By Dancho Danchev
Operating in the open since 2009, a bulletproof hosting provider continues offering services for white, grey, and black projects, as they like to describe them, and has been directly contributing to the epidemic growth of cybercrime to the present day through its cybercriminal-friendly services.
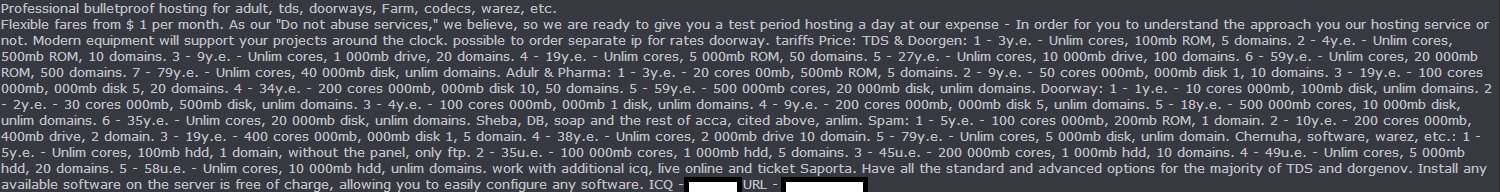
From Traffic Distribution Systems (TDS), to doorways, pharmaceutical scams, spam domains and warez, the provider is also utilizing basic marketing concepts like, for instance, promotions through coupon codes in an attempt to attract more customers.
More details:
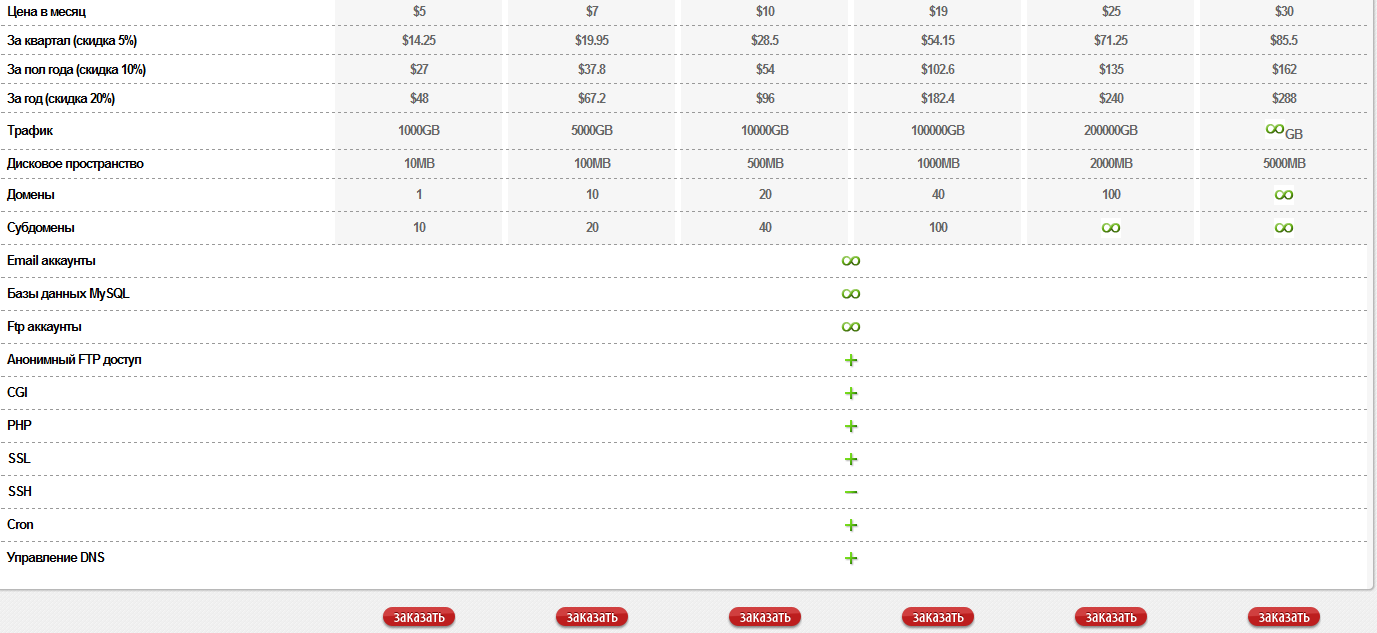
Sample screenshots of the provider’s market offering, including the actual cybercrime-friendly advertisement:
The bulletproof hosting provider currently operates dedicated servers in Canada, Latvia and Ukraine, as well as VPS/VDS servers in Ukraine and Latvia. The service celebrated this year’s international SysAdmin day, by issuing coupon codes offering 50% discount for all of its services.
- Knowledge tip – Go through an actual contract/agreement that cybercriminals had to ‘sign’ before using the infamous Russian Business Network’s (RBN) bulletproof hosting service
The service is just the tip of the iceberg in today’s mature market segment for bulletproof hosting services. Legally forwarding the responsibility for the malicious activity to their customers, in between ignoring all abuse requests, these services play an inseparable part of today’s modern cybercrime ecosystem relying on a combination of the following:
- abuse of purely malicious bulletproof hosting infrastructure – for years, their ‘even if it’s there, we still don’t care’ type of mentality is directly resulting in fulfilled customer (cybercriminal) orders. Despite the emergence of related hosting platforms for malicious content/command and control infrastructure, bulletproof hosting services will continue to play a crucial role in fraudulent/malicious operations of cybercriminals internationally
- abuse of purely legitimate infrastructure – from compromised Web sites, to compromised malware-infected hosts and legitimate services acting as command and control channels, what we’re currently observing is a mixed abuse of purely malicious and purely legitimate infrastructure in an attempt by the cybercriminals behind these campaigns to make it harder for researchers/the industry to shut down their operations
- active experimentation of alternative command and control channels over the years – From Twitter, LinkedIn, Baidu, MSDN, Facebook, Google Groups, Amazon’s EC2, ICQ and Yahoo Messenger, we’ve seen all of them abused as part of a cybercriminal’s command and control infrastructure
We’ll continue monitoring the developments in this market segment, and post updates as soon as new ‘innovative’ hosting offers become available.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.