Throughout the last couple of years, the persistent demand for geolocated traffic coming from both legitimate traffic exchanges or purely malicious ones — think traffic acquisition through illegally embedded iFrames — has been contributing to the growing market segment where traffic is bought, sold and re-sold, for the sole purpose of monetizing it through illegal means.
The ultimately objective? Expose users visiting compromised, or blackhat SEO-friendly automatically generated sites with bogus content, to fraudulent or malicious content in the form of impersonations of legitimate Web sites seeking accounting data, or client-side exploits silently served in an attempt to have an undetected piece of malware dropped on their hosts.
A recently spotted cybercrime-friendly underground traffic exchange service empowers cybercriminals with advanced targeting capabilities on per browser version basis, applies QA (Quality Assurance) to check their fraudulent/malicious domains against the most popular community/commercial based URL black lists, and ‘naturally’ we found evidence that it’s already been used to serve client-side exploits to unsuspecting users.
More details:
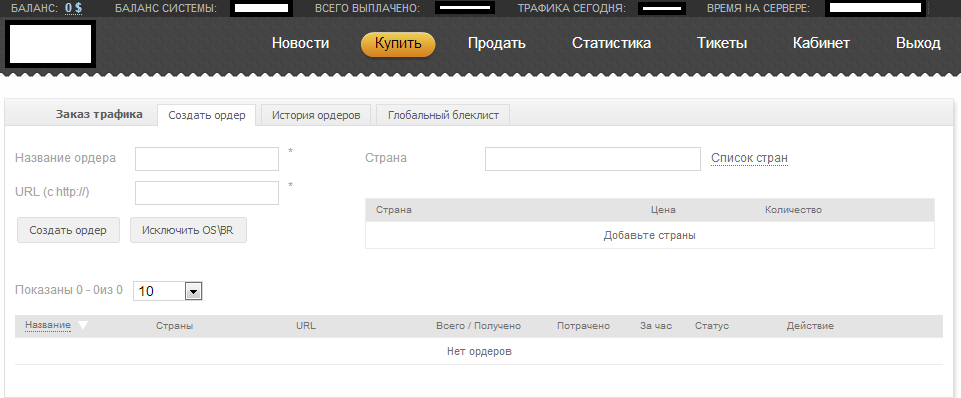
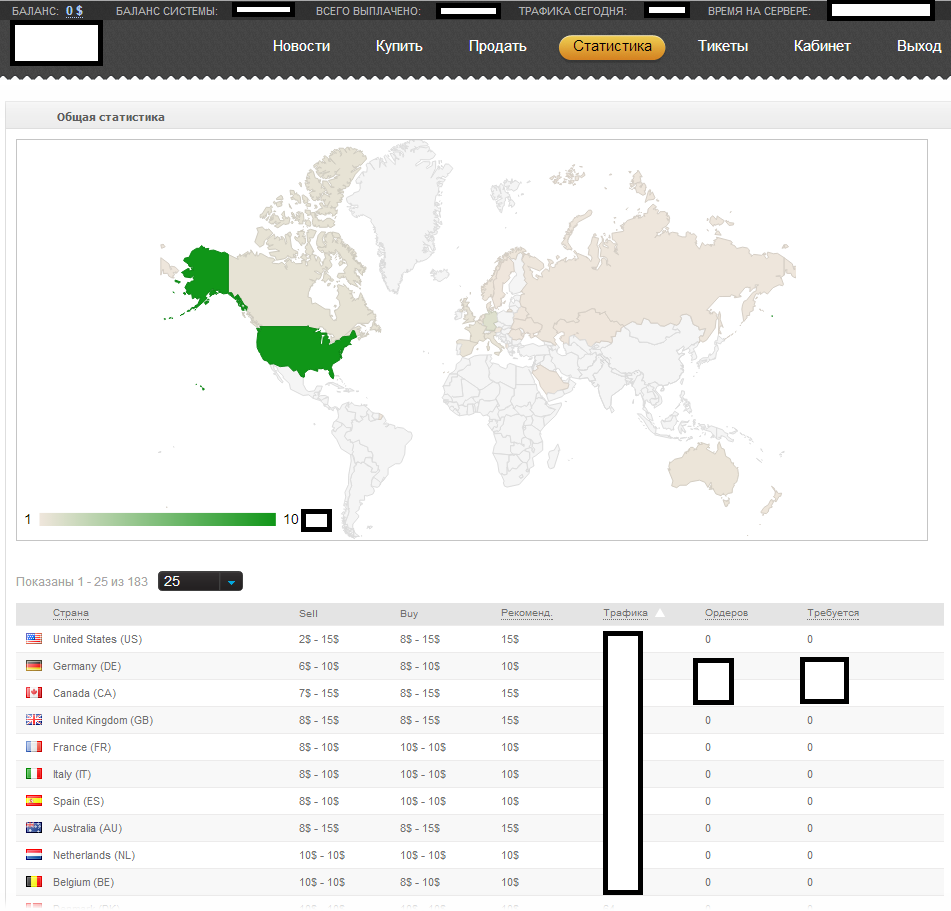
Sample screenshots of the Web-based interface for the underground traffic exchange:
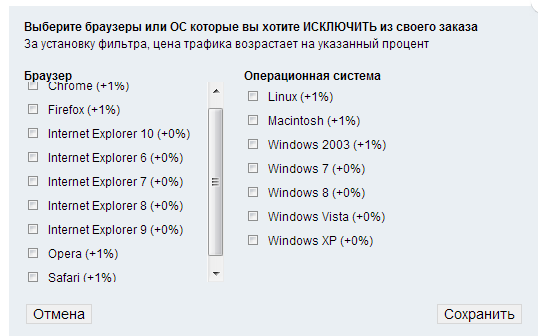
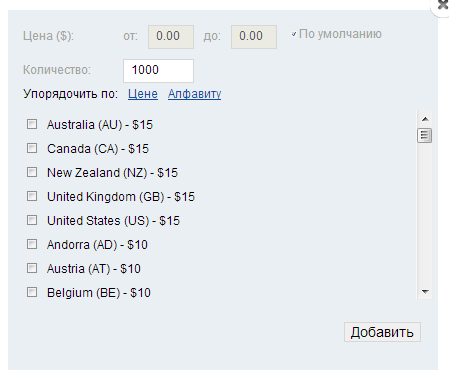
Potential cybercriminals can exclude which operating systems and browser versions they don’t want to see in their anticipated/hijacked traffic flow, so that they can better utilize virtually any — including outdated — Web malware exploitation kits in their campaigns. Not only does the service offer tens of thousands of unique visitors from virtually any given country, but it also allows the automatic rotation of the doorway script in those cases where it gets blacklisted by community/commercial IP reputation/URL blacklisting services/products.
Naturally, we’re already aware of the malicious use of this cybercrime-friendly service, with the cybercriminals using it already redirecting the traffic to their favorite Web malware exploitation kits.
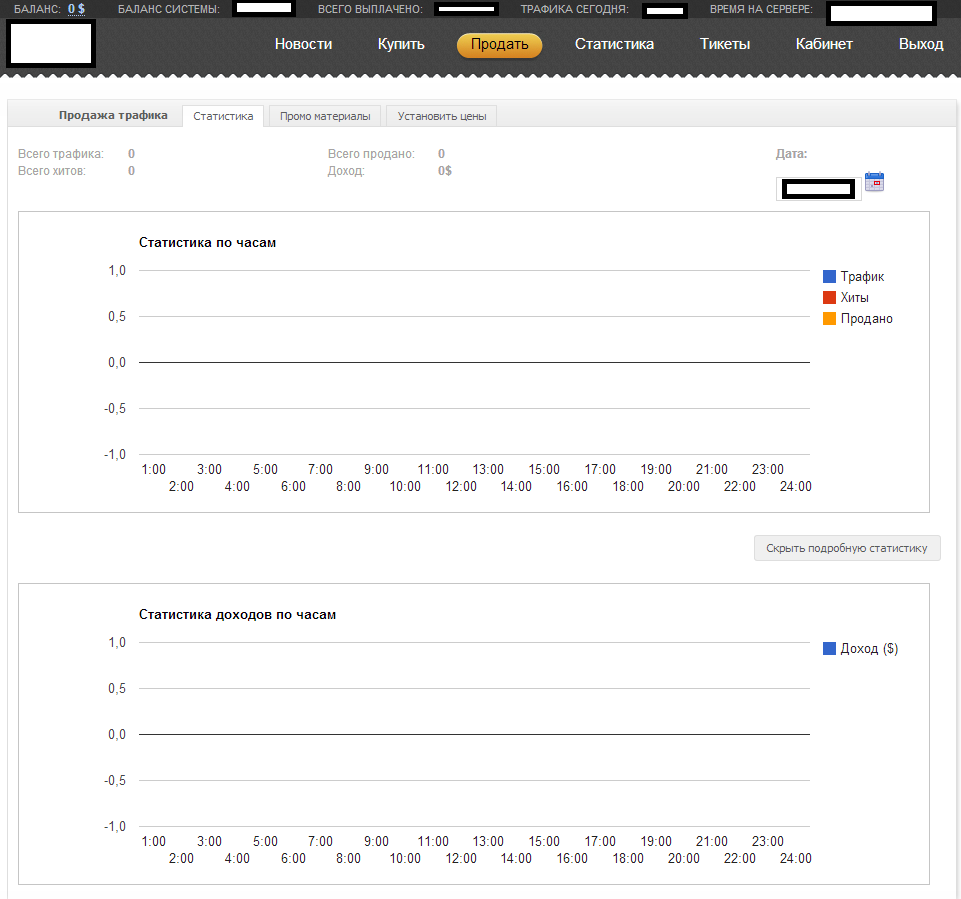
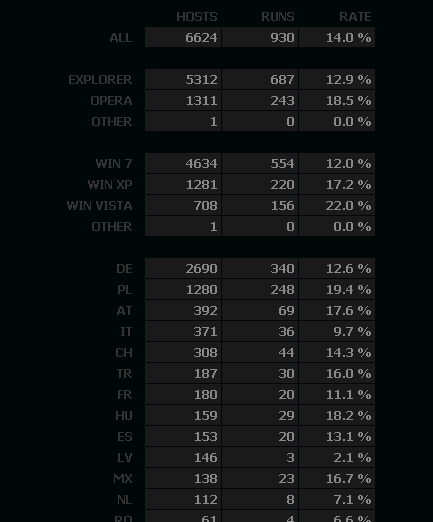
Sample screenshot of a Web malware exploitation kit statistics used by a user of the service:
‘Gate’ domain (in combination with a pseudo-random sudbomain) used over the past 24 hours:
bibinomiopertan.ru – 62.76.188.147 – Email: seo@me.com
The following domains are known to have responded to the same IP:
akeralopertinmer.ru
andyfoxx.com
areanantorius.ru
asterlotiomaki.ru
atlant-iz-msk.ru
baris-iz-astani.ru
bibinomiopertan.ru
binomen.ru
bipo-invest.ru
bk-astana-kaz.ru
bk-azovmash-ukraina.ru
bk-vef-latvia.ru
djfskdfjrewrer.ru
frewfrfdfdsfsfewr.ru
hk-akbars-best.ru
hk-dinamo-msk.ru
hk-krasno-sinie-armeici-msk.ru
hkloko-vsegda-vpered.ru
hksibir-novosibirsk.ru
hkslovan-bratislava.ru
jfidsfiurchdjhfdjf.ru
jksjdkfjsdkfj.ru
jsbalakkoir.ru
kjfjgdglferweew.ru
movistar-team-fan.ru
neftehimik-nignekamsk.ru
nflnews.ru
niropotinores.ru
nortok-invest.ru
omskiy-avangard.ru
pasv.ru
pragskie-lion.ru
radioshack-leopard-fan.ru
salavat-ula-ufa.ru
severstal-cherepovets.ru
spnation.ru
team-saxo-tinkoff-fan.ru
tractor-velikogo-goroda.ru
uweyqwiuikshchdffhds.ru
welsa-invest.ru
This underground market traffic exchange is just the tip of the iceberg, when it comes to the monetization of hijacked legitimate Web traffic. We’ll continue monitoring this growing market segment, and post updates as soon as we spot new services who have the potential to cause widespread damage, thanks to their customer-ized service offerings.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.