Update: Apple has patched the Bash bug. For more info (including links to download the updates on your Mac), check out this TechCrunch report.
As of last week, there’s a new security bug in the news, and it’s wreaking havoc on the Internet.
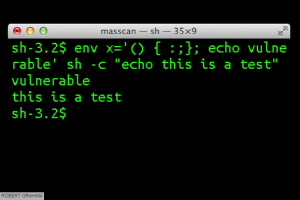
(Source: Macworld/Errata Security)
Discovered by Stephane Chazelas, a security researcher for Akamai (who revealed the bad news to the world last Thursday), the ‘Bash bug, or ‘Shellshock’, is a particularly nasty vulnerability affecting the Bourne-Again Shell (thus the Bash acronym) of certain versions of the Unix and Linux operating systems. Yes, that includes derivatives like the Mac OS. In other words, it’s everywhere, and could affect a countless number of devices that connect to the internet.
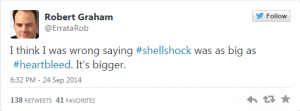
Remember Heartbleed? This is scarier. And potentially a bigger deal, too.
Why? According to Robert Graham of Errata Security:
“Unlike Heartbleed, which only affected a specific version of OpenSSL, this bash bug has been around for a long, long time. That means there are lots of old devices on the network vulnerable to this bug. The number of systems needing to be patched, but which won’t be, is much larger than Heartbleed.”
Oh, and it IS old. How old? Graham said in a different blog post that the bash issue has been around for 20 years.
For the record, the National Vulnerability Database gave Bash a 10/10! Here’s what you should know.
What is it?
As previously mentioned, it’s vulnerability, a bug affecting the Bash shell used in many Unix and Linux operating systems. Think of the Bash shell as the command-line shell. This means that a hacker could take over and issue remote commands to web servers that aren’t patched. As a result, private information could quickly become public information.
Is every device running Linux or Unix vulnerable?
No. According to Rapid7 Global Security Strategist Trey Ford, there are certain requirements that make a server vulnerable. More specifically, servers capable of passing commands over the internet remotely, are susceptible.
What makes it so dangerous?
Bash may not affect as many devices as Heartbleed, but that may be the only consolation. Because (unlike Heartbleed) Bash lets hackers execute commands remotely, the repercussions could be a lot more serious.
Who should be worried? Should you?
While network administrators who manage internet presence for their companies (particularly those running a CGI app written in Bash or using Bash script), should be concerned, the everyday desktop user probably doesn’t have as much to worry about. That is unless you have a bunch of connected ‘Internet-of-things devices’
What about those Internet-of-Things Devices?
This is largely about patching updates, so while the aforementioned everyday desktop user may not be affected by Bash, that doesn’t necessarily mean his or her connected devices aren’t vulnerable. From home automation systems to routers to webcams to refrigerators, there are many Internet-of-things devices that use the Bash script. And most users would probably never think twice about installing software updates on something like a fridge. Now they should.
What’s being done?
Companies like Google and Amazon were quick to react, rushing Thursday to patch this latest vulnerability on their end. And because recent versions of the Mac OS are vulnerable, Apple quickly responded, saying that while most OSX users aren’t at risk, the company was quickly working on patching the flaw. You can read more about that here.
What should you do?
Unfortunately, there’s not much you can do as this is a widespread vulnerability rather than say, a sneaky piece of malware. And because this is the case, you, as a consumer, can’t contain it by yourself. Rather, it’s up to the those maintaining the web servers. But absolutely do pay attention, run updates, and look for notifications from service providers who are vulnerable to Bash. And if a company tells you to take action and change your password because their servers are affected, listen to them and get on that immediately.
What about Webroot Servers?
We took all the necessary precautions and upgraded all of our systems to the patched version. We can verify that none of our services are susceptible. You can find our official statement on this support section of our site.
We’ll be keeping a close watch to see how this story unfolds, but in the meantime, take the necessary steps to ensure you’re as protected as possible and install necessary updates as they become available.







Its quite shocking how something like this has been around for 20 years now. that means that my grans old pentium one running windows 98 could have it. The fact that if you have this on your device someone can remotely issue commands from your computer means they can monitor your keyboard input as well which means you’d have to change your passwords and your whole life could basically be stollen from right in front of our eyes, literally.