Ransomware as a Service (RaaS) has been growing steadily since it made its debut in 2015 with Tox. With the new Satan service, it’s easier than ever. The idea is to use this web portal to contract threat actors to create new ransomware samples for distribution via the desired attack vector. This allows any potential cybercriminal, regardless of their skill or coding knowledge, to upgrade to an encrypting ransomware business model.
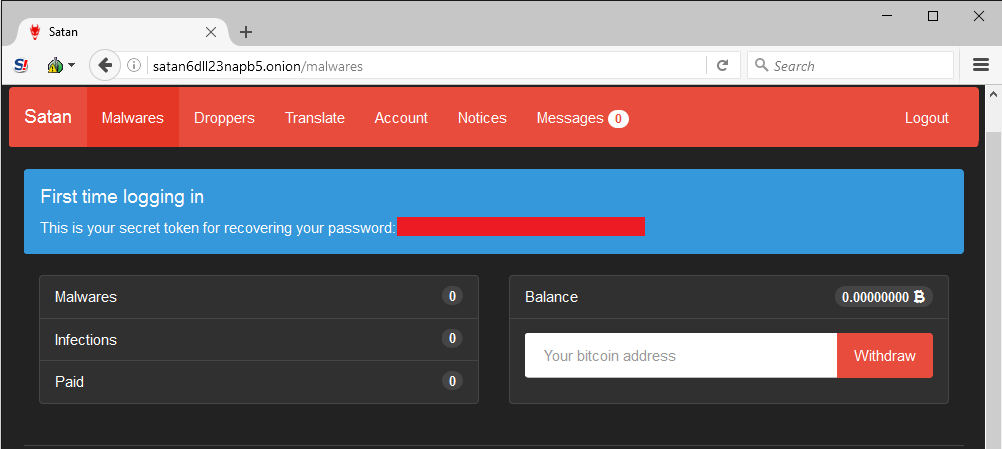
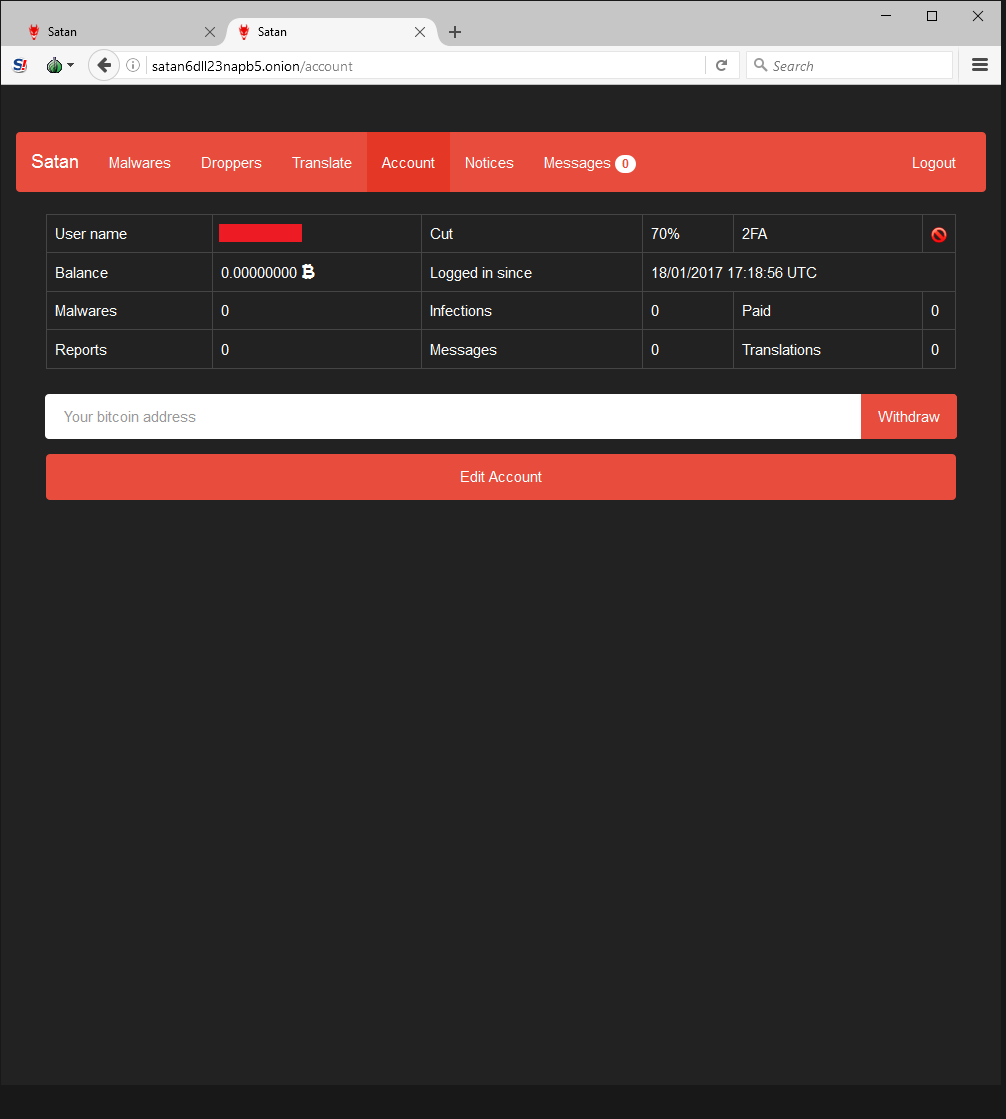
Those who join the program have a number of viewing options in the portal. The Account panel shows various stats, including how much money has been made, infection count, current share percentage, etc.
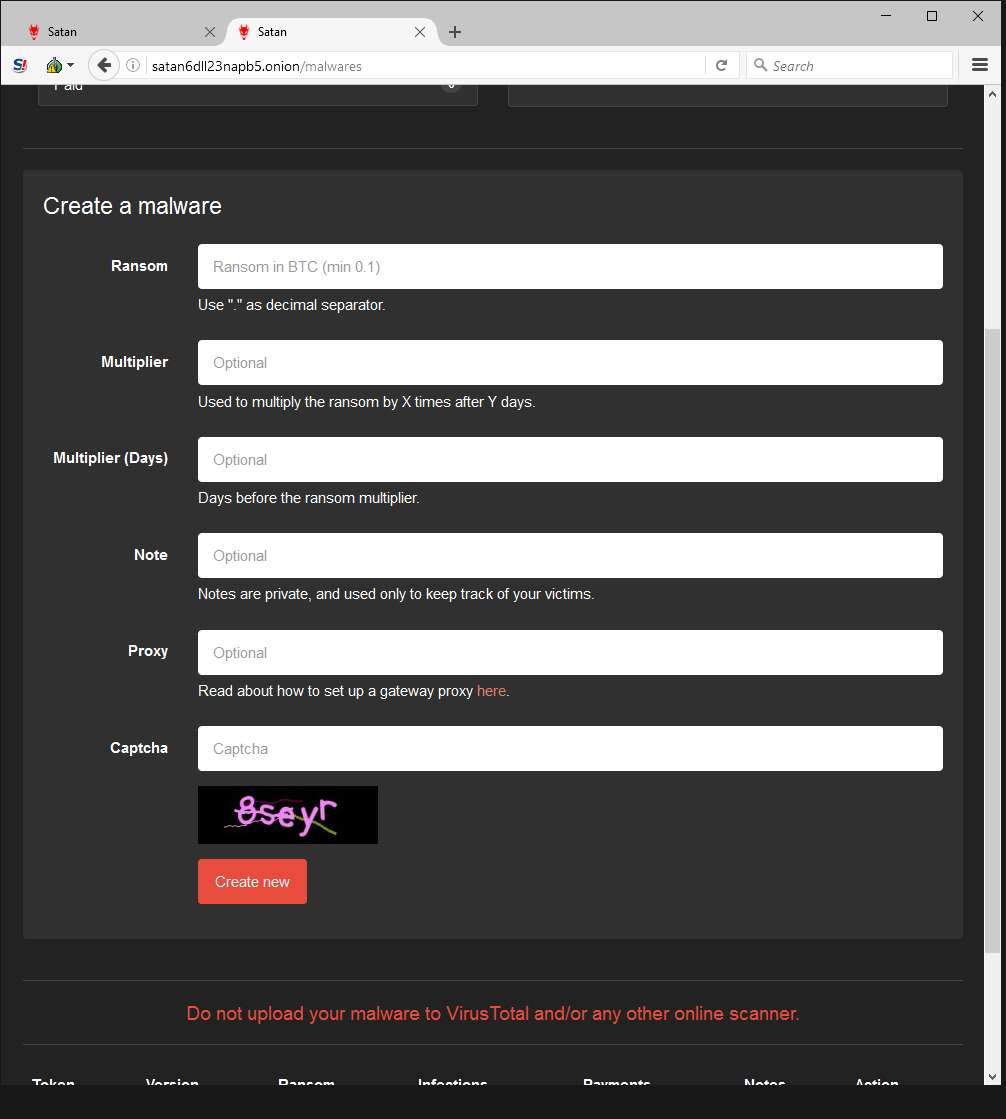
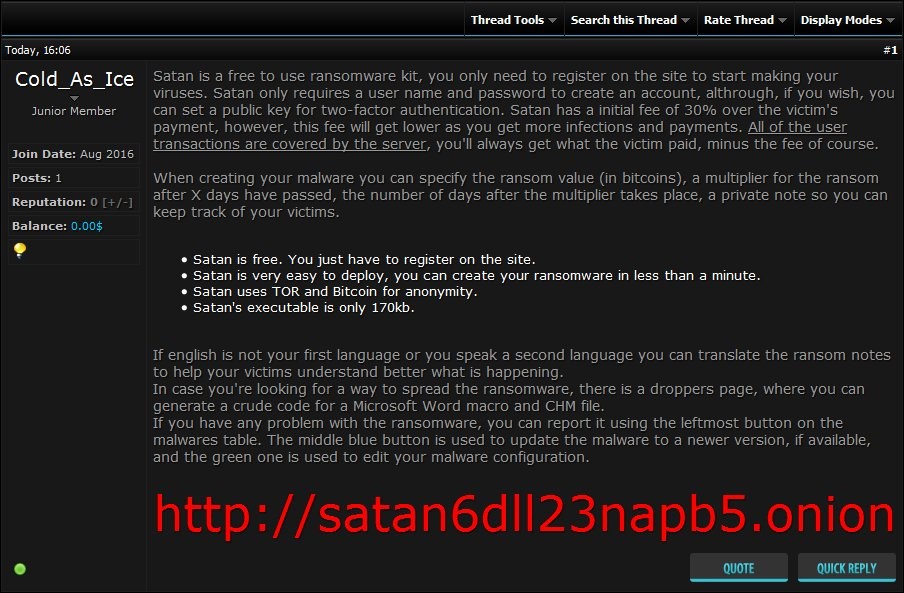
All a criminal needs to do is enter a few simple pieces of information to generate brand new malware that’s ready to infect victims. Note that the portal author specifically requests downloaded samples not be shared with VirusTotal, decreasing the likelihood that security vendors will have encountered the variant.
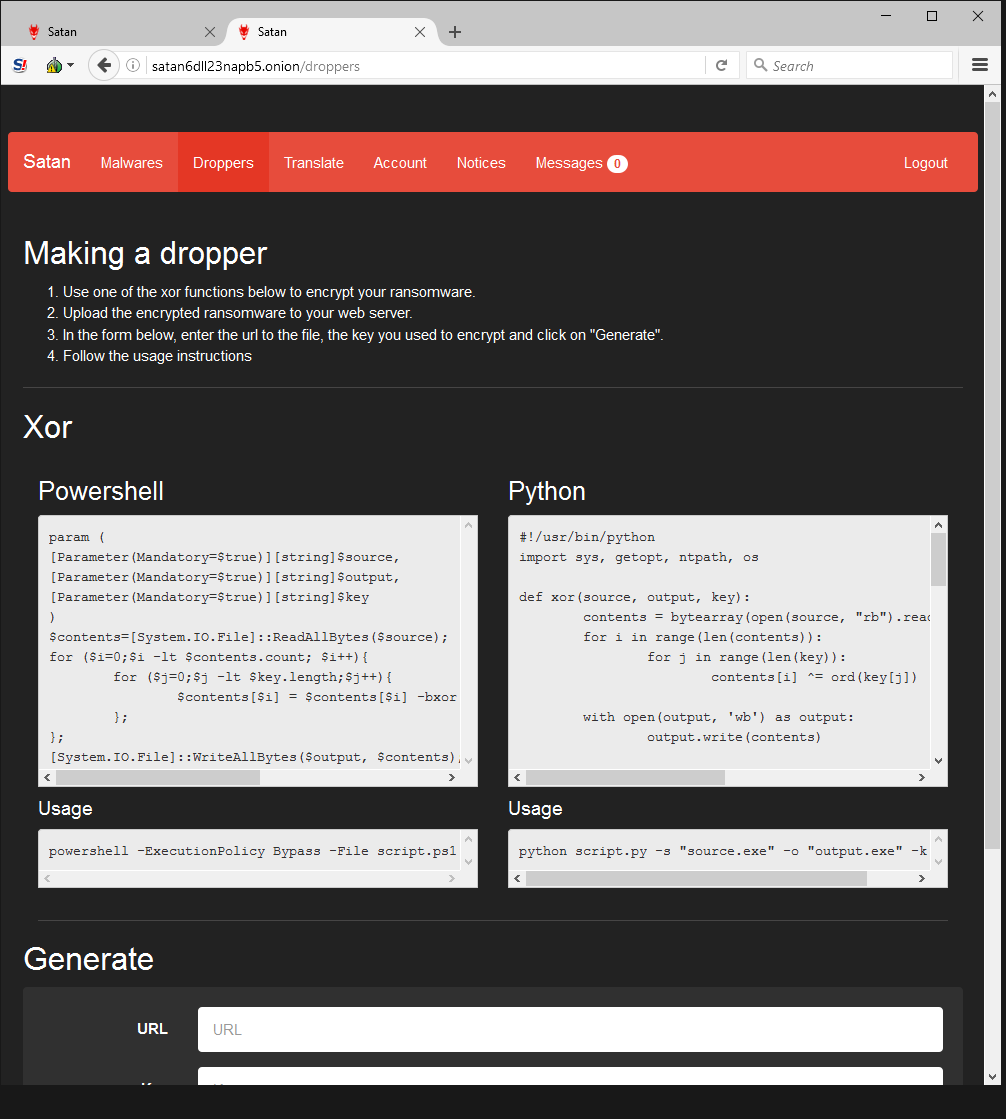
Since the darknet web portal creator takes a 30% cut of all ransoms, it’s in his best interests to make sure as many victims are infected as possible. He provides a guide with step-by-steps instructions on how to deploy malware using obfuscation techniques to avoid detection.
The author also advertises his web portal on underground forums, and explains the payload and the payout scheme. After all, affiliates’ success means he gets a bigger cut.
 Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
For best practices for securing your environment against encrypting ransomware, see our community post.







with these threats, backup is our best friend
Very good point, Abdel!
https://www.backblaze.com/blog/the-3-2-1-backup-strategy/
Warm Regards,
Josh P.
Social Media Coordinator