Update: We now have a soundbite of the music played after infection:
The RaaS (Ransomware as a Service) business model is still seeing growth. Here is the latest cyber criminals have to offer and it could later on be used for Mac and Linux OS
As with all other RaaS platforms you sign up to create new samples from hidden servers in the Tor Network. Just input the bitcoin wallet address you want your “revenue” to be deposited in.

Once you input a deposit bitcoin address, you’ll be presented with a very easy to use portal with customization and stats. The customization allows you to fully lock the computer – which will make the lockscreen pop-up every few seconds and not be able to be minimized. What is interesting is that it even mentions to use caution with this feature as victims will find it difficult to check that their files have even been encrypted and will have to use another machine to pay the bitcoin ransom. The stats will show you how many people you are infecting and how many people are paying the ransom.

Once you click download it will generate the malware with your customized setting and payment amount. The size of the file is 22MB which is quite large for malware in general. This is because main malware component inside the payload, “chrome.exe” is a packaged NW.js application which contains the malware code. NW.js s a framework that lets you call Node.js modules directly from the DOM and enables a way of writing applications with multiple web technologies that work on ALL operating systems. While we did see strings in the code reference commands only used on Unix operating systems, current samples only work on windows… for now. We suspect that Mac/Linux compatibility is in the works.

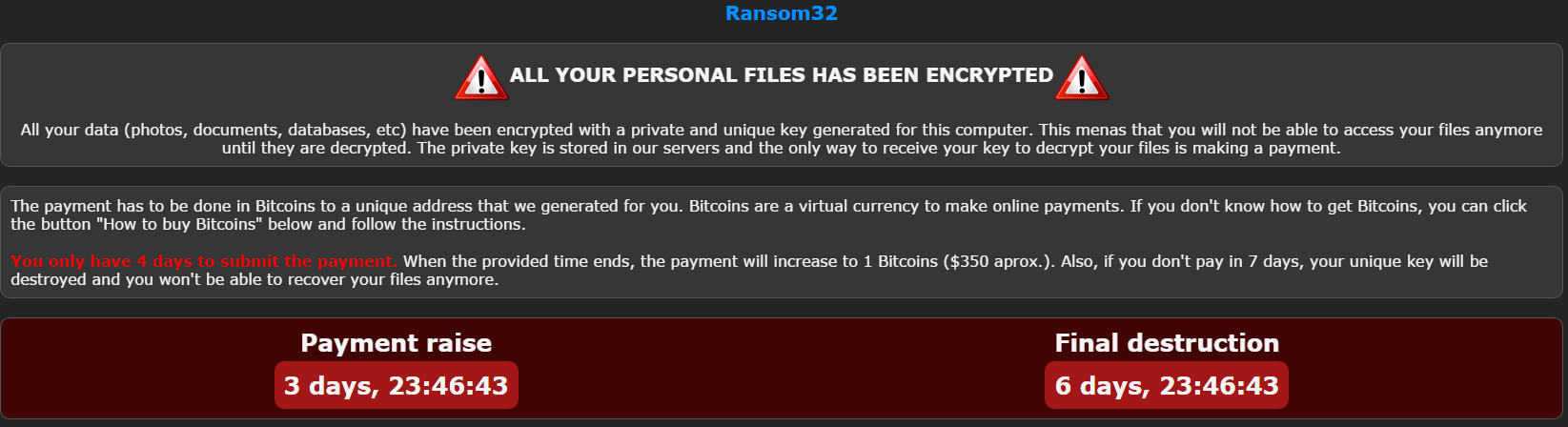
This is the infection lockscreen that pops up once you are infected and files are encrypted. You are also blasted with music from the video game Metal Gear Solid – which is bizarre and very obnoxious. We see that they’ve made sure to use the free decrypt tactic that was first introduced in 2014 with CoinVault – we did confirm that this feature works.

As always, these come with detailed instructions on how to purchase bitcoins with USD and then send it over to the ransom wallet.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
Please see our community post on best practices for securing your environment against encrypting ransomware.