Opportunistic cybercriminals continue ‘innovating’ through the systematic release of DIY (do-it-yourself), Web-based, botnet/malware generating tools, seeking to monetize their coding ‘know-how’ and overall understanding of abusive/fraudulent/malicious TTPs (tactics, techniques and procedures) – all for the purpose of achieving a positive ROI with each new release.
We’ve recently spotted a newly released, Web-based DNS amplification enabled DDoS bot, and not only managed to connect it to what was once an active DDoS attack, but also, to the abuse of a publicly accessible open DNS resolver which has been set up for research purposes. Let’s discuss some of its features and take a peek at the bot’s Web-based command and control interface.
More details:
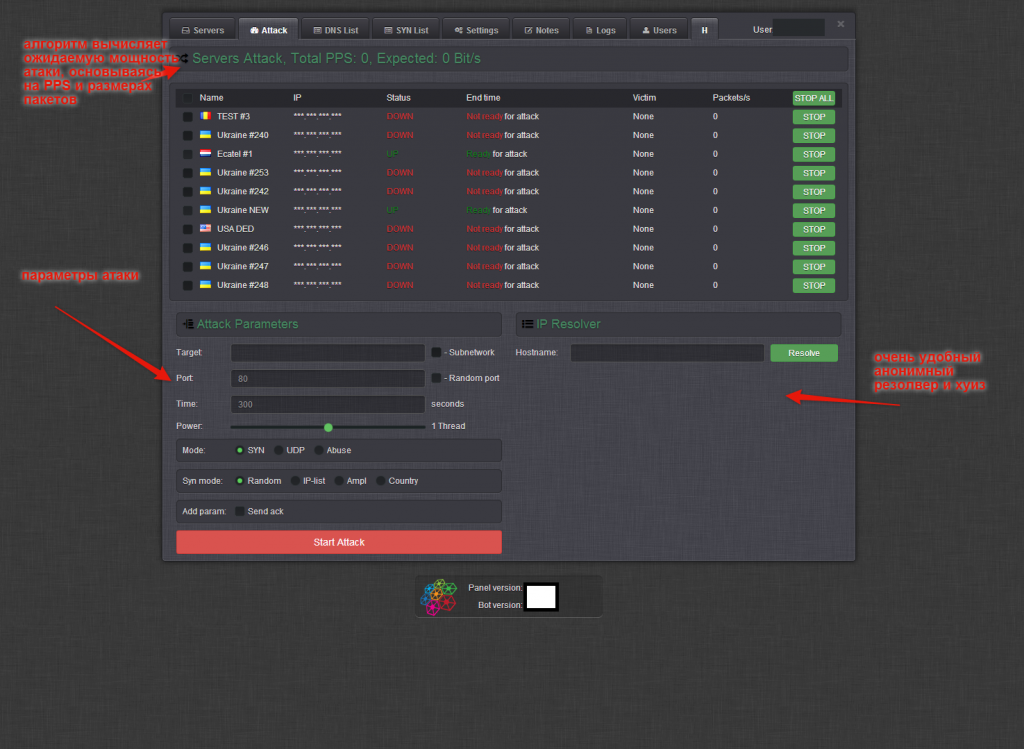
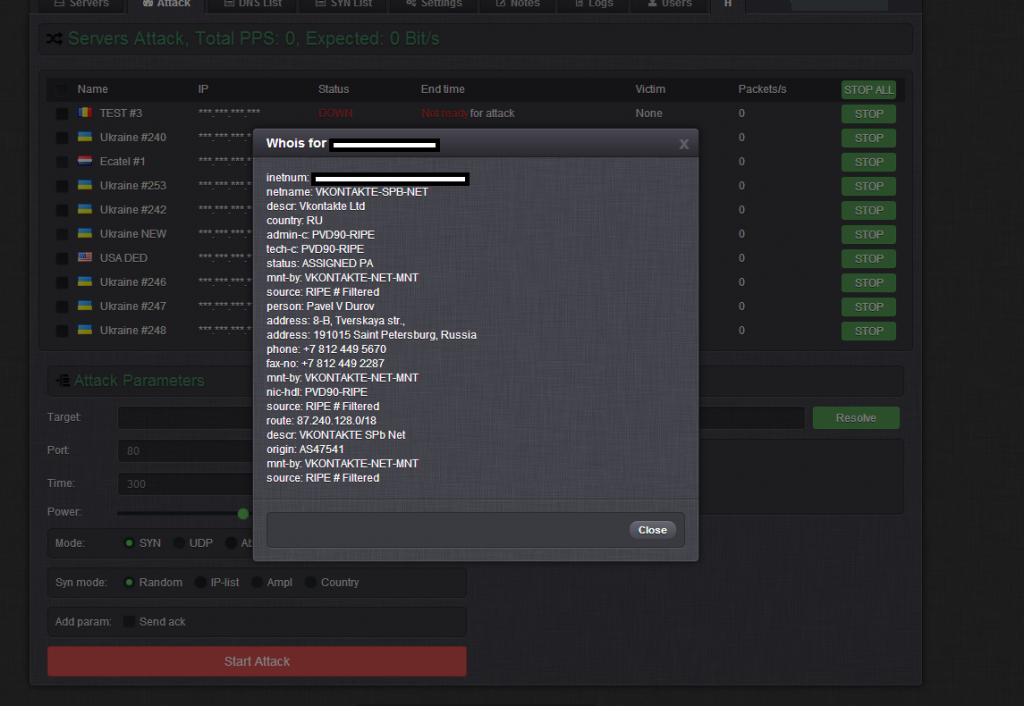
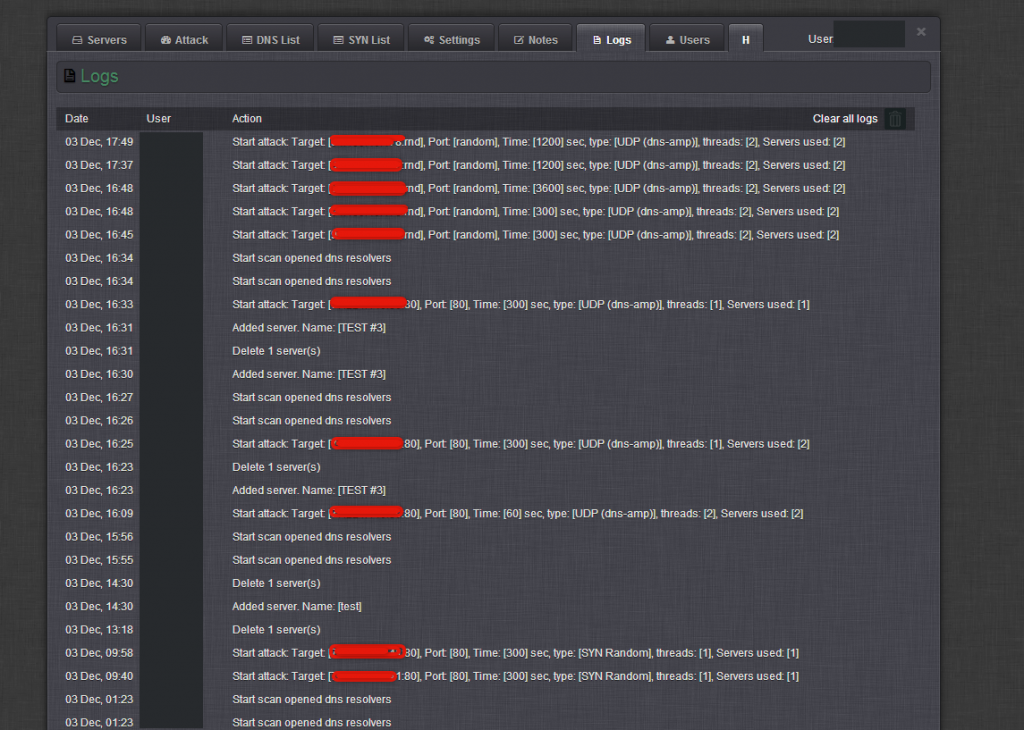
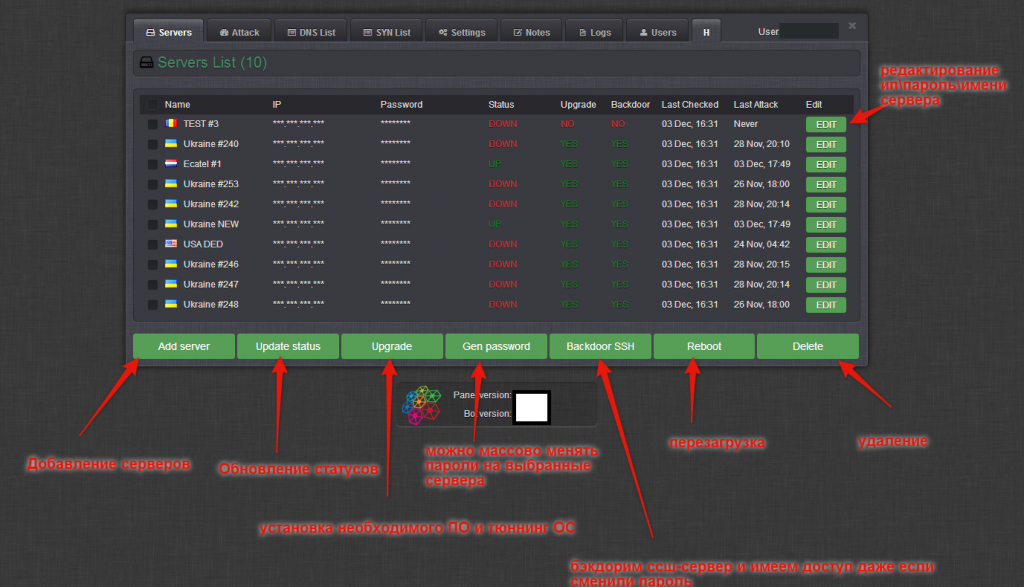
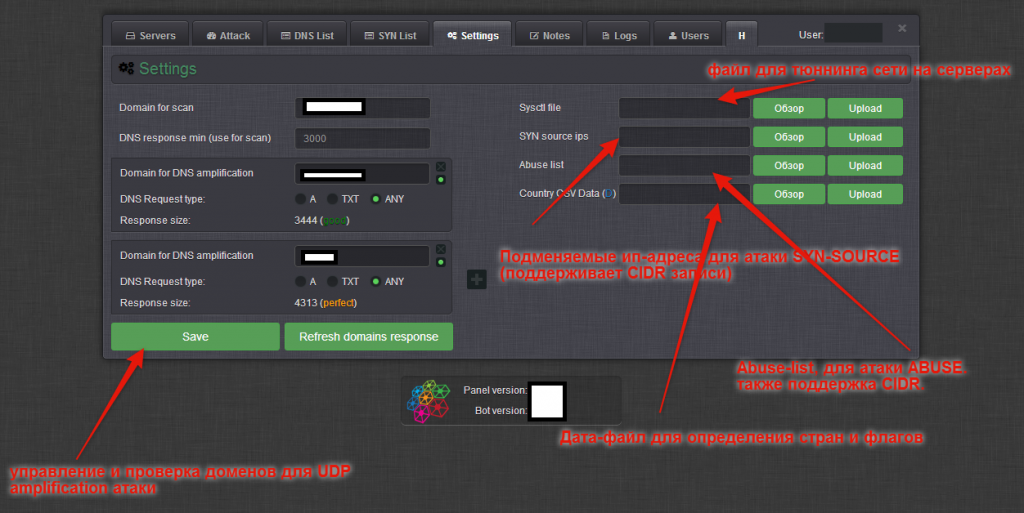
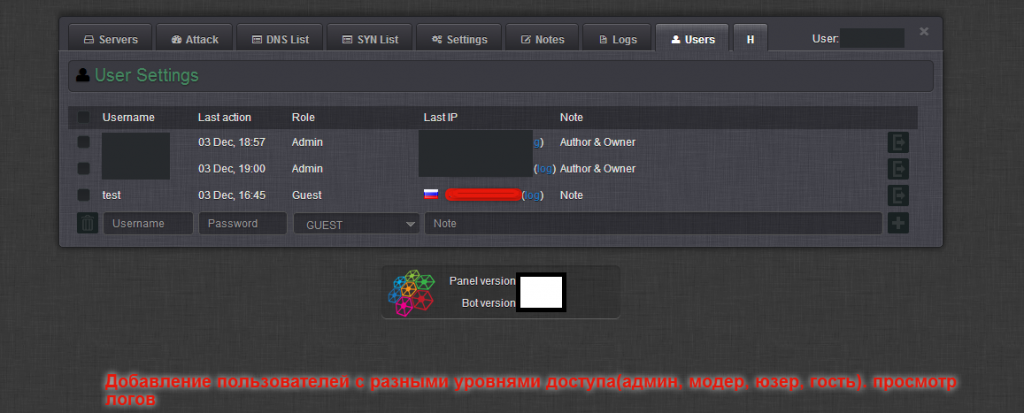
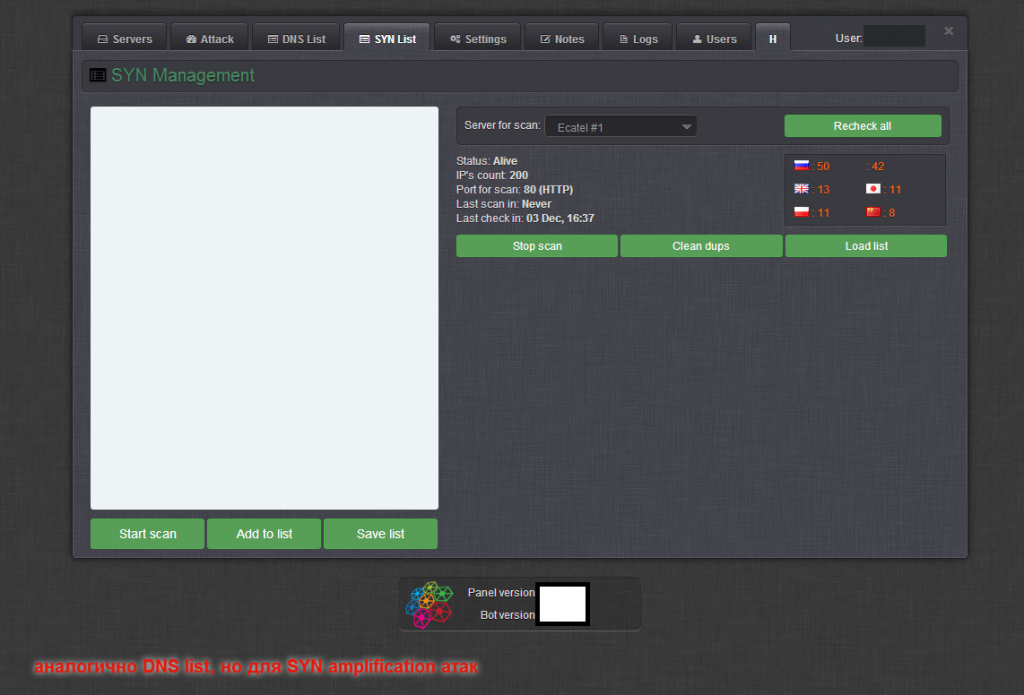
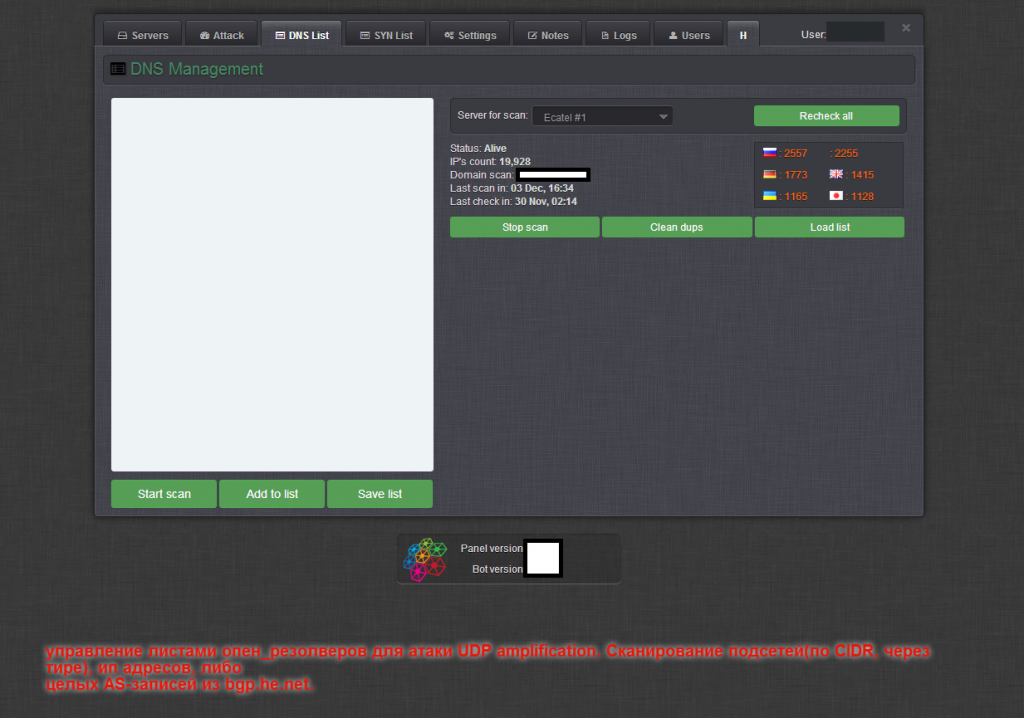
Sample screenshots of the administration panel of the Web-based DNS amplification DDoS enabled malware bot:
Just like we’ve seen with previous cybercrime-friendly releases, cybercriminals continue to stick to proven risk-forwarding tactics, consisting of pitching releases ‘for educational purposes only’, with the idea to be only utilized as a tool for performing stress testing scenarios.
Written in C, the bot is relies on its own obfuscation and packing algorithm. Packed, the binary’s size is approximately 30kb. Next to the active use of the Hardware ID licensing system, the bot’s C&C communications are also encrypted by default. It includes a built-in DNS scanner, for finding mis-configured DNS servers, to be used in high-bandwidth powered DNS amplification DDoS attacks which are utilized by a number of threat actors. Priced at $2,500, the vendor is also applying an additional OPSEC vector to the proposition, in the context of offering the option to host the actual archive, encrypted, on a server of choice based on the customer’s preferences, with the actual passphrase communicated in a secure fashion. It also offers a cybercrime-friendly bulletproof hosting option for hosting of the bot’s C&C. Among the value-added features offered by the vendor, is the ability to access a pre-configured VPN server to be exclusively used when accessing the bot’s interface.
What’s particularly interesting about this bot is the fact that the vendor’s demo included a live demonstration of the abuse of a publicly accessibly open DNS resolver, set up for research purposes. In combination with, both, the built-in mis-configured DNS scanner, high power managed/rented bulletproof server, as well as the active abuse of data obtained from publicly obtainable sources, we’re positive that the bot is poised to quickly gain marker share.
As always, we’ll continue monitoring the development of the tool.