Largely thanks to the increasing availability of easy to use DIY (do-it-yourself) DDoS bots, we continue to observe an increase in international cybercrime-friendly market propositions for ‘DDoS for hire’ services. And whereas these services can never match the bandwidth capabilities and vendor experience offered by their Russian/Eastern European counterparts, they continue to empower novice Internet users with the ability to launch a DDoS attack against virtually anyone online.
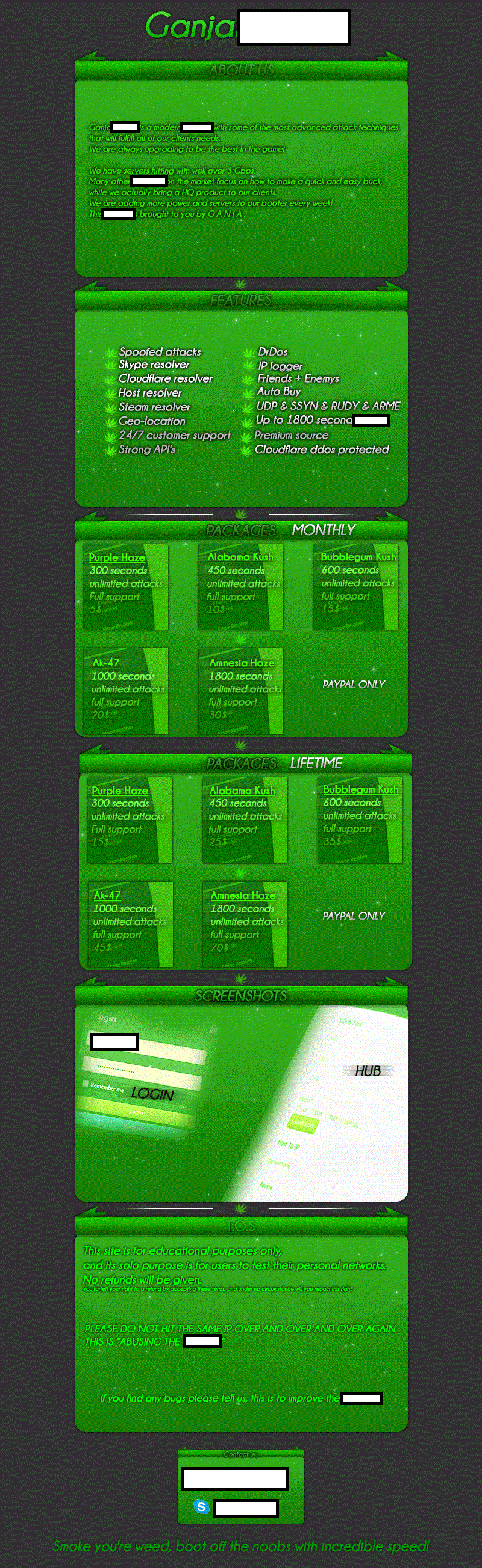
In this post, I’ll profile a recently launched marijuana themed DDoS for hire service and emphasize on how, despite it’s built in pseudo-anti abuse process, the service is prone to be abused by novice cybercriminals looking for cost-effective ways to cause disruption online.
More details: Sample screenshot of the actual advertisement:
Potential customers can choose between a variety of different pricing schemes, each of them based on the total number of seconds for the eventual DDoS attack that they’d like to launch. The service also offers Skype IP resolver, Cloudflare resolver, Steam resolver and Host resolver, in an attempt to make it easier for its customers to launch the DDoS attack.
Sample graph of the service in action:
The overall availability of such services can be compared to the rise of commercial RATs (Remote Access Tools/Trojans), in particular their attempts to add layers of legitimacy to their international cybercrime market propositions.
Just like Remote Access Tools, which often come with built-in spreading and rootkit functions, these ‘DDoS for hire’ services have TOS (Terms of Service), which usually state that the offered bandwidth and variety of DDoS attack techniques are only provided in order to empower network administrators with the necessary tools to test the DDoS resilience of their networks. However, why a network administrator would want to resolve a Steam/Skype/Cloudflare user’s IPs to launch a DDoS attack remains unclear.
We expect to continue observing an increase in similar ‘DDoS for hire’ types of international underground market propositions, a clear indication of just how easy it has become to generate and operate a botnet online. Everyone can do it, and everyone is doing it.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








DIY Bots is mainly for small attacks, often used to boot opponents in online games and online tournaments. However, a 30min outage can still hurt most businesses. Let’s hope they investigate and arrest the main providers soon.