Relying on the systematic release of DIY (do-it-yourself) mobile malware generating tools, commercial availability of mobile malware releases intersecting with the efficient exploitation of legitimate Web sites through fraudulent underground traffic exchanges, as well as the utilization of cybercrime-friendly affiliate based revenue sharing schemes, cybercriminals continue capitalizing on the ever-growing Android mobile market segment for the purpose of achieving a positive ROI (return on investment) for their fraudulent activities.
We’ve recently spotted yet another underground market proposition offering access to Android-based infected devices. Let’s take a peek inside its Web-based command and control interface, discuss its features, as well as the proposition’s relevance within the cybercrime ecosystem.
More details:
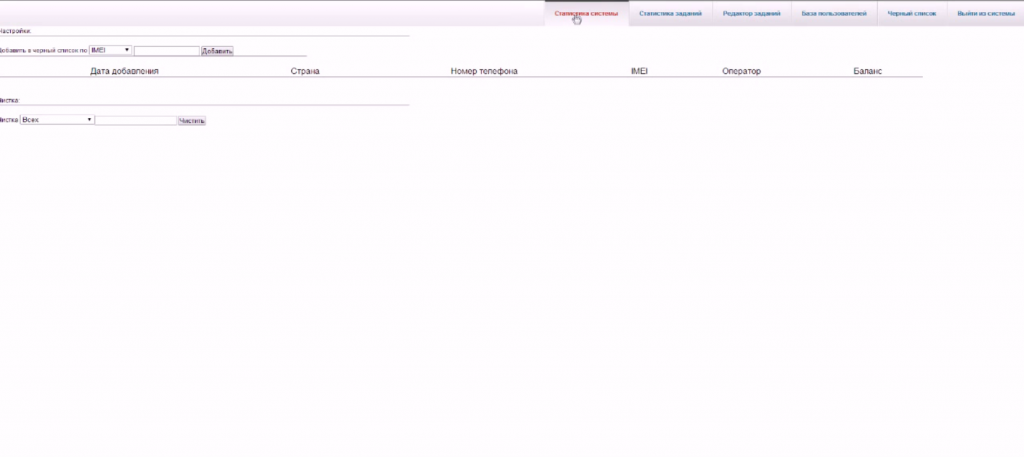
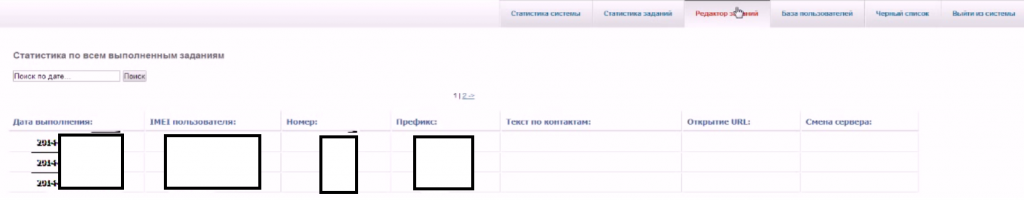
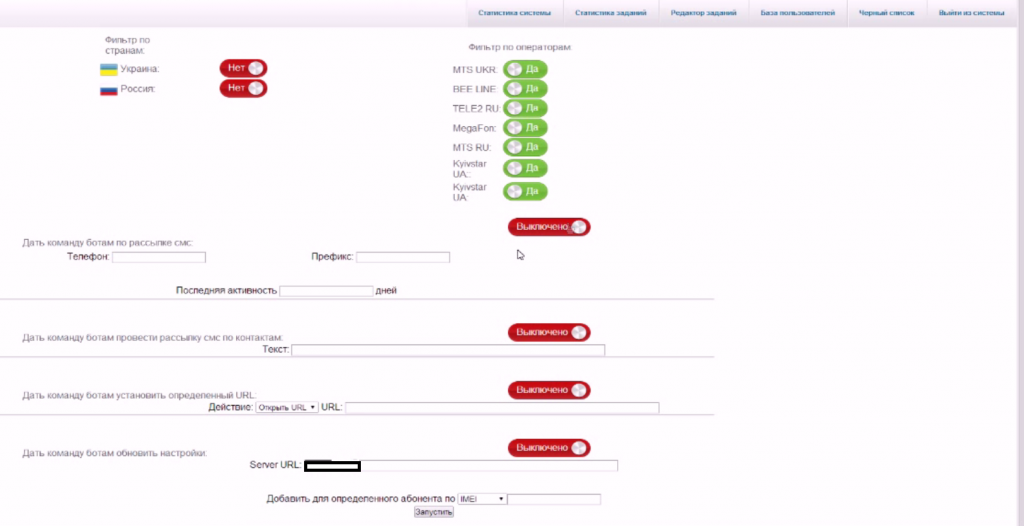
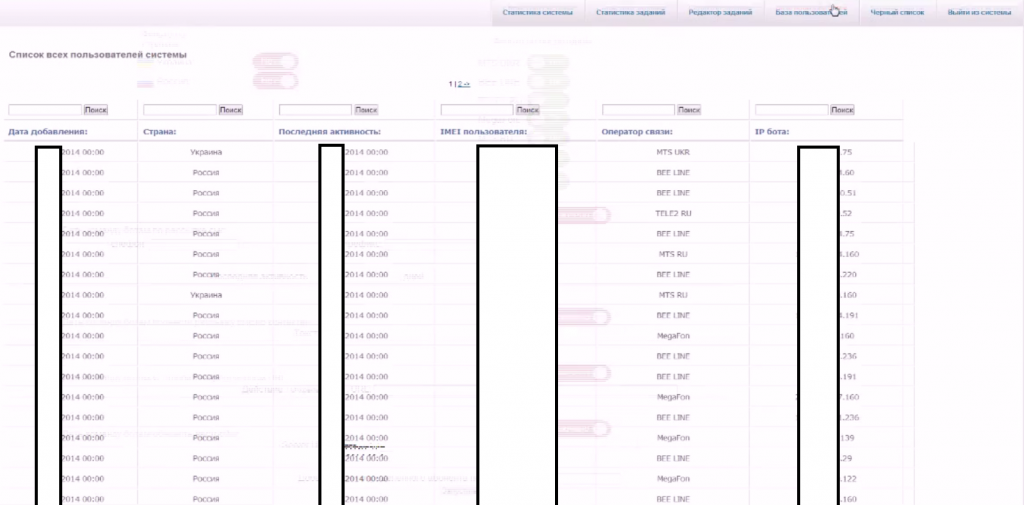
Sample screenshots of the commercially available Android-based botnet for hire:
This commercially available Android-based botnet currently offers access to 833 hosts, comes with a manual, and offers the market segment’s standard premium rate number monetization features. It is currently priced at $1,019.
Thanks to basic traffic acquisition tactics, such as underground cybercrime-friendly traffic exchanges relying on the efficient exploitation of legitimate Web sites, mobile traffic segmentation, and Android based affiliate networks offering novice cybercriminals access to automatically generated mobile malware, cybercriminals are positioned to continue expanding the mobile malware market segment, largely relying on the TTPs (tactics, techniques and procedures) that we discussed in our “Cybercrime Trends – 2013” summary.
We’ll continue monitoring the development of the Android based mobile malware market segment, and post updates as soon as new developments take place.