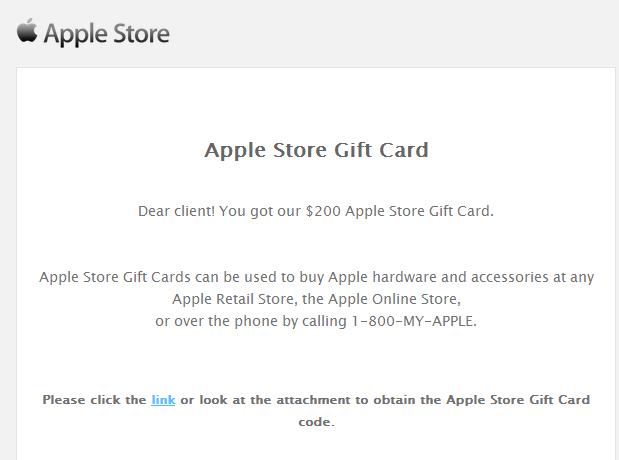
Apple Store users, beware!
A currently ongoing malicious spam campaign is attempting to trick users into thinking that they’ve successfully received a legitimate ‘Gift Card’ worth $200. What’s particularly interesting about this campaign is that the cybercriminal(s) behind it are mixing the infection vectors by relying on both a malicious attachment and a link to the same malware found in the malicious emails. Users can become infected by either executing the attachment or by clicking on the client-side exploits serving link found in the emails.
More details:
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment – MD5: 74cff87704aec030d7ad1171366aff87 – detected by 8 out of 46 antivirus scanners as UDS:DangerousObject.Multi.Generic; PWSZbot-FBX!74CFF87704AE.
Once executed, the sample starts listening on port 7499.
It the creates the following Mutexes:
Local{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Global{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global{5971F053-C032-A29C-11EB-B06D3016937F}
Global{5971F053-C032-A29C-75EA-B06D5417937F}
Global{5971F053-C032-A29C-4DE9-B06D6C14937F}
Global{5971F053-C032-A29C-65E9-B06D4414937F}
Global{5971F053-C032-A29C-89E9-B06DA814937F}
Global{5971F053-C032-A29C-BDE9-B06D9C14937F}
Global{5971F053-C032-A29C-51E8-B06D7015937F}
Global{5971F053-C032-A29C-81E8-B06DA015937F}
Global{5971F053-C032-A29C-FDE8-B06DDC15937F}
Global{5971F053-C032-A29C-0DEF-B06D2C12937F}
Global{5971F053-C032-A29C-5DEF-B06D7C12937F}
Global{5971F053-C032-A29C-95EE-B06DB413937F}
Global{5971F053-C032-A29C-F1EE-B06DD013937F}
Global{5971F053-C032-A29C-89EB-B06DA816937F}
Global{5971F053-C032-A29C-F9EF-B06DD812937F}
Global{5971F053-C032-A29C-E5EF-B06DC412937F}
Global{5971F053-C032-A29C-0DEE-B06D2C13937F}
Global{5971F053-C032-A29C-09ED-B06D2810937F}
Global{5971F053-C032-A29C-51EF-B06D7012937F}
Global{5971F053-C032-A29C-35EC-B06D1411937F}
Global{5971F053-C032-A29C-55EF-B06D7412937F}
Global{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
MPSWabDataAccessMutex
MPSWABOlkStoreNotifyMutex
And phones back to the following C&C servers:
50.65.158.6
216.56.52.130
70.169.168.37
99.146.98.160
189.242.35.122
157.100.168.252
184.39.153.172
178.238.233.29
68.22.158.150
108.210.219.218
108.74.172.39
99.0.126.100
90.156.118.144
217.114.113.148
66.63.204.26
130.251.186.103
75.1.200.201
188.129.147.67
69.115.119.227
94.240.232.143
95.104.0.54
76.226.134.206
86.135.15.147
211.33.132.158
121.160.84.54
76.189.224.55
67.78.107.130
110.169.227.239
46.121.59.30
66.101.206.254
Client-side exploitation chain: hxxp://www.smartadvmedia.com/h8qn42r.html -> hxxp://nutnet.ir/dl/nnnew.txt -> hxxp://www.emotiontag.net/cp/nnnew.txt -> hxxp://aurummulier.pl/nnnew.txt -> hxxp://stevecozz.com/topic/sessions-folk-binds.php – 173.246.104.52 – Email: frankieags@hotmail.com
Related client-side exploits serving domains known to have phoned back to the same IP/have been registered with the same email:
gottaghost.com
gottagirl.net
gottagirl.com
gottaguy1.com
gottagirl.info
gottagirl.us
Detection rate for a sampled client-side exploit: MD5: 91cb051d427bd7b679e1abc99983338e – detected by 2 out of 45 antivirus scanners as Mal/ExpJava-F.
Upon successful client-side exploitation, the campaign once again drops MD5: 74cff87704aec030d7ad1171366aff87.
We’re also aware of the following malicious MD5s that phoned back to same C&C servers over the past 24 hours:
MD5: 938a74b82f205c90606861d4ea37d48f
MD5: 24f98624699be0fdc74ce2f02340f67d
MD5: 3309b71b91851af8a2590a5f57649fd7
MD5: 2bade056325fcfec7b24618a5ee374bd
MD5: fcdfbc0604056f5a188431ef1d15549b
MD5: 074192e7f3b35725b9e14cbdc5189f6c
MD5: fcdfbc0604056f5a188431ef1d15549b
MD5: 074192e7f3b35725b9e14cbdc5189f6c
MD5: 139fe84beff22ffeb1ceef46fb243cbb
MD5: ed867f2eeb75aeb0392914022e62f9e2
MD5: 0be1b7f16091833da78f2a584ff4ecec
MD5: afc568ef98c67654ee89fe3ea1610408
MD5: 3ab0d85967e52ac246c4d52244f3dfc9
MD5: bf999b907ab611cb89aacd6304d87a68
MD5: b91a6e25625c724960990bdca9030bf4
MD5: 3af3b678570b3e30184db786b611d437
MD5: cb58ff571df8ba9c7960bcd03e35466b
MD5: c3b1884cda34740b38f4a273e3091e9e
MD5: d8cc4e1c491164f671a9a2e7f81178f0
MD5: 7d165513e1377213f231e7d89dcf3eee
MD5: b10d073b345f77426bac871d8a11498d
MD5: 38f247a3dec68004469bf4c745ee3617
MD5: f4ac698edd91803fbec358edcec1e09c
MD5: 27092120073d9ec572f0a83329eaa46d
MD5: 65e83c141307e3df6783c31b75204cbe
MD5: a0fe0824255b5f46b03bf33579ff9706
MD5: a5f399fa0f31d2d7695e6ce406ae434d
MD5: 80c86f34f2ae4062a7ec6918d4cd8e69
MD5: 1900dcd0c3a94f46a2b939b370d2d93f
MD5: e7569ff62e94952e03026d431ff7ad95
MD5: 092adf8366c7ccc584f590892225100b
MD5: 48cc5708ebe76f3908d3140ee9d05ece
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.