By Dancho Danchev
We’ve just intercepted a currently circulating malicious spam campaign consisting of tens of thousands of fake ‘Export License/Invoice Copy’ themed emails, enticing users into executing the malicious attachment. Once the socially engineered users do so, their PCs automatically become part of the botnet operated by the cybercriminals behind the campaign.
More details:
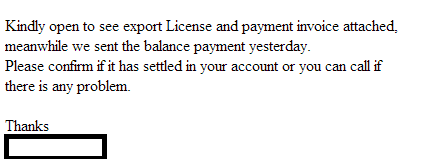
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment – MD5: 5e2c658096f7e2360b3ea15c093ef07e – detected by 26 out of 46 antivirus scanners as PWS:Win32/Zbot.gen!AM; HEUR:Trojan.Win32.Generic.
Once executed, the sample starts listening on port 1581. It also marks its presence on the affected PCs, through the following Mutexes:
Local{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Local{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global{32644819-7878-C989-11EB-B06D3016937F}
Global{32644819-7878-C989-75EA-B06D5417937F}
Global{32644819-7878-C989-4DE9-B06D6C14937F}
Global{32644819-7878-C989-65E9-B06D4414937F}
Global{32644819-7878-C989-89E9-B06DA814937F}
Global{32644819-7878-C989-BDE9-B06D9C14937F}
Global{32644819-7878-C989-51E8-B06D7015937F}
Global{32644819-7878-C989-81E8-B06DA015937F}
Global{32644819-7878-C989-FDE8-B06DDC15937F}
Global{32644819-7878-C989-0DEF-B06D2C12937F}
Global{32644819-7878-C989-5DEF-B06D7C12937F}
Global{32644819-7878-C989-95EE-B06DB413937F}
Global{32644819-7878-C989-F1EE-B06DD013937F}
Global{32644819-7878-C989-89EB-B06DA816937F}
Global{32644819-7878-C989-F9EF-B06DD812937F}
Global{32644819-7878-C989-E5EF-B06DC412937F}
Global{32644819-7878-C989-0DEE-B06D2C13937F}
Global{32644819-7878-C989-09ED-B06D2810937F}
Global{32644819-7878-C989-51EF-B06D7012937F}
Global{32644819-7878-C989-35EC-B06D1411937F}
Global{32644819-7878-C989-55EF-B06D7412937F}
Global{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
It then phones back to the following C&C servers:
190.202.83.105
201.209.58.176
79.184.18.48
76.226.114.217
78.131.50.190
94.43.213.17
94.240.232.143
2.40.193.124
89.123.209.123
190.238.117.97
114.26.96.221
107.217.117.139
188.121.218.120
108.74.172.39
87.10.213.155
5.20.67.209
199.30.90.80
92.228.162.163
90.156.118.144
82.211.180.182
83.29.15.37
84.59.131.0
188.169.204.227
85.108.124.87
108.220.162.134
188.169.52.202
190.5.76.35
74.92.13.177
107.193.222.108
93.45.117.139
The following malicious MD5s are also known to have phoned back to the same C&C servers over the past 24 hours:
MD5: 145e8f06bda983b07420dfffff5044ef
MD5: 686a9166be128dec512df4d4555bba19
MD5: 5e3cdbc8ef211a9b4d7b2922f40c3983
MD5: 5d79409951d48bb79777cbf82304ae98
MD5: a8f9d987c9d8483256ddeef241693863
MD5: 25d4a2e3e09875c3d3737f4efb6ace54
MD5: 84b7454358936846f8490355c2142e8a
MD5: 2737b117a12adfada3269edd6c4ffd2f
MD5: 371d7ecb5aaa071dd50102ccb9de3959
MD5: cfd4840196eb85a41e9d2412e90d292f
MD5: 4c7a90ce5db5ffece1cb29c9ffca26ee
MD5: 27f746e57f50eebfed65de1fdf3352d2
MD5: 27b4adf726331e56f0d1c8206b6803ba
MD5: c9d386332c81d4d520bdaa8163ca3f24
MD5: d3a76daa412e4ed3f418e5dd8b616291
MD5: e90ee04802083fc390f271e57fe1cfe1
MD5: b5f08d912930a16501d3eb8485bf006f
MD5: dc388d9d63e40e8256163cd3ea9e17c0
MD5: 28b735bd54be1155fd98fb0979e223c8
MD5: dcda68aa63578cfe1b44087bb377062e
MD5: fdcd97d2e4021dea6c2bb527615ffa95
MD5: f7d8e22eaf697842660a04a54ca1148f
MD5: 02c8996cae23885e7c46fa8bb19ae8bb
MD5: 1208af17b9d6c048f2ed263a4e1bbeba
MD5: de5049d03fb0362ca1b7e629bbaf2445
MD5: c91516c167087bbc594c0ce03e3fdd80
MD5: afad143961e03433f3a162d2ebefcaa0
MD5: 036071e7eb10db7aaf19aa0f80459eb6
MD5: 44a1947ad74d3aa201172af1543540e3
MD5: 652ccf58e2e55afd368fdbf4d0764464
MD5: c34ac13d8f10b543dbc397c9eb1df662
MD5: c6cd8a84dabc1433a1716be7d3569b9e
MD5: 5ffcdc86ac55341b31352c0239685259
MD5: 3b47744946aecf8b5942ce2d54110ea0
MD5: 85ba4d6b434e8a92fa61219197286bee
MD5: 2548c5635cd8da2d6699e0c043c7ecf8
MD5: b7042a2214622636d3bfb6725292c433
MD5: 66d0d4339e6f9aa56bd711cc11158233
MD5: aa0de4ca13dc9a78e745531e75e7568a
MD5: 3473820f72e3be1315c887fc676cac19
MD5: 61ec7945c6bbae500e3f9fef9280796f
MD5: 4aa49ed506d0bc4691337e26ec7e930e
MD5: 450f7fca26c1fc37e830703e779cd032
MD5: 65eaabda2e348adffe2a7a2974ce96b6
MD5: d479b413253a54a50a75bfef18e14b52
MD5: 08e6dbd2edca1a85c392ba84c049740c
MD5: 46cd159be7c00e888ed8f571ade012c3
MD5: 78675ed06f2a9d0812b916aa0bb148e0
MD5: cd008ad25ee7387ce404e6a5b7df4810
MD5: 9d74885213df255b254f0424dc374b07
MD5: 494206750cb7c1e8ff1027a8d1f8ef40
MD5: 8ab3d7624e7415d0c45aea51db1deef4
MD5: f1d183c26058ab94ba0d7584b0ee412f
MD5: eaae570a67c5de0a657a5af4be988384
MD5: 858d32e2b8cf4dab9d5b9fb5352dce05
MD5: 06b236b967d1155aaca904f87a6047ae
MD5: e25d75d33395de12acd0197f8fdf5cd5
MD5: 3f57b27fe6198159288018e5ef71906b
MD5: 96d0663f49666a93ccba296130477378
MD5: d52db559de88d8ed6b10248dd1249a42
MD5: 06e1d9bbfef6d7af9a032e78c8432c6c
MD5: 35b299d08874ae755eeb72b728e5b918
MD5: 06e1d9bbfef6d7af9a032e78c8432c6c
MD5: 35b299d08874ae755eeb72b728e5b918
MD5: c356a37cb3ead0eff1c5b32c8ed33f76
MD5: 438c49178f2288bf9e1b2167ca93e0c9
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.