By Dancho Danchev
Cybercriminals are currently spamvertising tens of thousands of emails impersonating American Airlines in an attempt to trick its customers into thinking that they’ve received a download link for their E-ticket. Once they download and execute the malicious attachment, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals behind the campaign.
More details:
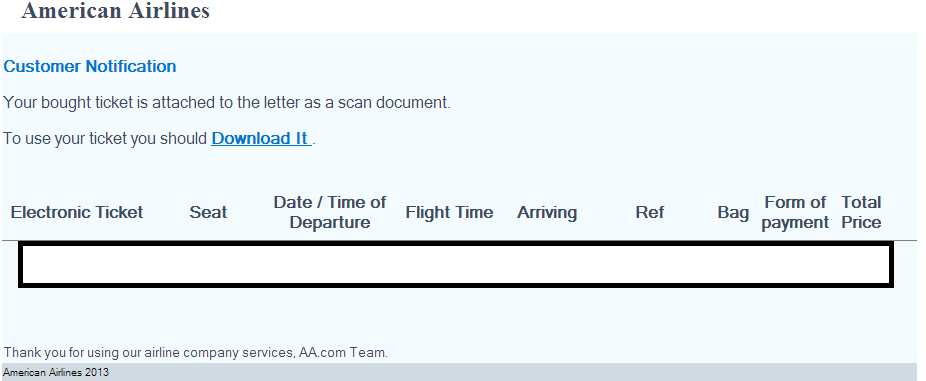
Sample screenshot of the spamvertised email:
Sample compromised URLs participating in the campaign:
hxxp://www.biketheworld.net/components/.k9q1kh.php?request=ss00_323
hxxp://www.bikeforcourage.com/components/.0y5ygh.php?request=ss00_323
hxxp://www.bindsteinhuette.info/components/.pyhhrz.php?request=ss00_323
hxxp://www.bioks.info/components/.woos4r.php?request=ss00_323
Detection rate for the malicious executable: MD5: f17ee7f9a0ec3d7577a148ae79955d6a – detected by 10 out of 46 antivirus scanners as Mal/Weelsof-D
Once executed, the sample phones back to the following C&C servers:
202.52.136.27/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
80.67.6.226/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
80.67.6.226/private/sandbox_status.php
78.142.63.165/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
202.52.136.27/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
178.32.136.84/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
180.235.132.29/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
94.23.254.90/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
91.121.156.162/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
94.23.254.90/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
68.233.32.145/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
68.233.32.146/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
180.235.133.70/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
87.106.26.231/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
94.23.254.90/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
68.233.32.145/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
193.23.226.15/798475540DFA75FE5945D24FA5CBF9A5578EB293595AAF8C6E445FAE8464227079DAED1AC61062B271D16CAB2E483FB5830A72A3104DF0644E2AEC46CB62E9598B13036FBDD8DE367F41EF7D2406F547
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.