With WordPress continuing to lead the CMS market segment, with the biggest proportion of market share, cybercriminals are actively capitalizing on the monocultural insecurities posed by this trend, in an attempt to monetize the ubiquitous (for the cybercrime ecosystem) TTPs (tactics, techniques and procedures). Despite actively seeking new and ‘innovative’ ways to abuse this trend, cybercriminals are also relying on good old fashioned reconnaissance and ‘hitlist’ building tactics, in an attempt to achieve an efficiency-oriented ‘malicious economies of scale’ type of fraudulent/malicious process.
We’ve recently spotted a managed WordPress installations-targeting, XML-RPC API abusing type of DDos (Denial of Service) attack service, whose discovery intersects with a recently launched mass widespread WordPress platform targeting campaign.
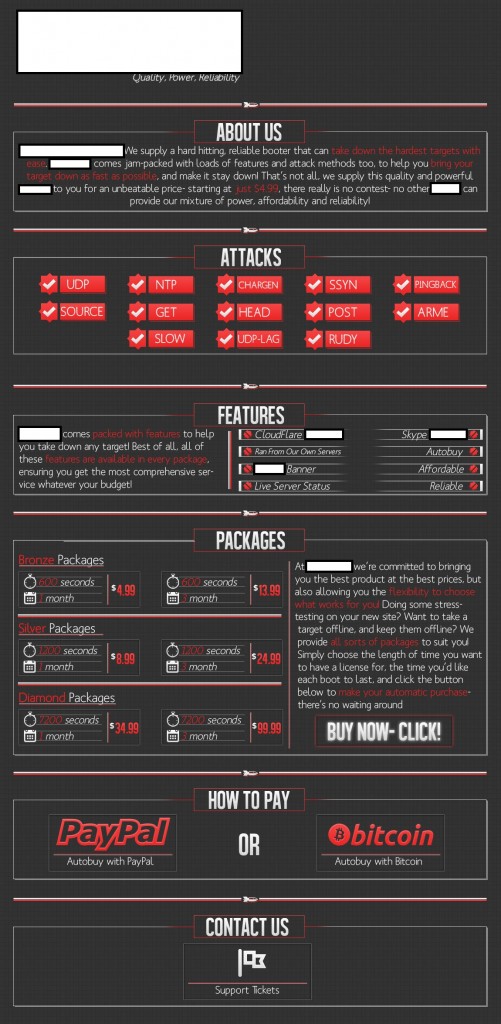
Sample screenshot of the managed DDoS WordPress-targeting XML-RCP API abusing service:
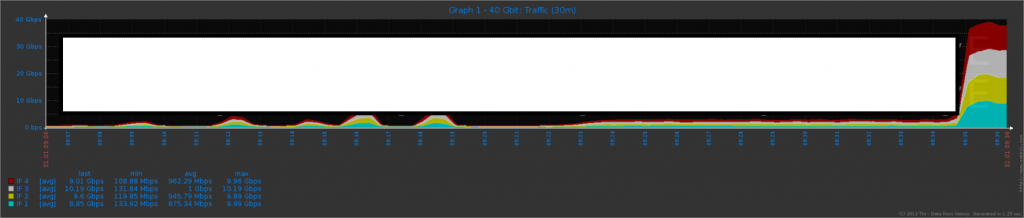
In addition to offering a variety of DDoS attack methods, the service is also offering multiple ‘value-added’ features, such as popular hosting/VoIP platforms resolving services. Priced between $4.99 and $99.99 for different packages, it also currently accepts PayPal and Bitcoin, and is capable of delivering over 40 Gbps of DDoS bandwidth. Its key differentiation factors include Source Banner reconnaissance scanning capability, as well as the direct abuse of a well known WordPress platform abuse vector, namely, the XML-RPC API pingback type of DDoS attack vulnerability.
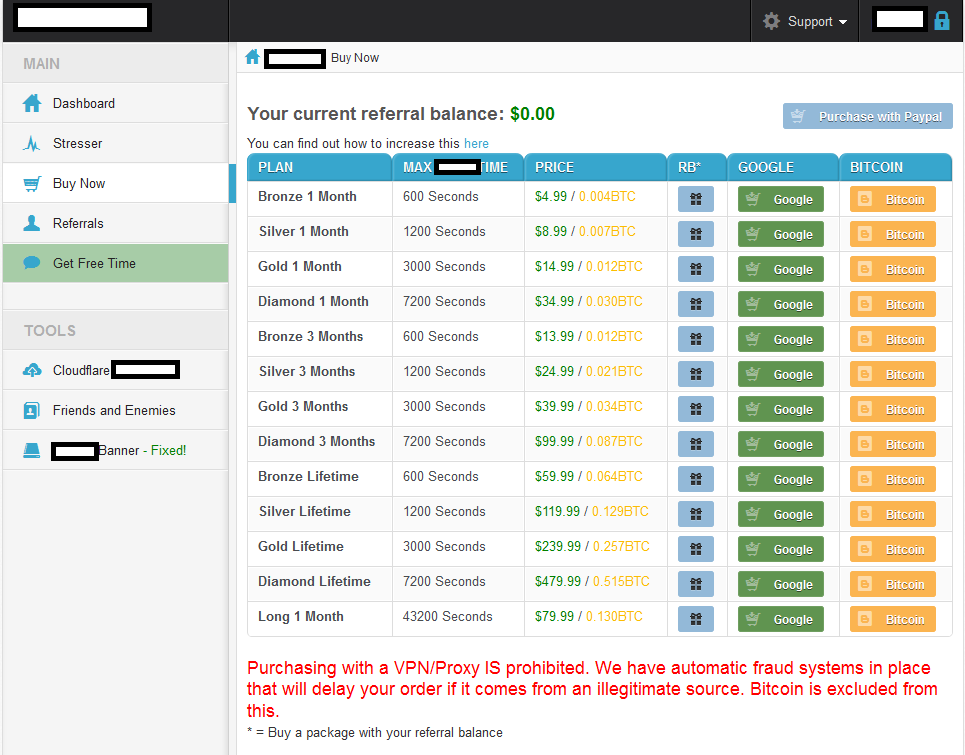
Sample screenshot of a prospective service’s customer Web based interface:
Sample screenshot of the service’s DDoS capabilities:
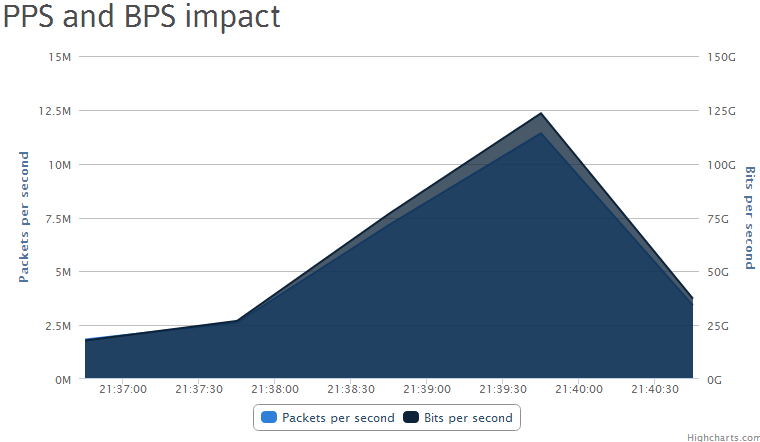
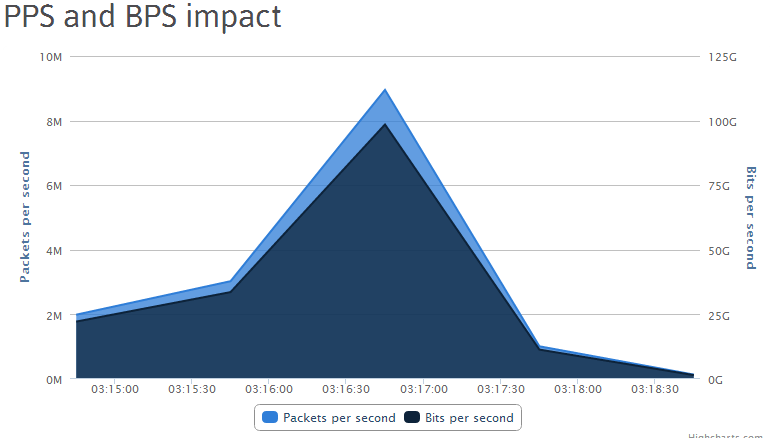
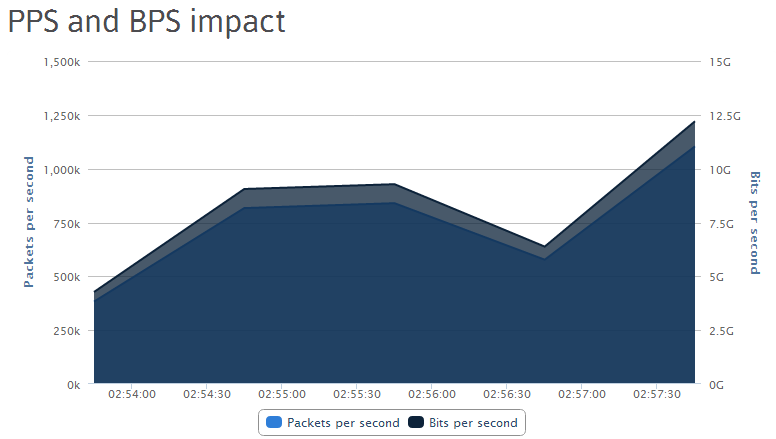
Related screenshots of the promoted service’s DDoS bandwidth capacity:
Despite the evident malicious ‘innovation’ on behalf of the adversaries behind the XML-RPC API pingback based DDoS attack campaign, on a large scale, cybercriminals continue largely relying on DIY (do-it-yourself) types of DDoS malware/botnet generating tools, successfully leading to the growth of the ever-green market segment for managed DDoS attacks. To mitigate the risk of falling victim to such widespread WordPress CMS targeting campaigns, WordPress owners are advised to go through the official WordPress hardening guide, as well as to take advantage of Sucuri’s free DDoS scanning service.
We’ll continue monitoring the development of the service, and post updates as soon as new developments take place.