“Internet of things” (IoT) is a term that’s becoming increasingly commonplace in our daily lives. Internet-connected devices are being designed and implemented at a rapid clip, especially in our own homes. The internet is not just at our fingertips anymore, but also at our beck and call with smart speakers and digital assistants.
It’s easy to see why we are drawn to these cool new devices. They promise to make our lives easier and the convenience associated with some of these devices is undeniable.
But at what point are we sacrificing security for convenience?
A Brave New World of IoT Devices
Internet-connected doorbells can beam a video feed to your phone so you can see who is at your door before deciding whether or not to open it. A smart refrigerator will alert you when supplies are running low or approaching expiration while you shop at the grocery store. Smart thermostats boost efficiency and deliver monthly savings on utilities. These functions have obvious appeal for consumers.
However, some devices on the market stretch their advertised utility and convenience. Smart salt shakers, for instance, deliver voice-controlled sodium so you can avoid the hassle of salting your food the old fashioned way. Smart toasters will burn the date and weather into your bread, lest you forget an umbrella and what day it is. But with each new “convenience” promised by smart devices comes the danger of ceding some of your security.
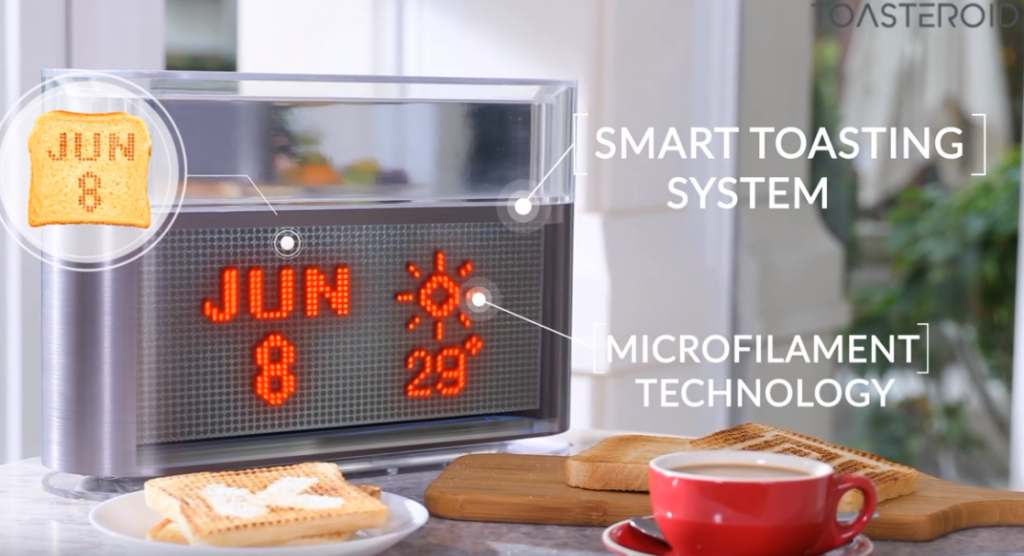
Image source: Screenshot from Toasteroid YouTube.
The underlying issue with the new and accelerating trend of buying more and more IoT devices is that the average consumer has little to no education about security when shopping for these devices. Even manufacturers can be blind to or willfully negligent of the security issues inherent to their IoT devices. It’s all about coolness and convenience—and that’s the trap.
Be wary of Unsecure IoT
Many IoT devices have little to no embedded security, and there’s little incentive for designers to consider it. One reason for that is a lack of third-party standards for evaluating IoT security. Until now, the focus has been on producing a viable product that’s functional enough to get consumers to purchase it at the right price. The “right price” is usually as inexpensive as possible, and so some quality is sacrificed.
With IoT devices, that sacrifice usually comes at the expense of security vetting in the design process. As a result, one of the biggest trends we see with cheap IoT devices is a complete and total lack of security. It’s just not something that stands out in marketing materials, so manufacturers don’t promise it and consumers don’t demand it.
That’s why care is required when shopping for new IoT devices—especially cheap ones. IoT devices like smart thermostats, smart doorbells, et cetera, usually feature competing products with varying functionalities and prices. It’s common to peruse the fanciest, most expensive devices, and then purchase an off-brand device that offers similar functionality at a much lower price.
Vendors have flooded the IoT market with devices that have so-called “hardcoded passwords.” This means that, when setting up your device, the password given to you in the instructions is the same password for every device of that model and can’t be changed. Even if the device allows you to setup a custom password, the hardcoded password will still work to log into the device.
This is basically the opposite of security. It served as the principal attack vector for the infamous Mirai botnet attack a couple years ago. It’s also how hundreds of thousands of routers have been hacked to mine cryptocurrency. Even premium IoT devices like Google’s Nest are subject to attacks, but when properly set up and used—as in by setting up two-factor authentication and not reusing their compromised credentials—they tend to be safer than their knock-off counterparts.
It’s clear now that internet-connected devices will be a part of our lives for the foreseeable future. They will help run our cities, power our grids, and yes, manage our homes. But we must be aware of what we are connecting in our home and the security of each device. Vendor regulation will also need to play its part, something already underway in California, but there is plenty more ground to cover and no time to wait. For now, it’s on the consumer to scrutinize the IoT products they bring into their home, and security should be high on their checklist.
Make sure that any internet-connected devices you buy allow you to create custom passwords, as a start. It’s also wise to only shop from reputable vendors.
Taking caution will help ensure that your smart home isn’t an easy target for cybercriminals.






