In a diversified underground marketplace, where multiple market players interact with one another on a daily basis, there are the “me too” developers, and the true “innovators” whose releases have the potential to cause widespread damage, ultimately resulting in huge financial losses internationally.
In this post, I’ll profile one such underground market release known as as “Zerokit, 0kit or the ring0 bundle” bootkit which was originally advertised at a popular invite-only/vetted cybercrime-friendly community back in 2011. I’ll emphasize on its core features, offer an inside peek into its administration panel, and discuss the novel “licensing” scheme used by its author, namely, to offer access to the bootkit in exchange for tens of thousands of malware-infected hosts on a monthly basis.
More details:
Sample description of the underground market release:
Features:
– Start of *.exe, *.dll (*.dll is in a pre-alpha stage) and shellcodes in a context of the chosen process.
– Start of files from a disk and from the memory* (start from memory is in a pre-alpha stage).
– Start of files with specified privileges: CurrentUser and NT SYSTEM/AUTHORITY.
– Granting the protected storehouse** for off-site (your) ring3-solutions for permanent existence in the system without need of crypt.
– Survivability of the bundle, down to a reinstallation of the system.
– All the components are stored outside of a file system and are invisible to OS.
– Intuitively clear interface of admin-panel.
– Protection against the abstraction of Admin Panel.
– Impossibility of detection of the bundle in the working system by any of known AV/rootkit scanner, owing to the use of author’s technologies of concealment. The unique opportunity of detection exists only at loading with livecd or scanning of a disk from the other computer. Thus the opportunity of detection is also extremely improbable, as own algorithms of a mutation are used.
* Start of a file from the memory allows to bypass all modern proactive protection and AV-scanners, that is, there is no necessity to crypt a file.
** Protected storehouse is the original ciphered file system in which the certain quantity of files which will be started from the memory at each start of the OS can be stored.
The bundle consists of:
– Bootkit. It is responsible for the start of the basic modules at a stage of loading of OS.
– Driver. It is responsible for all infrastructure and implements componential business-logic on the basis of so-called mod (functional unit). That is, the driver is not a legacy driver (monolithic), and consists of the set of mods that allows to operate the bundle with maximum of flexibility, and to protect (hard to reverse), update and expand it.
– Dropper. At the current moment it brake out all machines with the patches till January, 8th, 2011, except for XP x32/x64 where reloading is initiated. If the systems distinct from XP have latest updates reloading is initiated as well.
– User friendly Admin Panel.
Also I will give support to clients within the subscription fee. I provide them with:
– Development of new functionality and
– Development of new exploits for the dropper.
– Perfection of algorithms of concealment and penetration of the system.
High scalability of zerokit allow to develop additional mods and to complicate business-logic of all infrastructure.
Zer0kit have flexible update subsystem and can live in system as long as possible. Also zerokit has considered and provable logic to prevent the lost of bots.
Supported OSes:
– Windows XP SP1-SP3 (x32, x64)
– Windows Vista SP1-SP2 (x32, x64)
– Windows 7 SP0-SP1 (x32, x64)
More information about the booter, plus details about upcoming features:
1. It is possible to embed in zerokit up to 7 domains. Thus, in the case when all the domains will be for any reason unavailable, zerokit activates the mechanism for generation of domains that would allow it to locate the server.
2. Bypassing all the currently known firewalls with full blocking network, ie, if all of your domains will be in the firewall’s blacklist, it will not affect the communication to server.
3. Ability to update the first 6 months – free, then 10K per month (this is optional, if you subscribe for it) – it’s not a classic purge of AV, but the ability to make zerokit more stable, more undetected and more functional.
Rent software for installs:
1. We give you access to OUR admin panel (CONFIGURED WITH YOUR DOMAINS, BUT ON OUR SERVERS). This will be your personal place in our admin panel.
2. In this admin panel you can get pack of zerokit and begin install of it. We accept only US, CA, UK, AU installs in approximate proportions: 60/10/20/10.
3. Prepayment is 10,500 installs per week.
4. Once in our admin panel will be a specified number of bots from your installs, we give you access to YOUR admin panel (CONFIGURED WITH YOUR DOMAINS, BUT ON OUR
SERVERS) on which you can make any number of installs and load any of your software.
5. Since then, the cost is 40000 installs per month or 10500 per week. For example, you made us 40000 installs and we extend you access to YOUR admin panel for a month.
6. Installs will only be accepted within exploit packs.
7. We do not provide the crypts of zerokit’s dropper.
Over time we plan to implement:
3.a Provide a socket for your software that will allow you to work with the network with bypassing all the firewalls.
3.b P2P network for botnet, which will hide the control centers, which provide a more prolonged existence of a botnet (will be included in one of the updates).
3.c Bioskit. It’s allow zerokit to work even full formatting or changing the HD (will be included in one of the updates).
3.d New exploits for dropper. Moreover, we can prepare dropper for you with yours exploits that will be used only by you.
All this will allow you time to counter the attempts of Microsoft and AV companies to complicate the installation and operation of zerokit.
4. Verification system of files not allow any third party to take control of your botnet without a special private key to upload files. They will simply be ignored.
5. Minimal chaining with OS allows zerokit to be completely undetectable.
6. A great subsystem for downloading files, which allows the flexibility to manage and update your files on the side of botnet. This includes the launching of EXE from
memory, injecting of DLL/Shellcode into any process.
7. Keeping your files into the Encrypting File System allows to load even the detectable software.
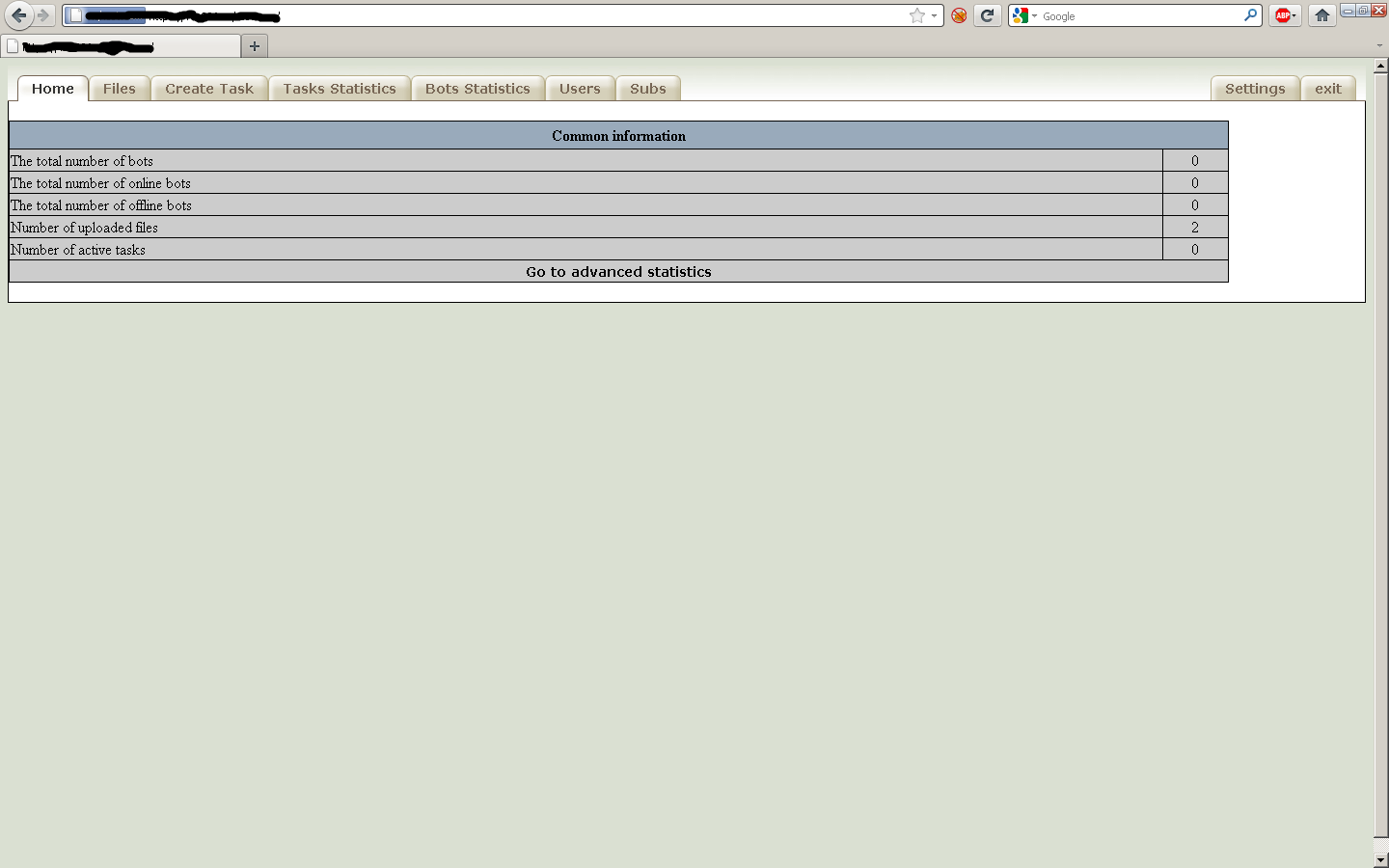
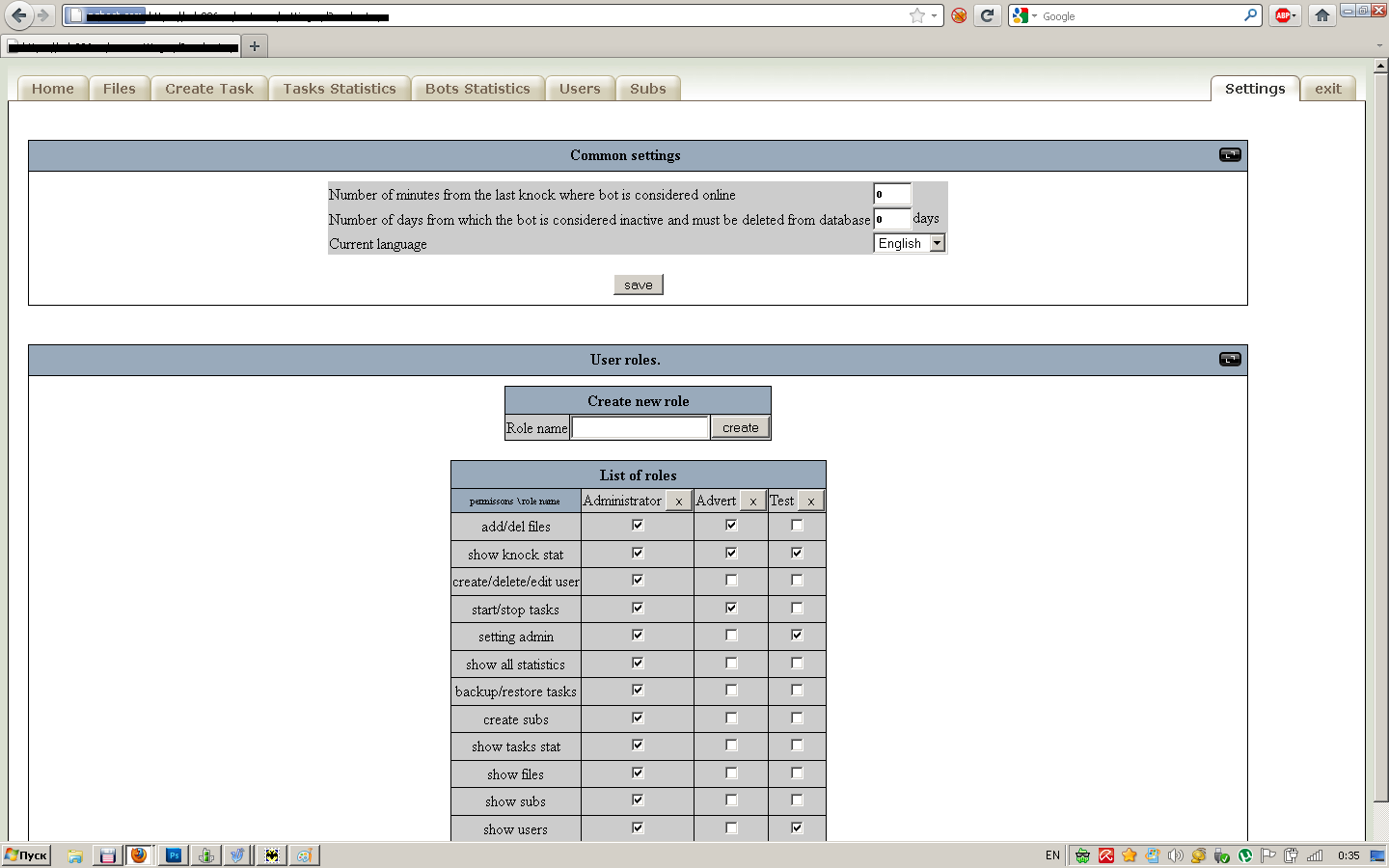
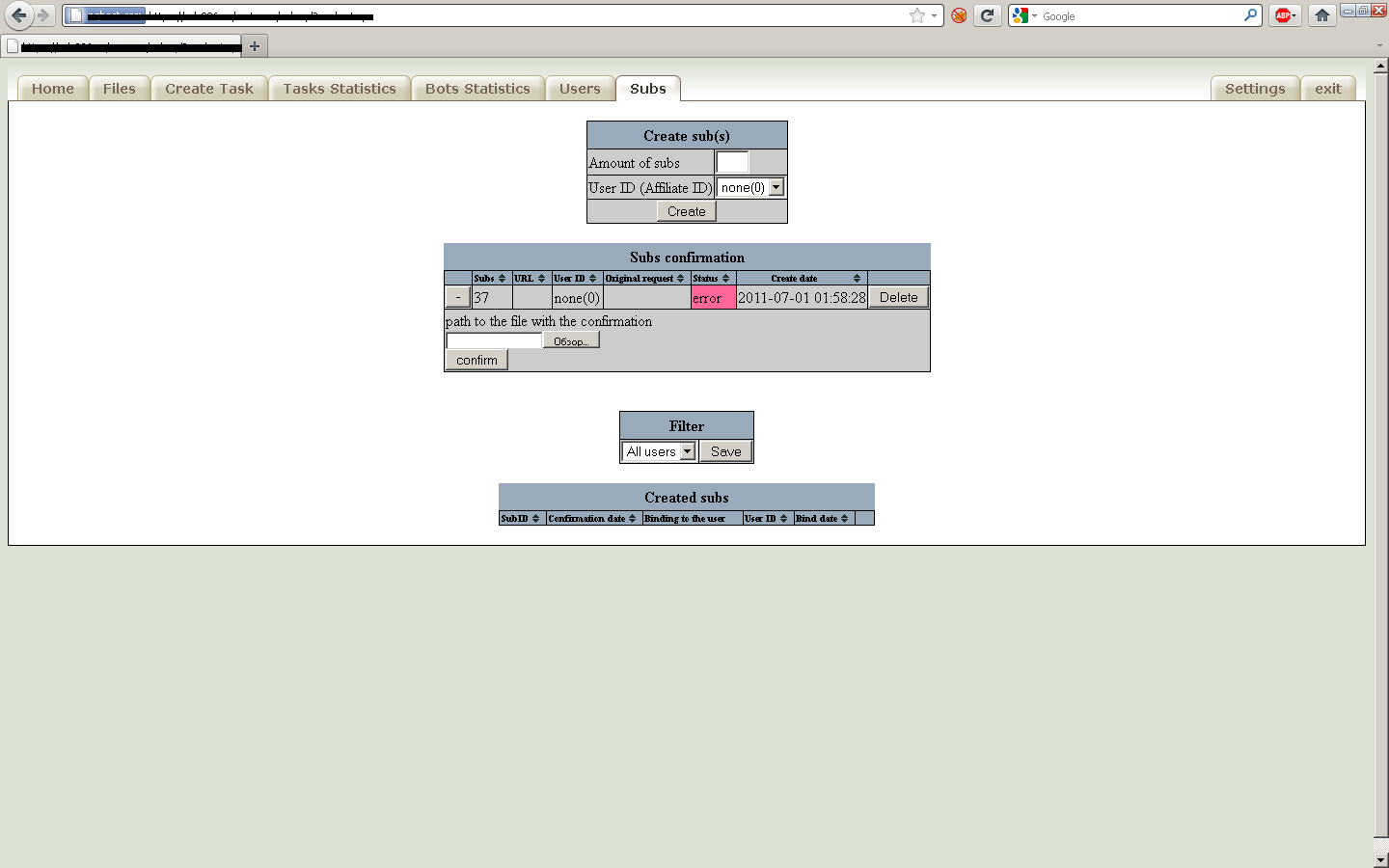
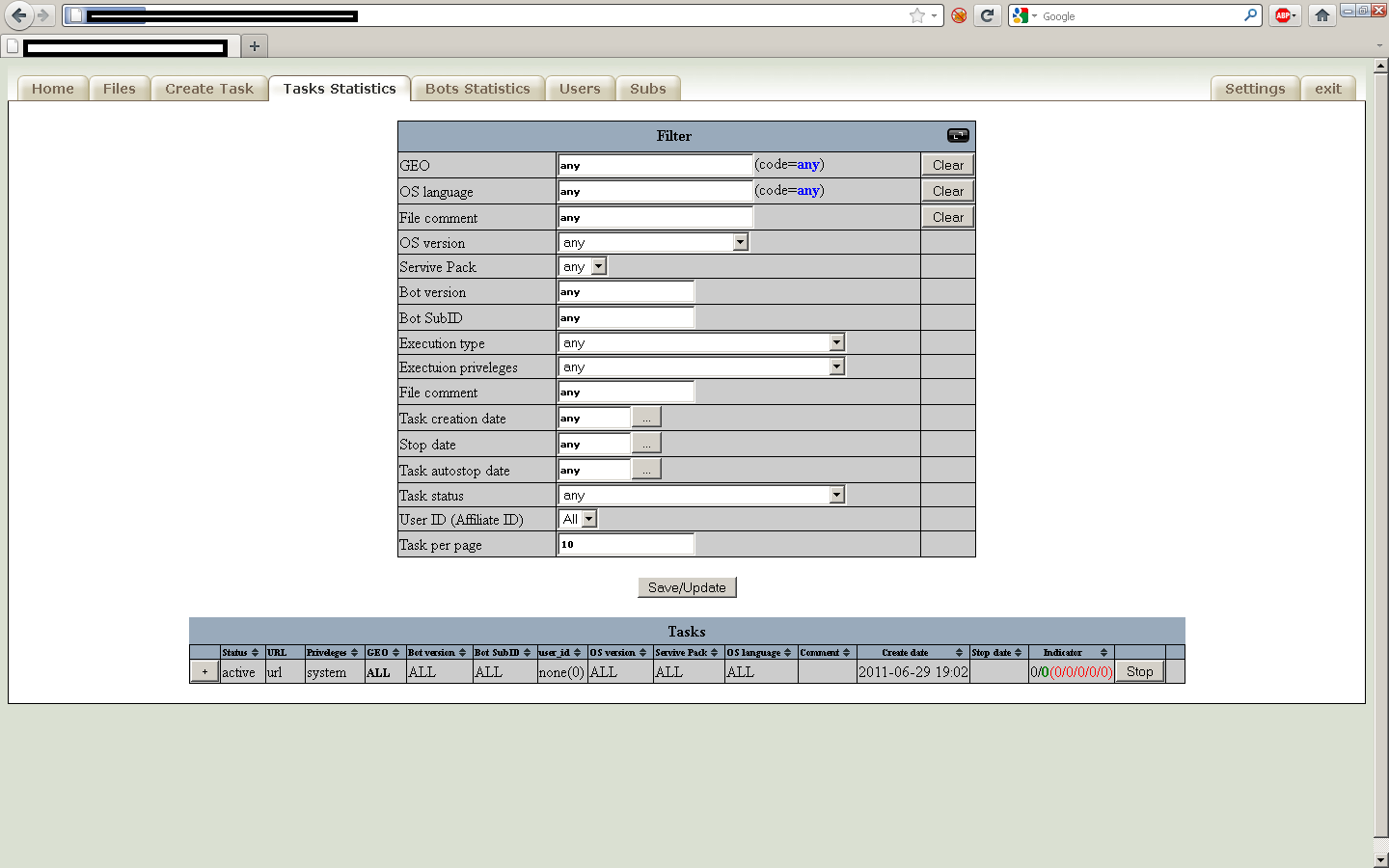
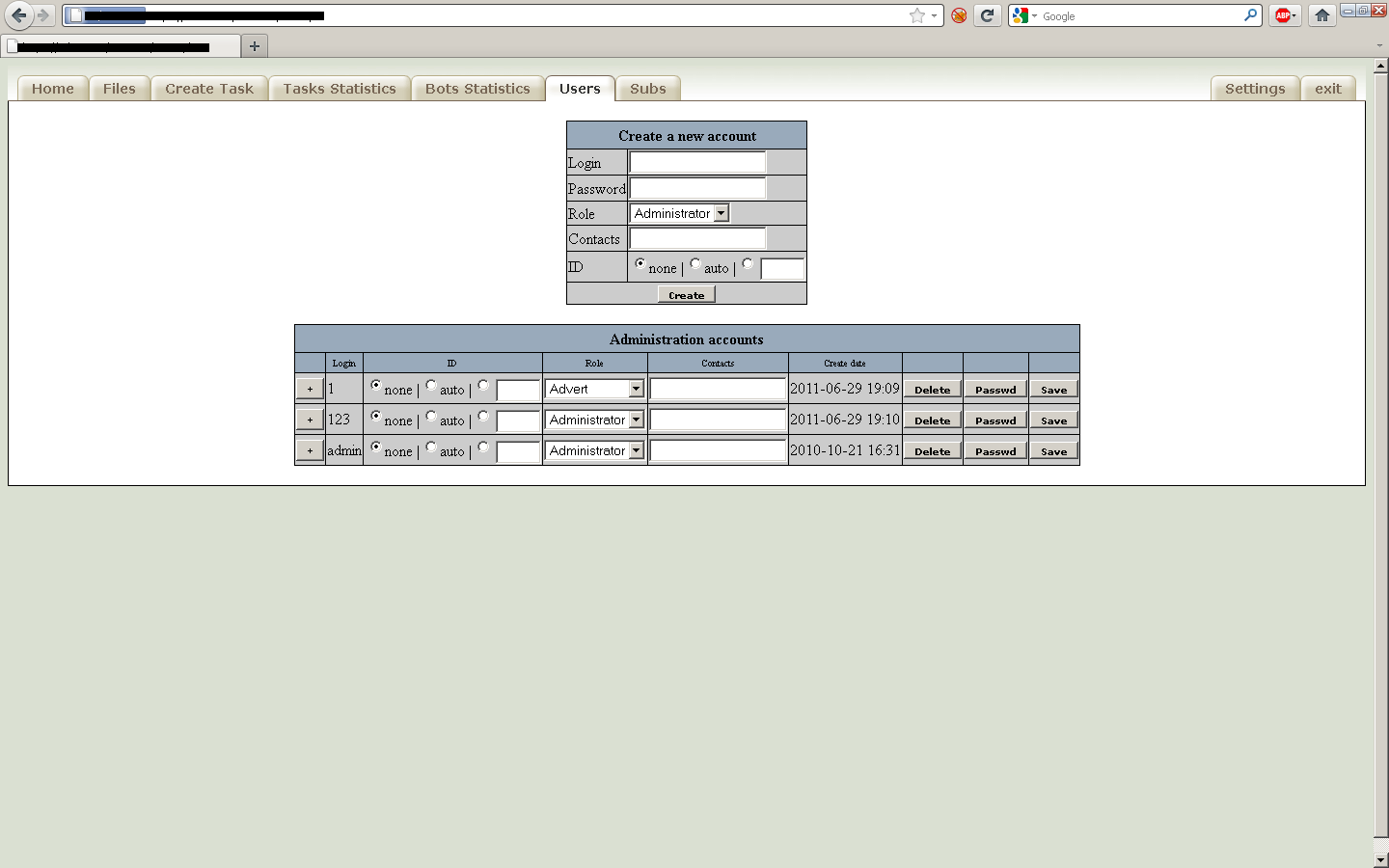
Sample screenshot of the administration panel:
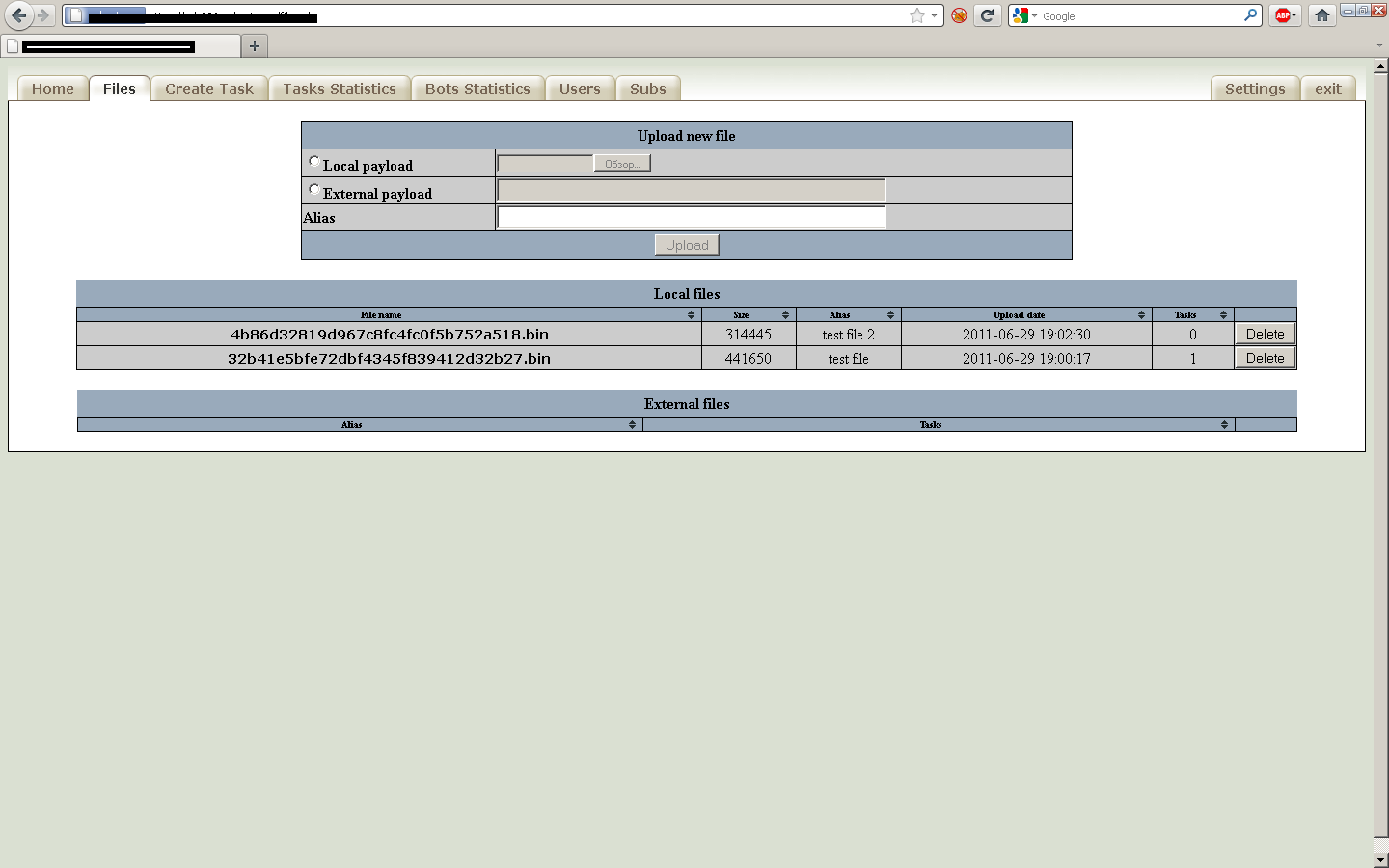
Second screenshot of the administration panel:
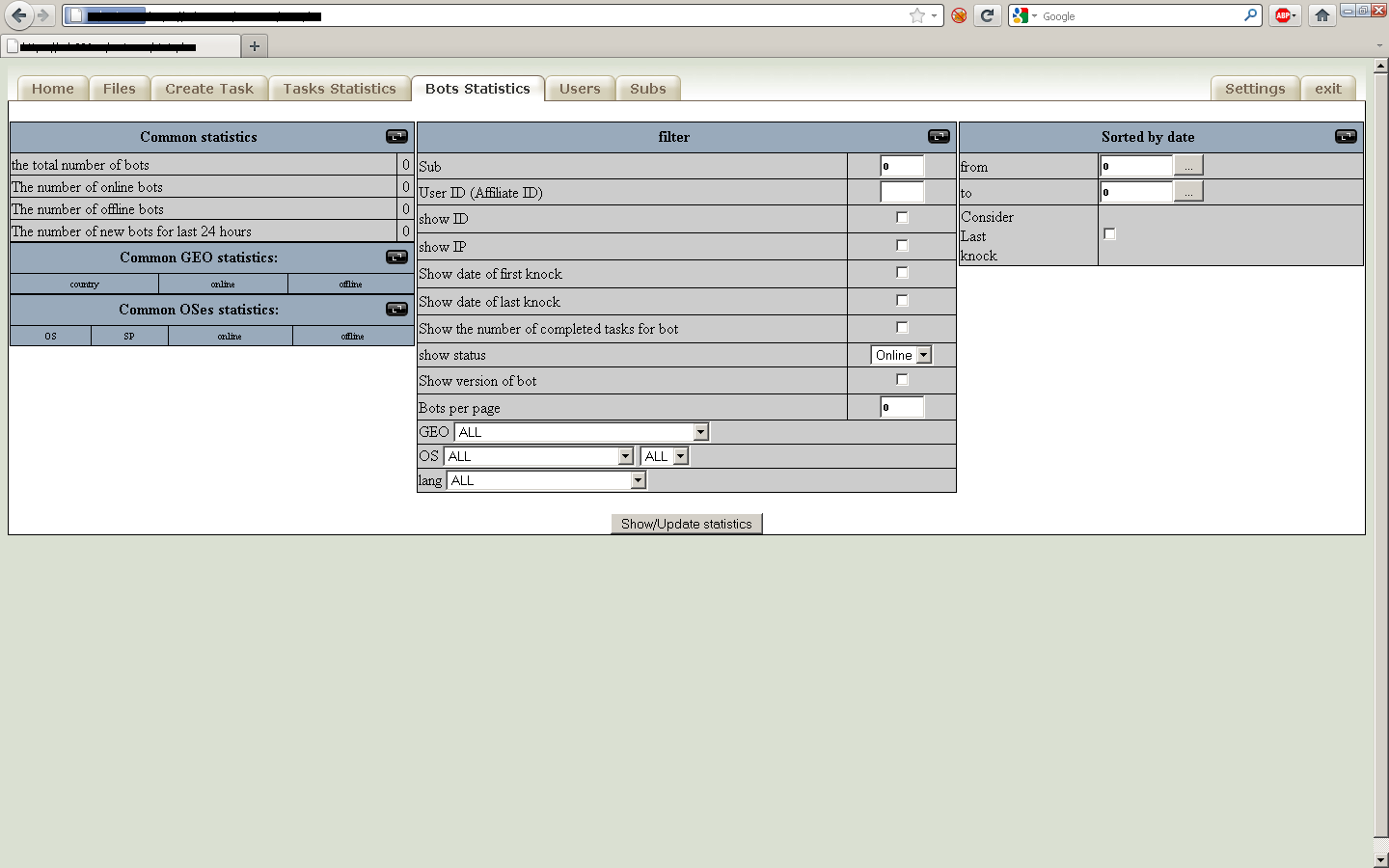
Third screenshot of the administration panel:
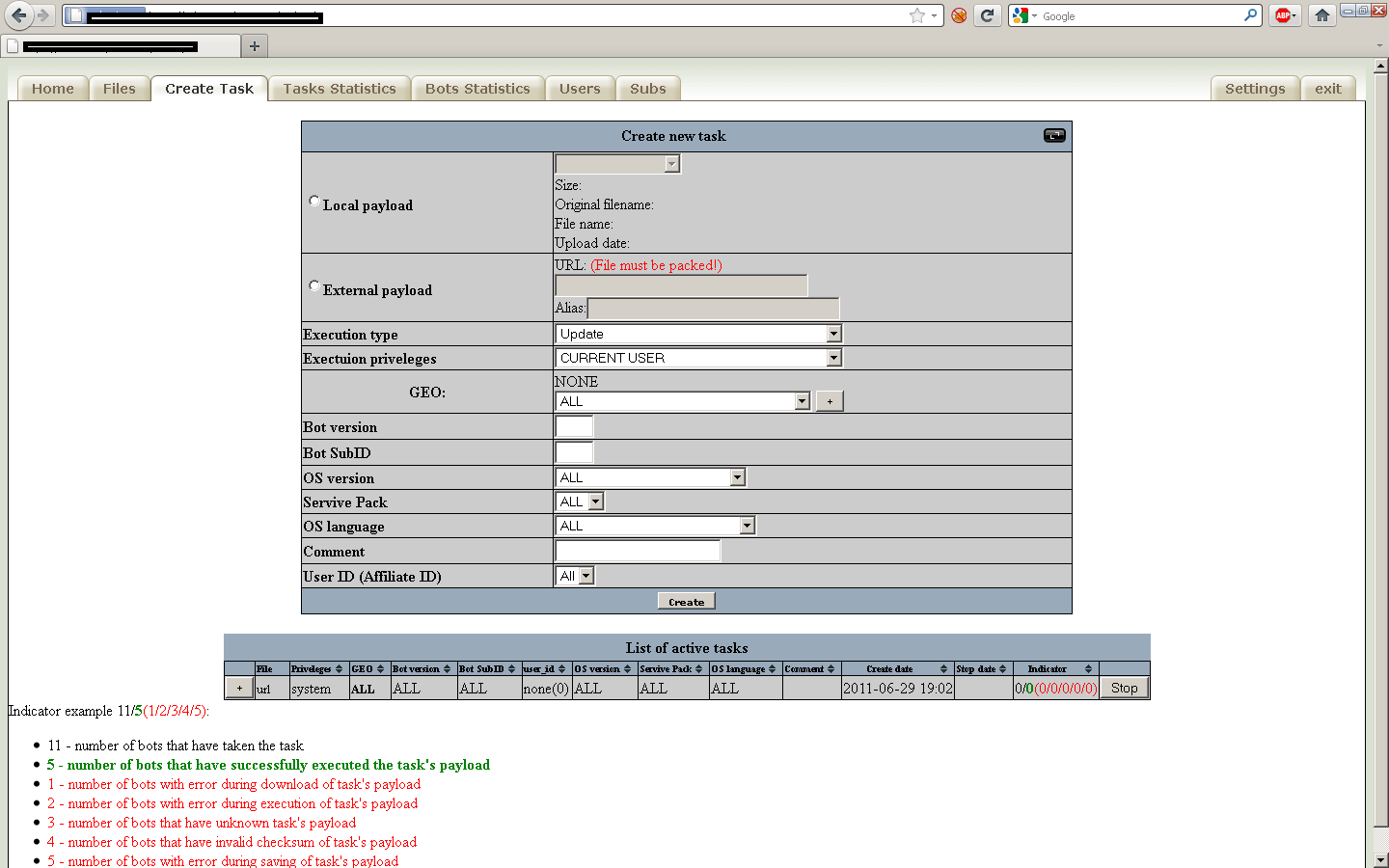
Fourth screenshot of the administration panel:
Fifth screenshot of the administration panel:
Sixth screenshot of the administration panel:
Seventh screenshot of the administration panel:
Eight screenshot of the administration panel:
Next to the fact that the group of cybercriminals behind this release are clearly interested in innovating in order for them to secure an international market share of malicious activity, they also attempt to achieve ‘asset liquidity’ by offering access to their release to those cybercriminals who can supply tens of thousands of malware-infected hosts to them on a monthly basis. Naturally, these very same cybercriminals will multi-task through double or triple layer monetization tactics utilized on the malware-infected hosts, the same malware-infected hosts that will be then monetized by the authors of the bootkit.
This underground market proposition represents a good example of OPSEC (Operational Security) aware gang of cybercriminals, clearly possessing sophisticating coding capabilities, which combined with the novel customers acquisition model, indicates a decent understanding of the dynamics of the cybercrime ecosystem.
We’ll continue monitoring its development, and post updates as soon as new features get introduces.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Thanks for the information, great report as usual. Can you describe how the exploits used in this advanced threat may be prevented and/or eradicated? If traditional signature-based antivirus are unable to detect or remediate, and native firewall protection is useless, is Webroot’s platform successful? And if so, how? Anymore, it seems the evolution of the threat landscape continues to develop advanced code to bypass those measures, so what do users do? Seems we need a way to carefully evaluate the file structure almost in real time, and somehow assess drive end sectors despite zero-byte buffer response. I continue to see increasing clients that require rebuild of the MBR and even see reinfection after factory-reset of drives and OS. I’ve yet to see reinfection from reload from a system image, thank goodness. Are you employing something more effective than trusted installer, something at the lowest levels to “sense” misbehavior? I know, lots of questions…try me!