The idea of controlling multiple, high-bandwidth empowered servers for launching DDoS attacks, compared to, for instance, controlling hundreds of thousands of malware-infected hosts, has always tempted cybercriminals to ‘innovate’ and seek pragmatic ‘solutions’ in order to achieve this particular objective.
Among the most recent high profile example utilizing this server-based DDoS attack tactic is Operation Ababil, or Izz ad-Din al-Qassam a.k.a Qassam Cyber Fighters attacks against major U.S financial institutions, where the use of high-bandwidth servers was utilized by the attackers. This indicates that wishful thinking often tends to materialize.
In this post, we’ll take a peek inside what appears to be a command and control PHP script in its early stages of development, which is capable of integrating multiple (compromised) servers for the purpose of launching distributed denial of service attacks (DDoS) taking advantage of their bandwidth.
More details:
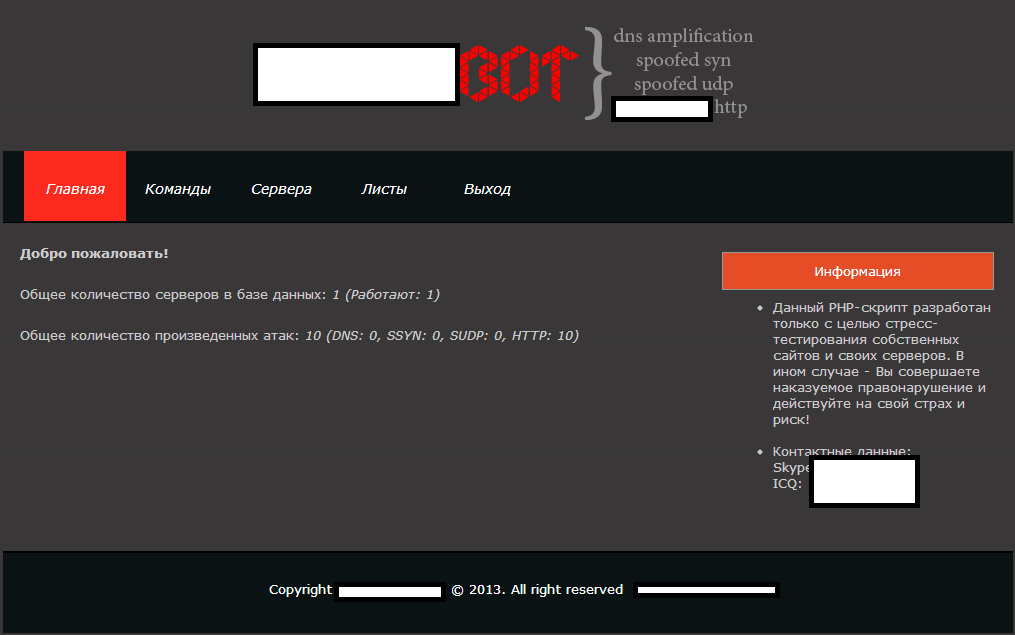
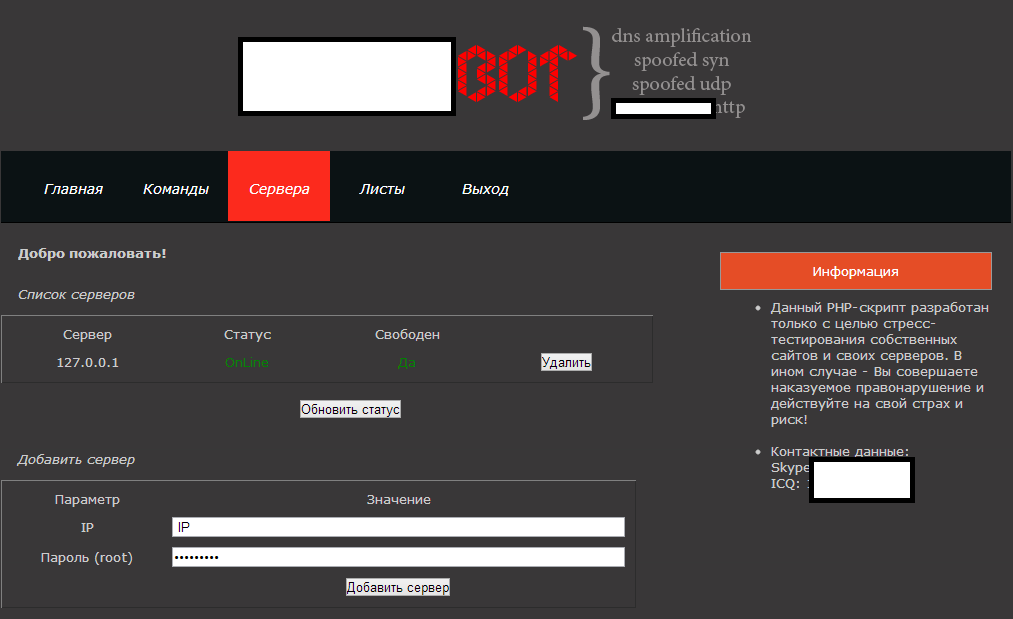
Sample screenshots of the administration panel of the PHP script:
Currently, the PHP script supports four types of DDoS attack tactics, namely DNS amplification, spoofed SYN, spoofed UDP, and HTTP+proxy support. The script also acts as a centralized command and control management interface for all the servers where it has been (secretly) installed on. It’s currently offered for $800.
Just like we’ve seen in numerous other cybercrime-friendly underground market releases, in this case, the author of the PHP script is once again forwarding the responsibility for its use to potential customers, and surprisingly, in times when fake scanned IDs continue getting systematically abused by cybercriminals, is expressing his trust in the user legitimization methods applied by his payment processor of choice – WebMoney.
We believe that this tool will eventually get abused by its customers, and we’ll continue to monitor its future development.
To find more about Dancho Danchev, follow him on Twitter.