In times when we’re witnessing the most prolific and systematic abuse of the Internet for fraudulent and purely malicious activities, there are still people who cannot fully grasp the essence of the cybercrime ecosystem in the context of the big picture — economic terrosm — and in fact often deny its existence, describing it as anything else but an underdeveloped sellers/buyers market.
That’s totally wrong.
In this post, I’ll discuss the cybercrime ecosystem events that eventually led to the leakage of a private DIY botnet building and managing platform – with the idea to raise more awareness on the dynamics taking place within the vibrant ecosystem.
More details:
The pre-leak activity is as follows:
- A cybercriminal, apparently a member of an invite only cybercrime-friendly community, publicly announces that he didn’t have much trouble analyzing a sample of the malware bot, in particular the Domain Generation Algorithm (DGA), and consequently publishes sample source code of the process.
- Other cybercriminals start asking, ‘Why is this bot not public?’, and fellow cybercriminals surprisingly provide a working (password protected) link to a copy of the malware bot – citing that they believe the bot is buggy, uses copy and past source code from other underground releases, and that its price of $10,000 is simply not realistic
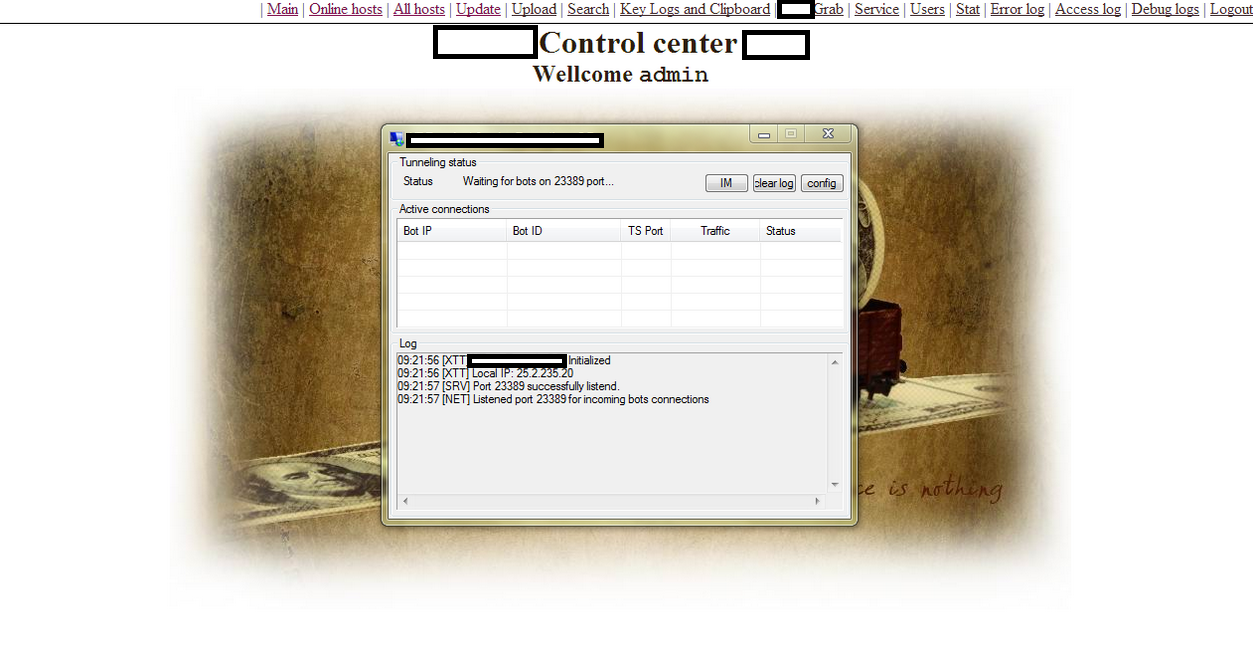
The bot exclusively relies on the Remote Desktop Protocol (RDP) for interacting with the malware infected hosts. In cases where the ports are disabled, the malware infected host will tunnel the connection on a random port. Access to the admin panel is provided by both a Web and client based GUI.
Some of the key features of the DIY botnet include:
– Displays all the statistics about the infected host (OS, Host, NAT etc.)
– The last time of the activity of the bot
– Collects information about the payment system/banking system used on the infected machine.
– Has the ability to update the version of the bot.
– Search the log files. Ability to define tags to posts for easy sorting.
– Logs errors and access to the administrative panel.
– Controls who’s authorized to view the logs of access to the admin panel.
– Controls who’s authorized to view the logs of otstuk bots.
– Fixed an error which allows to generate a domain name from the domains range, and intercept bots.
– Supported keylogger
– Can downlaod and execute additional files on the affected hosts.
Sample screenshot of the DIY botnet generating tool&command and control interface:
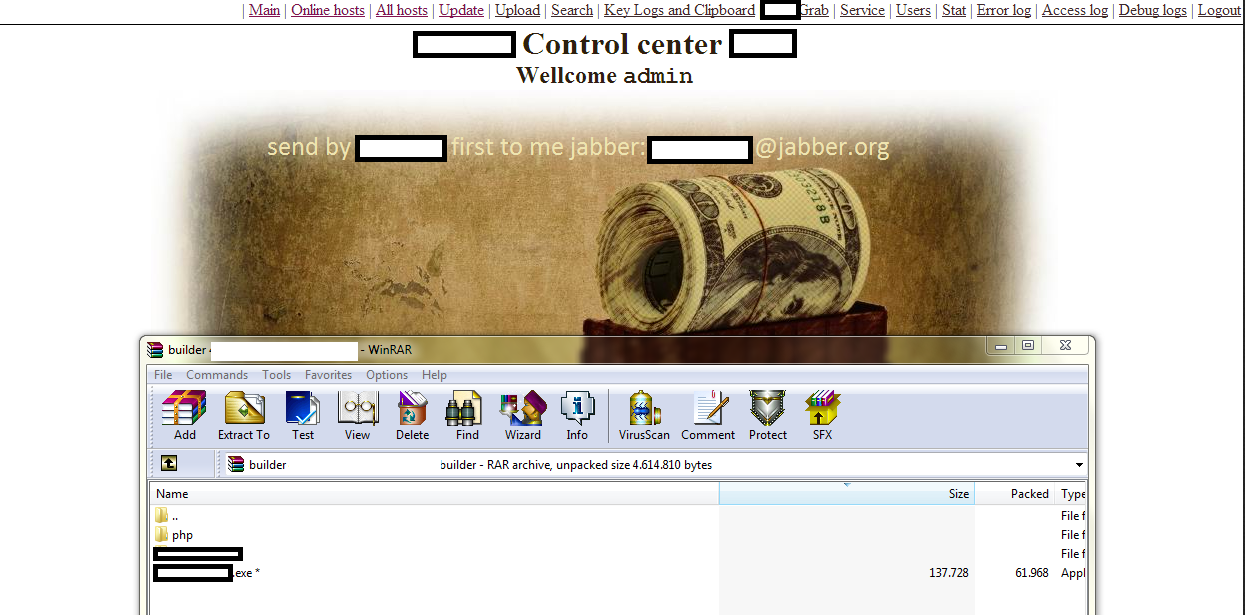
Second screenshot of the DIY botnet generating tool&command and control interface:
We’ll continue monitoring the development of this, now leaked, DIY botnet generating tool – and post updates as soon as new developments take place.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.