Cybercriminals continue to systematically release DIY (do-it-yourself)type of cybercrime-friendly offerings, in an effort to achieve a ‘malicious economies of scale’ type of fraudulent model, which is a concept that directly intersects with our ‘Cybercrime Trends – 2013‘ observations.
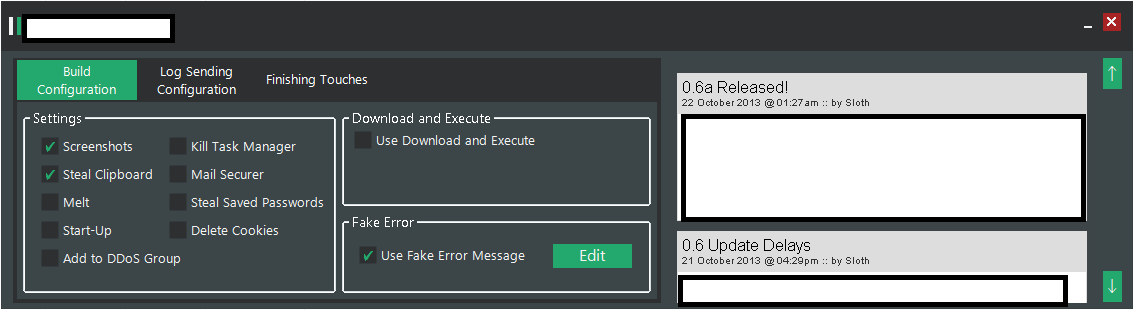
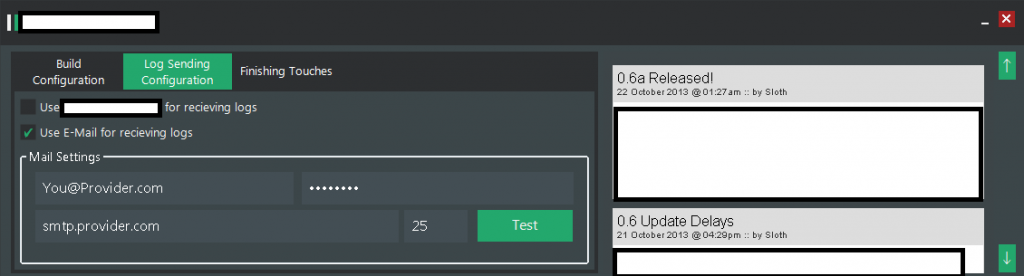
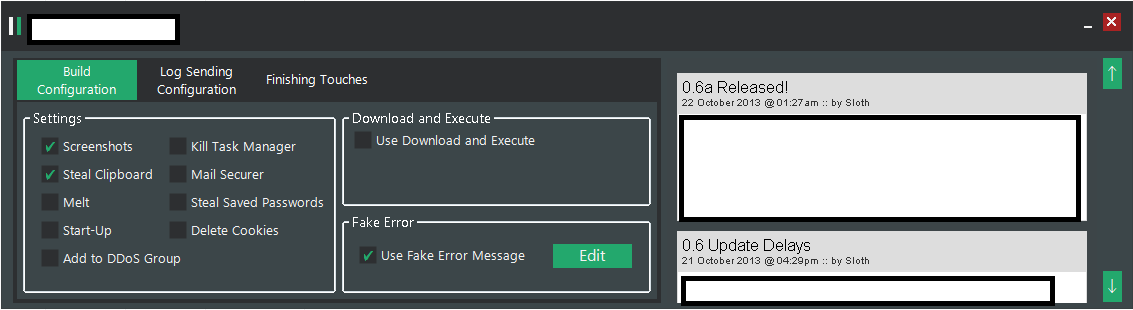
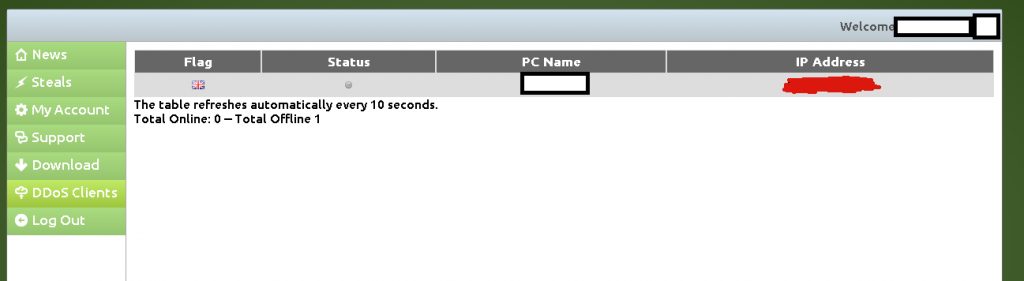
We’ve recently spotted yet another subscription-based, DIY keylogging based botnet/malware generating tool. Let’s take a peek inside its Web based interface, and expose the cybercrime-friendly infrastructure behind it.
More details:
Sample screenshots of the DIY keylogging platform:
Next to the standard keylogging features, the botnet/malware generating tool also comes with DDoS functionality. What’s particularly interesting about this tool is that its primary hosting location exposes a cybercrime-friendly malicious infrastructure worth keeping an eye on. Let’s take a look.
Known to have phoned back to the same IP as the original hosting location (37.221.160.39) are also the following malicious MD5s:
MD5: 6b6836efff22dae8fd49de23e850f9a4
MD5: b60df6003c214d29f574b871530d0e3a
MD5: d4eb62529918bd18820809d34d8a443b
MD5: 42c826634ee1479de99b2a354475574d
Related serial numbers:
Serial Number: 27 42 F1 24 28 26 FB 7F 69 B0 52 B7 F3 94 DF ED
Serial Number: 00 9B 51 7C AF 08 AA 1A 85 82 2D B0 CE 5E 91 69 FE
Once executed MD5: 6b6836efff22dae8fd49de23e850f9a4 phones back to:
hxxp://freedowloading.tk/love/gate.php – 37.221.160.39
Once executed MD5: b60df6003c214d29f574b871530d0e3a phones back to:
hxxp://os.downloadastrocdn.com (54.245.233.100)
hxxp://marketsmaster.org (37.221.160.39)
hxxp://images.downloadastro.com (54.230.184.115)
hxxp://img.downloadastrocdn.com (199.58.87.151)
hxxp://cdneu.downloadastrocdn.com (146.185.27.45)
hxxp://cdnus.downloadastrocdn.com (74.81.69.244)
hxxp://liveupdate.symantecliveupdate.com (195.12.226.226)
hxxp://stats.norton.com (63.245.201.111)
hxxp://rp.downloadastrocdn.com (54.244.253.240)
Related malicious MD5s known to have phoned back to (os.downloadastrocdn.com; 54.245.233.100):
MD5: 7653f1815f563d0de16effff5ca2e87a
MD5: 3c4c28ee8da612b86d0d25c9bab878b2
MD5: 26dcae966055a426344649947873d5f5
MD5: 4fad1ced75f400183b977e0a763e6e5a
MD5: 9f052ce63f1197aedf9ab6c677442076
MD5: 4949d65b597dd83b1e6e6b5feacff337
MD5: fb25222b269b58f78305dfc0e84f03d0
Once executed MD5: d4eb62529918bd18820809d34d8a443b phones back to:
hxxp://os.5oftwarescdn.com (54.245.235.34)
hxxp://download.my-apps-repository.com (69.16.175.10)
hxxp://re2.pw (64.79.83.242)
hxxp://50ftwares.com (64.79.83.254)
hxxp://marketsmaster.org (37.221.160.39)
hxxp://img.5oftwarescdn.com (199.58.87.155)
hxxp://cdneu.5oftwarescdn.com (146.185.27.45)
hxxp://cdnus.5oftwarescdn.com (199.58.87.155)
hxxp://wajam.com (198.199.14.15)
Once executed MD5: 42c826634ee1479de99b2a354475574d phones back to:
hxxp://download.my-apps-repository.com (69.16.175.42)
hxxp://os.5oftwarescdn.com (54.245.233.100)
hxxp://re2.pw (64.79.83.242)
hxxp://50ftwares.com (64.79.83.254)
hxxp://marketsmaster.org (37.221.160.39)
hxxp://img.5oftwarescdn.com (199.58.87.151)
hxxp://cdneu.5oftwarescdn.com (65.254.40.36)
hxxp://cdnus.5oftwarescdn.com (199.58.87.155)
hxxp://wajam.com (198.199.14.10)
Webroot SecureAnywhere users are proactively protected from these threats.