The encrypting ransomware business model is hugely successful and isn’t going away any time soon (possibly ever). This latest variant not only encrypts the normal scope of valued files, but it now encrypts files required for your games – saves, mods, and profiles (like Day Z). It even even encrypts game software components from the like of Valve, Bethesda, Unreal engine, and RPG Maker. This means many of the major games that users play will be rendered useless unless they pay the ransom if hit by the malware. For a full list of the scope of files encrypted see here.
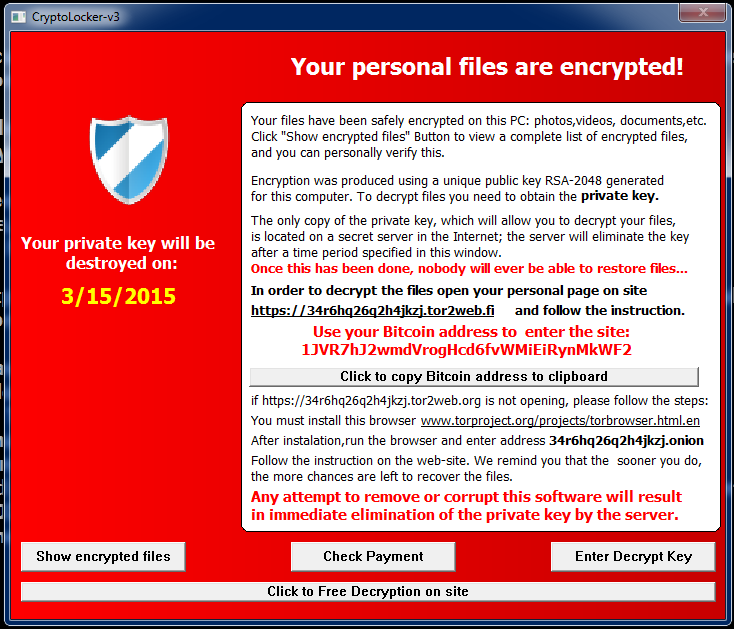
Here is what the GUI looks like
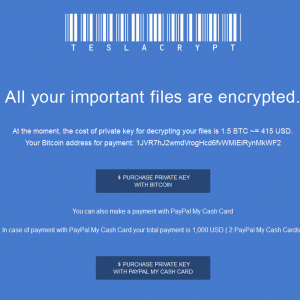
Notice how it says “CryptoLocker-V3” on the window and has a uncanny resemblance. However, this is very different from the original cryptolocker so don’t be fooled. Tools like decryptolocker.com are NOT going to work on this variant. It also mentions “Click to Free Decryption on site”. When we first saw this we thought maybe it offered a free decryption similar to what we observed on an older ransomware variant, but it’s just a lie. Here is what you are presented with when you go to the decryption site and enter the bitcoin address it assigns you.
Bitcoin is the preferred method of payment as it is a untraceable secure method of receiving payment from you so they give you a better price of only $415. If you wish to use payment systems like PayPal My Cash Card, then the price increases to $1000 (this is because they lose a percentage through the middleman). The choice is very clear that they want the hefty discount to sway you into using bitcoin as payment.
Webroot will catch this specific variant in real time and heuristically before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware