In need of a fresh example of penetration pricing, within the cybercrime ecosystem, used by a cybercrime-friendly vendor in an attempt to quickly gain as much market share as possible in the over-supplied market segment for keylogging-specific systems? We’re about to give you a very fresh one.
A newly released, commercially available PHP/MySQL based, keylogging-specific malware/botnet generating system, with full Unicode support, is currently being offered for $5o, with the binary re-build priced at $20, in a clear attempt by the vendor to initiate basic competitive pricing strategies to undermine the market relevance of competing propositions. Just like the Web based DDoS/passwords-stealing tool that we profiled yesterday, this most recently released keylogging system is once again acting as a very decent example of a “me too” type of underground market release, whose overall success in the short term would mostly rely on basic branding, and whose long term success relies on the systematic introduction of new features.
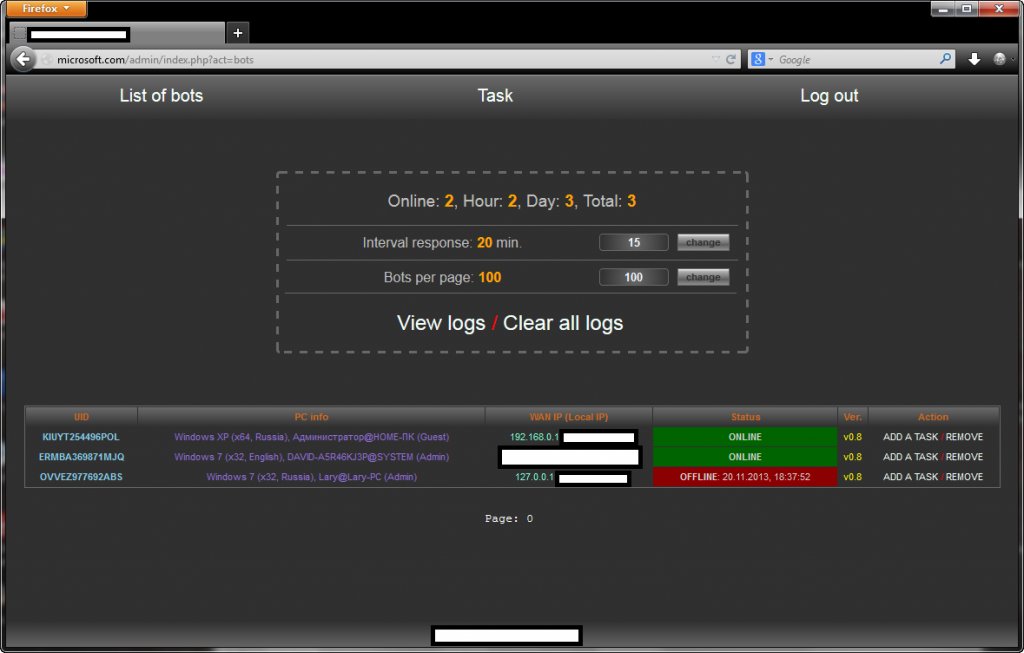
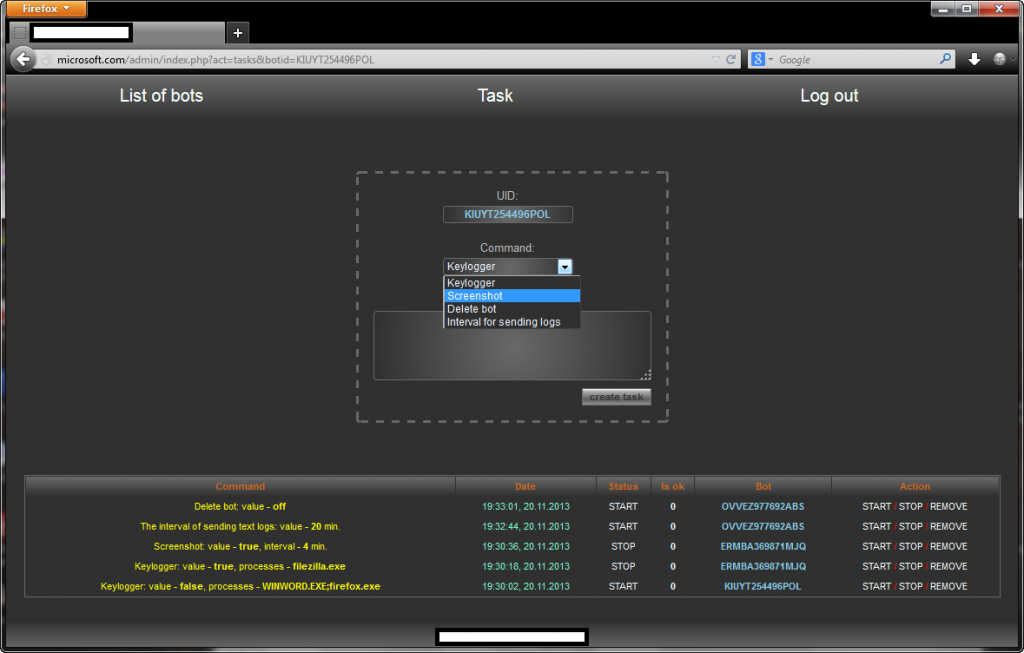
To get a better view of the tool’s core functions, let’s take a peek at its administration panel.
Sample screenshots of the Web based command and control interface:
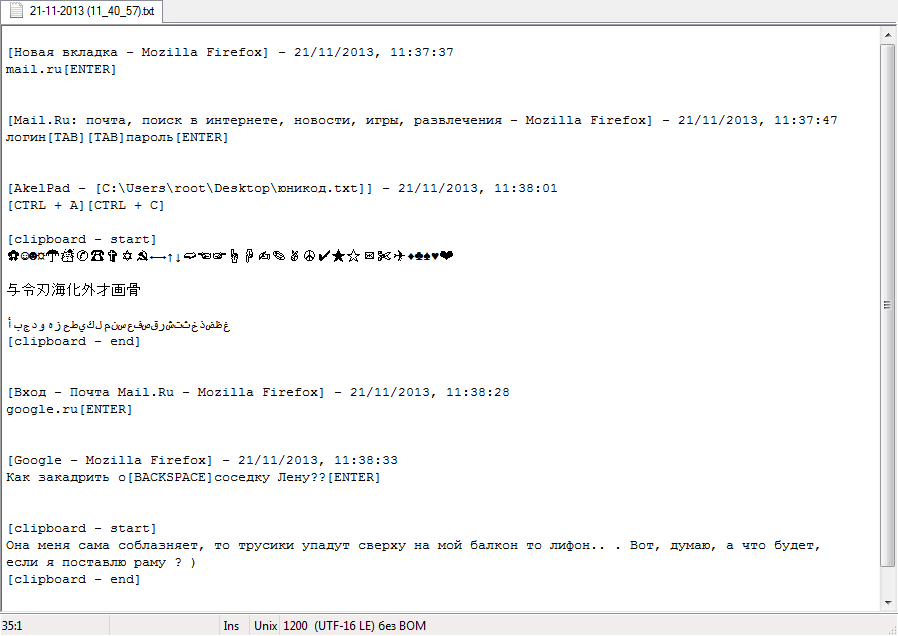
The vendor behind the release is applying the KISS (Keep It Simple Stupid) strategy, namely relying on good old fashioned keylogging concepts, including the automatic taking of screenshots from the Desktops of infected hosts, as well as the self-destruction option for the keylogger. The actual logs are then stored in text files, which would be later on ‘processed’ by the cyberciminals using log parsing tools popular within the cybercrime ecosystem, ultimately supplying E-shops with a steady flow of compromised accounting data, as well as utilizing it as a foundation to launch related malware disseminating attacks.
As always, we’re closely monitoring the future development of the keylogging system.
Meanwhile, readers interested in knowing more about keyloggers can watch the following video, featuring Grayson Milbourne, Webroot’s Security Intelligence Director, part of the Webroot Threat Vlog series, as well as another informative video demoing what happens when Webroot misses a potentially undetected keylogging application. Hint: we’ve got you covered!