for the purpose of adding an additional layer of anonymity to the fraudulent/DoS process. Let’s profile several vendors offering IMEI modification services and discuss their relevance within the TDoS market segment.
More details:
Sample screenshots of the IMEI modification process by multiple vendors of the anonymity and non-attribution centered service:
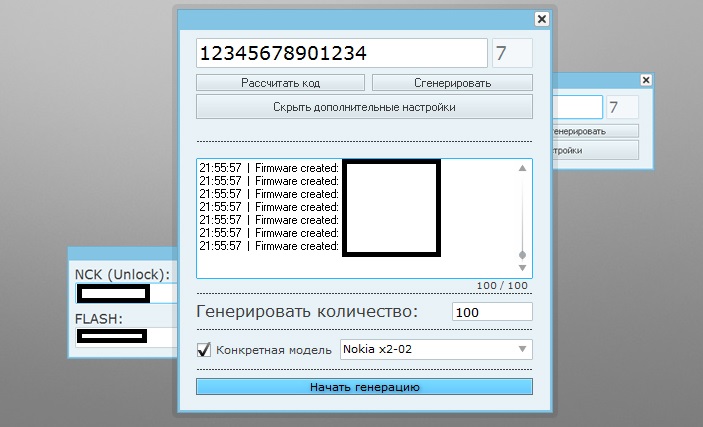 What’s particularly interesting about these services is the fact that they rely on automatically-generated IMEI codes which provide plausible deniability when launching malicious or fraudulent attacks. The services that we’re currently aware of rely on DIY (do-it-yourself) type of valid IMEI generating applications. Priced at $450, a sampled application targets both Windows and Linux users and is exclusively targeting Huawei USB dongles, with the company currently possessing a 55% international market share for datacards. We expect that cybercriminals will start applying this OPSEC tactic to their fraudulently obtained SIM cards/datacards, in an attempt to add an additional layer of OPSEC to their campaigns.
What’s particularly interesting about these services is the fact that they rely on automatically-generated IMEI codes which provide plausible deniability when launching malicious or fraudulent attacks. The services that we’re currently aware of rely on DIY (do-it-yourself) type of valid IMEI generating applications. Priced at $450, a sampled application targets both Windows and Linux users and is exclusively targeting Huawei USB dongles, with the company currently possessing a 55% international market share for datacards. We expect that cybercriminals will start applying this OPSEC tactic to their fraudulently obtained SIM cards/datacards, in an attempt to add an additional layer of OPSEC to their campaigns.
We’ll continue monitoring the TDoS market segment and post updates as soon as new developments take place.