Cybercriminals continue releasing new, commercially available, stealth Bitcoin/Litecoin mining tools, empowering novice cybercriminals with the ability to start monetizing the malware-infected hosts part of their botnets, or the ones they have access to which they’ve purchased through a third-party malware-infected hosts selling service.
What’s so special about the latest mining tool that popped up on our radar? Let’s find out.
More details:
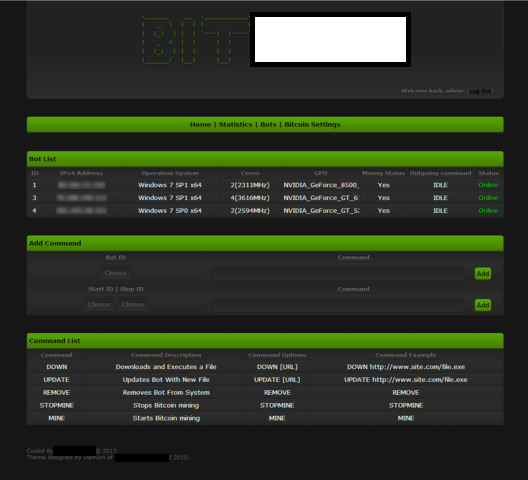
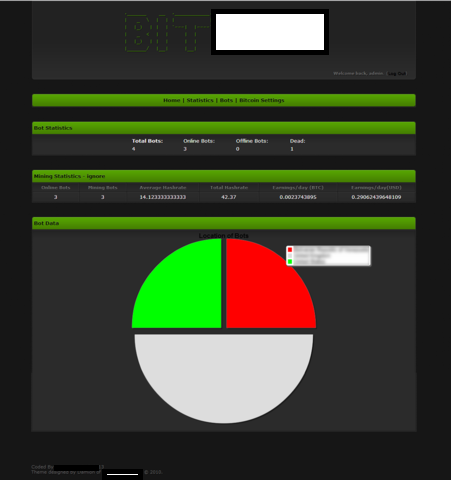
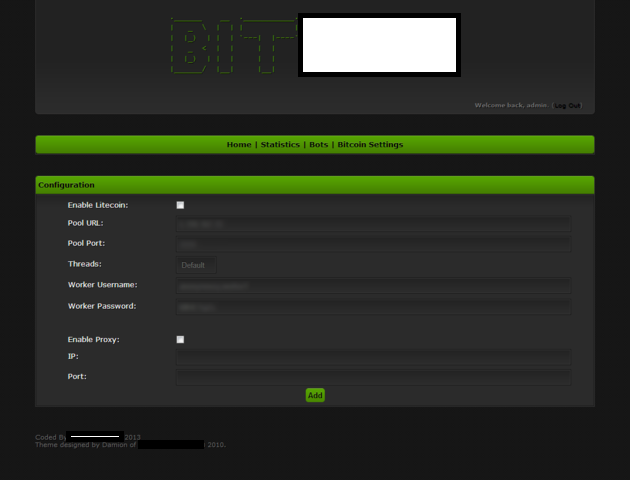
Sample screenshots of the stealth Bitcoin/Litecoin mining tool’s admin panel:
The Web-based, Stratum-protocol supporting Bitcoin/Litecoin stealth mining tool is coded in Visual Basic 6, and has the following features:
- Persistence on the affected host
- Automatic detection of idle-ing host
- Startup options
- Miner running from memory
- Statisics for the system specifications
- Mining statistics (hash rate)
- HTML5 based Web interface
- Competing bot killing capabilities
The price? $70 USD for a bin and access to a Web panel, and another 10 USD for an updated re-build. No actual DIY (do it yourself) building tool is offered.
What’s particularly interesting about this release is the fact that the cybercriminal behind it released it in a way that would prevent its mass spreading, supposedly due to the fact that he doesn’t want to attract the attention of security vendors whose sensor networks would easily pick up any massive campaigns featuring the miner. Therefore, he’s currently offering a limited number of copies of this miner.
Over the last couple of months we’ve been intercepting multiple subscription-based or DIY type of stealth Bitcoin/Litecoin miners, indicating that the international underground marketplace is busy responding to the demand for such type of tools. Despite the fact that Bitcoin is a ‘trendy’ E-currency, we believe that for the time being, Russian and Eastern European cybercrime gangs will continue to maintain a large market share of the underground’s market profitability metric, due to their utilization of mature, evasive, and efficient monetization tactics.
We’ll continue monitoring this international underground market segment, and post updates as soon as new releases are introduced to potential cybercriminals.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.