Everyday, new vendors offering malicious software enter the underground marketplace. And although many will fail to differentiate their underground market proposition in market crowded with reputable, trusted and verified sellers, others will quickly build their reputation on the basis of their “innovative” work, potentially stealing some market share and becoming rich by offering the tools necessary to facilitate cybercrime.
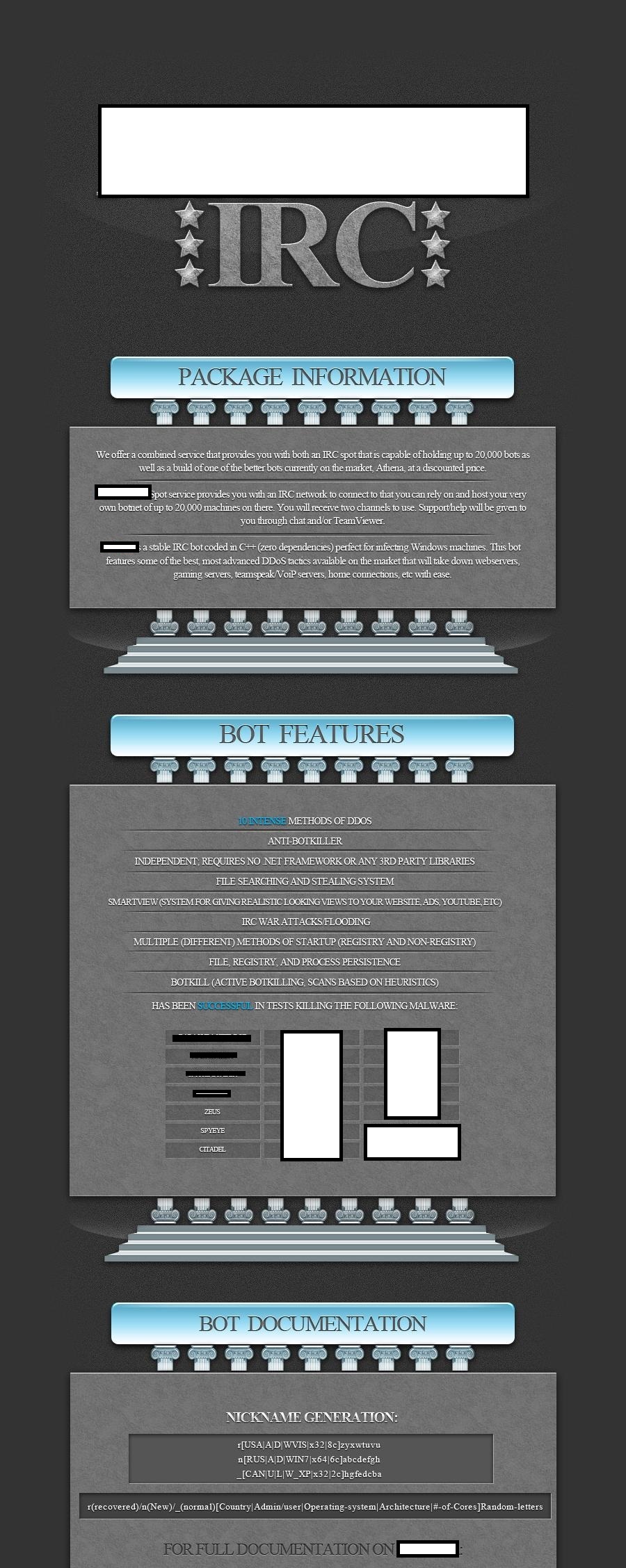
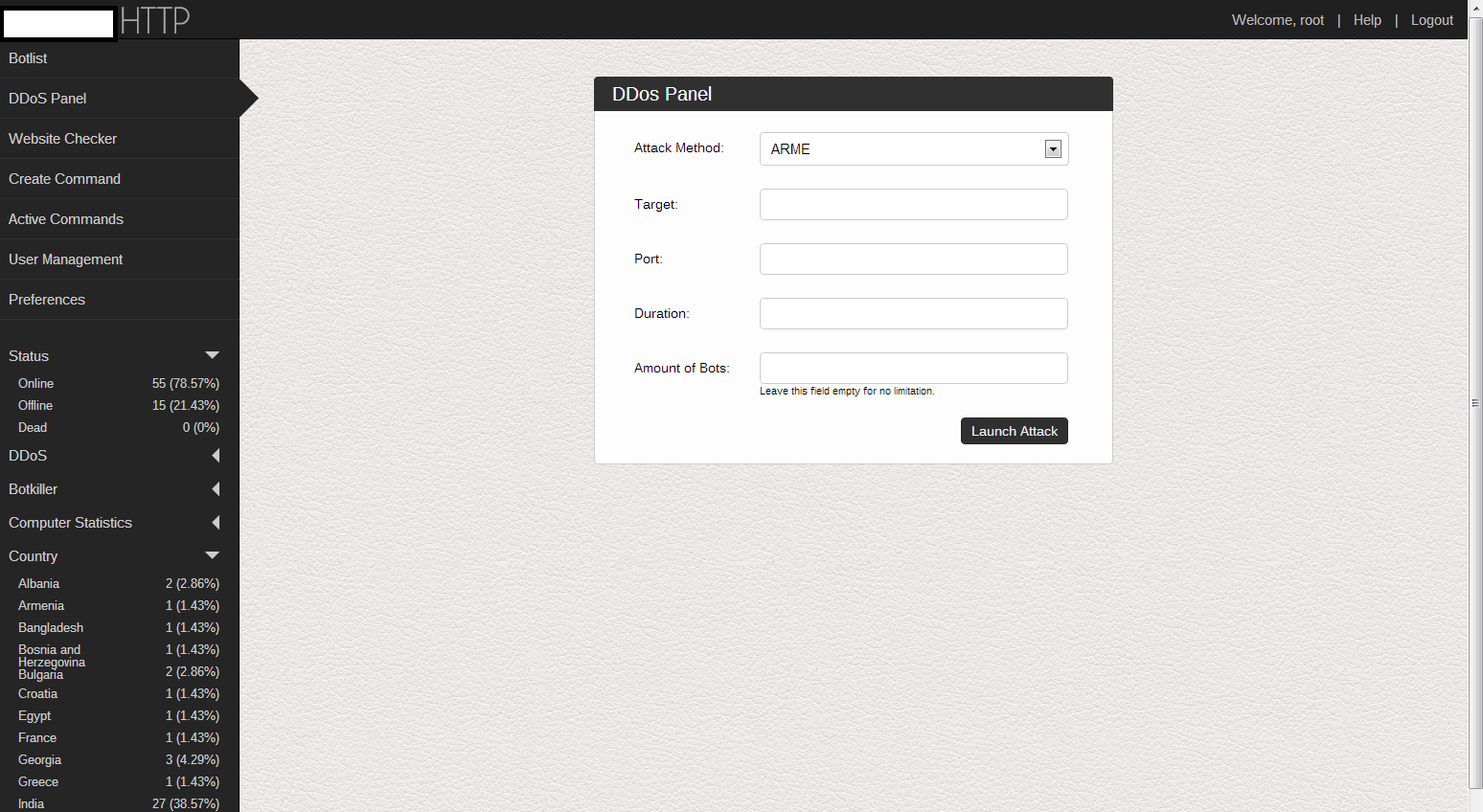
Publicly announced in late 2012, the IRC/HTTP based DDoS bot that I’ll profile in this post has been under constant development. From its initial IRC-based version, the bot has evolved into a HTTP-based one, supporting 10 different DDoS attack techniques as well as possessing a featuring allowing it to heuristically and proactively remove competing malware on the affected hosts, such as, for instance, ZeuS, Citadel or SpyEye.
More details:
Sample screenshots describing the features of the bot, a peek inside its command and control (C&C) interface, as well as screenshots of the bot in action:
What about the price? The IRC version goes for $100, while the HTTP version goes for $300. Managed services are available for IRC ($10), and bullet proof domain ($15).
Thanks to its price, the DDoS bot managed to generate quite a bit of commentary on behalf of fellow cybercriminals across multiple cybercrime-friendly communities, resulting in a cracked version available exclusively to members of these communities. What we’ve got here is yet another example of a technically flawed licensing model for malicious software, allowing fellow cybercriminals to undermine the vendor’s entire business model. Whether competing vendors of malware/crimeware releases targeted by this bot will take action or not, will entirely depend on the market share that it succeeds in securing, once again, thanks to its affordable price.
We’ll continue monitoring the tool’s future development, in particular whether or not it will migrate to a less noisy — like IRC — C&C communication models, taking into consideration the fact that its latest version has indeed migrated to a HTTP-based C&C.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.