Yesterday in the news we saw a huge spike in the interest of the Rombertik malware. Rombertik infiltrates the computer through email phishing attacks that drop as a .scr screen saver executable that contains the malware that will inject code into your browsers to spy on you and threaten your MBR or Encrypt documents if it detects that it’s being analyzed or sandboxed. We’ve been catching these variants since January 13th, but only now has it become so popular with the media coverage.
The initial drop is a zipped attachment and once unzipped it’s a .scr screensaver executable file. The first stage of the malware is checks to make sure it’s not being debugged or sandboxed where if it fails these checks will attempt to overwrite your MBR (Master Boot Record).
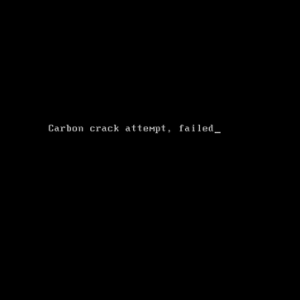
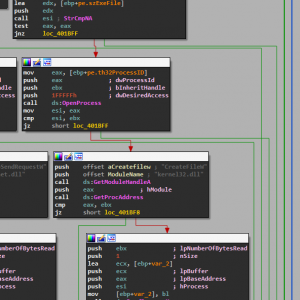
Here we can see the code “\\\\.\\PhysicalDrive0” in the first image where it is attempting to obtain the handle to the MBR. If it can get access to the MBR then it will perform the second image where it writes 200 hex bytes to the MBR with buffer to display the below message after the BIOS when starting your computer – forcing a bootloop until the operating system is reinstalled.
However, you will need to give this administrator rights in order for the MBR or encrpyting routine to complete. So unless you’re an XP user, you’ll see that familar user account control pop up asking if you wish to give “yfoye.exe” permission. I don’t know how many users are blindly giving permission to random executables that are originally expected to be documents from attachments (many group policies in businesses are also set to not give admin rights to email attachments), but I would suspect that the scare hype of this malware is limited to XP users.
After all the checks for sandboxing and debugging are cleared the malware will then perform it’s normal operation of hooking into your browser. Below in the first image is Rombertik searching for handles to the Firefox process (it does this with other browsers like Chrome as well).
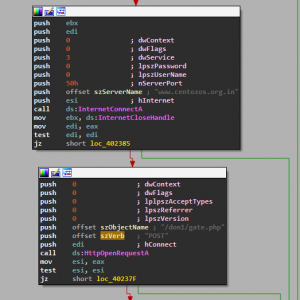
Then the second images shows it will connect to home and ensure that it can securely transmit the data it intercepts. Below, the malware injects a thread into the browser process to intercept and monitor network traffic API calls
For Rombertik specifically it drops through email phishing and Webroot has multiple layers of protection. First is going to be through the zip – we actually detect this exact drop as a zip once it writes to disk. If that doesn’t trigger, then next layer is once it’s extracted and will be blocked in real time right as the .scr executable inside the zip it’s written to disk. If that fails, then next layer of protection is through heuristics if an action by the file is picked up. Since after the sandbox checks it launches a second copy of itself and overwrites the second copy with remaining thread process it’s very suspicious and a common tactic used by encrypting ransomware as well so our heuristics look out for actions like this.
MD5 Analyzed:
F504EF6E9A269E354DE802872DC5E209 (W32.Rombertik.Gen)
Aditional MD5s:
9FA5CE4CD6323C40247E78B80955218A (W32.Rombertik.Gen)
21A728FCD1A45642490EE0DAF17ED73A (W32.Rombertik.Gen)
FAADD08912BADEF2AB855D0C488B9193 (W32.Rombertik.Gen)
AC94549FAF48D11778265F08535A55B7 (W32.Rombertik.Gen)
D95495728DB1D257C78BCC19B43E94FF (W32.Rombertik.Gen)
3733DD9DF99C08953216B3DA5A885EFD (W32.Rombertik.Gen)
B5AFBB36D9E3EC3BC4A9445627C23E4F (W32.Rombertik.Gen)
38F5191DE5B8C266746006E9766B2F9D (W32.Rombertik.Gen)






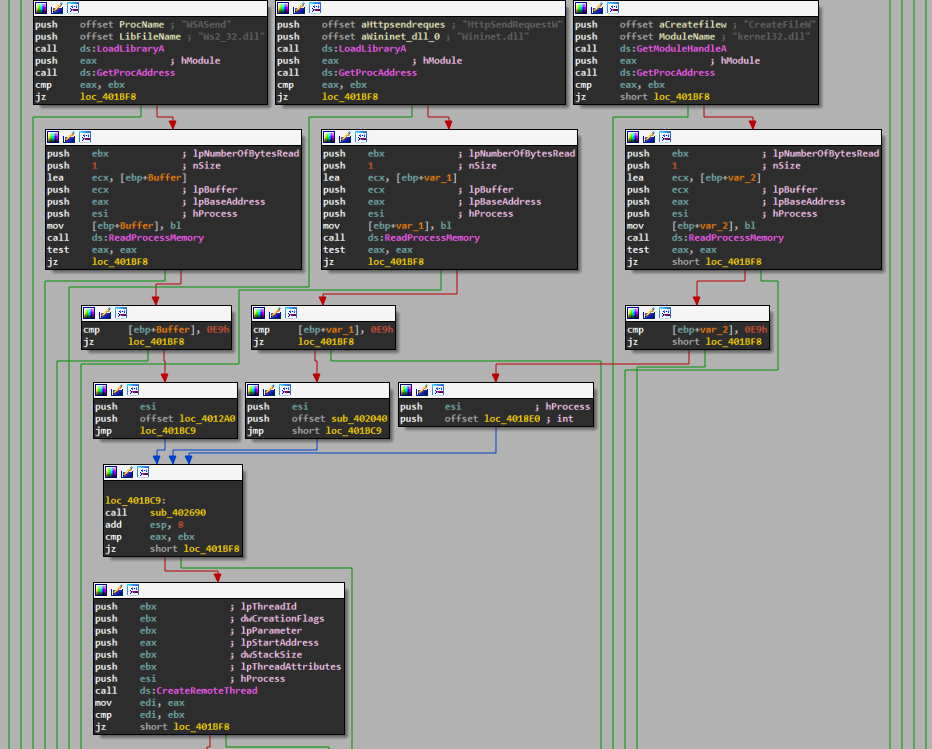
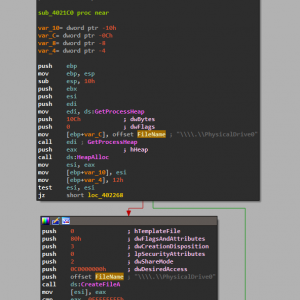
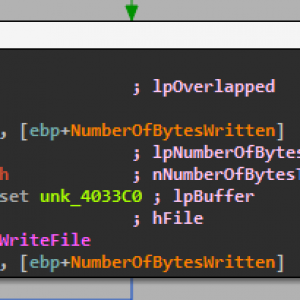
How does it do its hooking? I mean I know it uses CreateRemoteThread to inject itself following the WriteProcessMemory call in say….iexplore. I know it enables SPDY via the registry and gives itself SeDebugPrivilege, but what happens after that? How does it call home?
Nevermind, I figured it out. It hooks 1 of 3 api functions. Scrapes data from the hooked functions.