A couple of days ago our sensors picked up two separate malicious email campaigns, both impersonating Data Processing Services, that upon successful client-side exploitation (courtesy of the Black Hole Exploit Kit), drops an identical piece of malicious software.
Let’s dissect the campaigns, expose the malicious domains portfolio, connect them to previously profiled malicious campaigns, and analyze the behavior of the dropped malware.
More details:
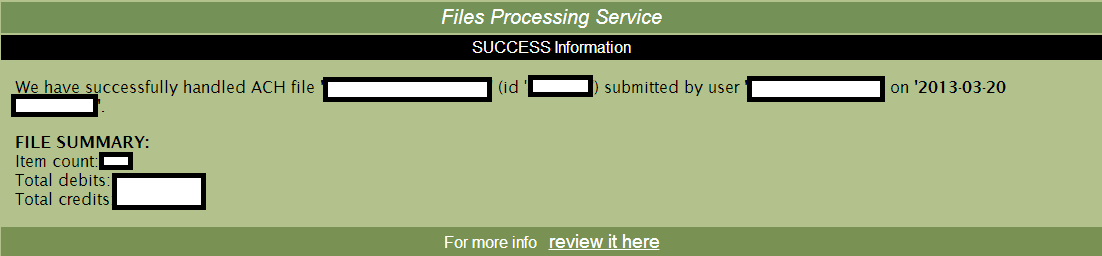
Sample screenshot of the “ACH File ID” themed spamvertised campaign:
Sample compromised URLs used in the campaign:
hxxp://may.kz/dataach_proc.html
hxxp://kimsee.co.kr/dataach_proc.html
hxxp://katja-korotynsky.de/dataach_proc.html
hxxp://raketa.molo.by/dataach_proc.html
hxxp://union-allegro.ru/dataach_proc.html
hxxp://medsintes.ru/dataach_proc.html
hxxp://bora-bora.travel/dataach_proc.html
hxxp://lexa.razor.w2c.ru/dataach_proc.html
hxxp://niko-bor.ru/dataach_proc.html
hxxp://4ord-rj.com.br/dataach_proc.html
hxxp://may.kz/dataach_proc.html
hxxp://medsintes.ru/dataach_proc.html
hxxp://zar.aero/dataach_proc.html
hxxp://www.sib-intech.ru/dataach_proc.html
Sample client-side exploits serving domain: hxxp://neo-webnet.com/kill/reading_screen.php – 24.111.157.113; 58.26.233.175; 155.239.247.247 – Email:
bannerpick45@yahoo.com
Name Server: NS1.STREETCRY.NET
Name Server: NS2.STREETCRY.NET
Sample malicious payload dropping URL: hxxp://neo-webnet.com/kill/reading_screen.php?
zwp=1n:33:2v:1l:1h&ppqf=38&zrdlkj=2v:1i:2w:2w:1o:1l:1g:1n:1i:2w&pyo=1n:1d:1f:1d:1f:1d:1j:1k:1l
We’ve already seen the same Name Servers in the following previously profiled malicious campaigns:
- Spamvertised BBB ‘Your Accreditation Terminated” themed emails lead to Black Hole Exploit Kit
- ‘ADP Package Delivery Notification’ themed emails lead to Black Hole Exploit Kit
- Fake ‘CNN Breaking News Alerts’ themed emails lead to Black Hole Exploit Kit
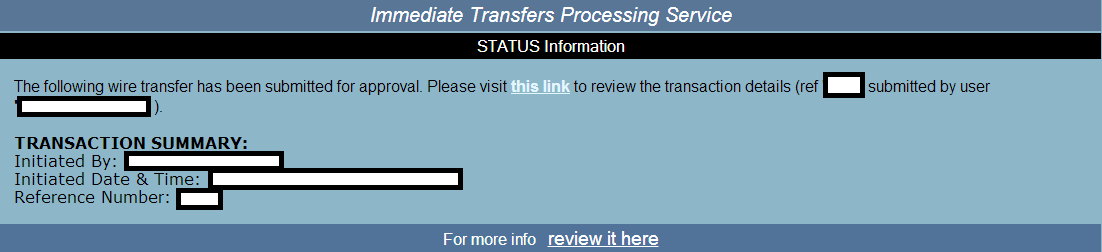
Sample screenshot of the “Terminated Wire Transfer Notification” themed spamvertised campaign:
Sample compromised URLs participating in the second “Terminated Wire Transfer Notification” campaign:
hxxp://forum.prb-fight.dp.ua/achinfo_2013_03_21.html
hxxp://rnckidsclothing.com/achinfo_2013_03_21.html
hxxp://mamnonduhangkenh1.edu.vn/achinfo_2013_03_21.html
hxxp://forum.dungeon-defenders.ru/achinfo_2013_03_21.html
hxxp://chongjisyj.com/achinfo_2013_03_21.html
hxxp://forums.iboxgames.org/achinfo_2013_03_21.html
hxxp://20h27.com/achinfo_2013_03_21.html
Sample client-side exploits serving URL: hxxp://dataprocessingservice-reports.com/kill/chosen_wishs_refuses-limits.php – 24.111.157.113; 58.26.233.175; 155.239.247.247 – Email: calnroam@yahoo.com
Name Server: NS1.STREETCRY.NET
Name Server: NS2.STREETCRY.NET
Sample malicious payload dropping URL: hxxp://dataprocessingservice-reports.com/kill/chosen_wishs_refuses-limits.php?
zwp=1n:33:2v:1l:1h&ppqf=38&zrdlkj=2v:1i:2w:2w:1o:1l:1g:1n:1i:2w&pyo=1n:1d:1f:1d:1f:1d:1j:1k:1l
Responding to 58.26.233.175 are also the following malicious domains:
crackedserverz.com
webpageparking.net – seen here
picturesofdeath.net – seen here, and here
Upon successful client-side exploitation, both of the campaigns drop MD5: 00c7693681d111c0b74121ea513abe91 – detected by 5 out of 43 antivirus scanners as
Trojan.Necurs.97.
Once executed, the sample stores the following modified files on the affected hosts:
C:Documents and SettingsAdministratorApplication DataKB00635017.exe
C:DOCUME~1ADMINI~1LOCALS~1TempexpF.tmp.bat
C:Documents and SettingsAdministratorLocal SettingsTemporary Internet FilesContent.IE589OC5JKA2MB9vCAAAA[1].txt
C:DOCUME~1ADMINI~1LOCALS~1Tempexp10.tmp.exe
C:Documents and SettingsAdministratorApplication Data9CC207909CC20790
C:DOCUME~1ADMINI~1LOCALS~1Tempexp11.tmp.exe
C:Documents and SettingsAdministratorApplication Data9CC207909CC20790
C:Documents and SettingsAdministratorApplication Data9CC207909CC20790.srv
C:Documents and SettingsAdministratorLocal SettingsTemporary Internet FilesContent.IE589OC5JKA2MB9vCAAAA[1].txt
C:Documents and SettingsAdministratorLocal SettingsTemporary Internet FilesContent.IE589OC5JKA2MB9vCAAAA[2].txt
C:Documents and SettingsAdministratorApplication DataKB00635017.exe
C:DOCUME~1ADMINI~1LOCALS~1Tempexp12.tmp.bat
Creates the following Registry Keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCFBDC89D4
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTS25BC2D7B
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTS9CC20790
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTCBA6D3F36
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareWinRAR
Sets the following Registry Values:
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> KB00121600.exe = “”%AppData%KB00121600.exe””
Creates the following Mutexes:
LocalXMM00000418
LocalXMI00000418
LocalXMRFB119394
LocalXMM0000009C
LocalXMI0000009C
LocalXMM000000D8
LocalXMI000000D8
LocalXMM000001C4
LocalXMI000001C4
It then phones back to the following C&C (command and control servers):
50.57.99.48:8080/AJtw/UCyqrDAA/Ud+asDAA/
156.56.94.212/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
85.214.143.90/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.