In a cybercrime ecosystem, dominated by client-side exploits serving Web malware exploitation kits, cybercriminals continue relying on good old fashioned social engineering tricks in an attempt to trick gullible end users into knowingly/unknowingly installing malware. In a series of blog posts, we’ve been highlighting the existence of DIY (do-it-yourself), social engineeringdriven, Java drive-by type of Web based platforms, further enhancing the current efficient state of social engineering driven campaigns.
Let’s take a peek inside yet another Web based DIY Java applet distribution platform, discuss its features, and directly connect to the Rodecap botnet, whose connections with related malicious campaigns have been established in several previously published posts.
More details:
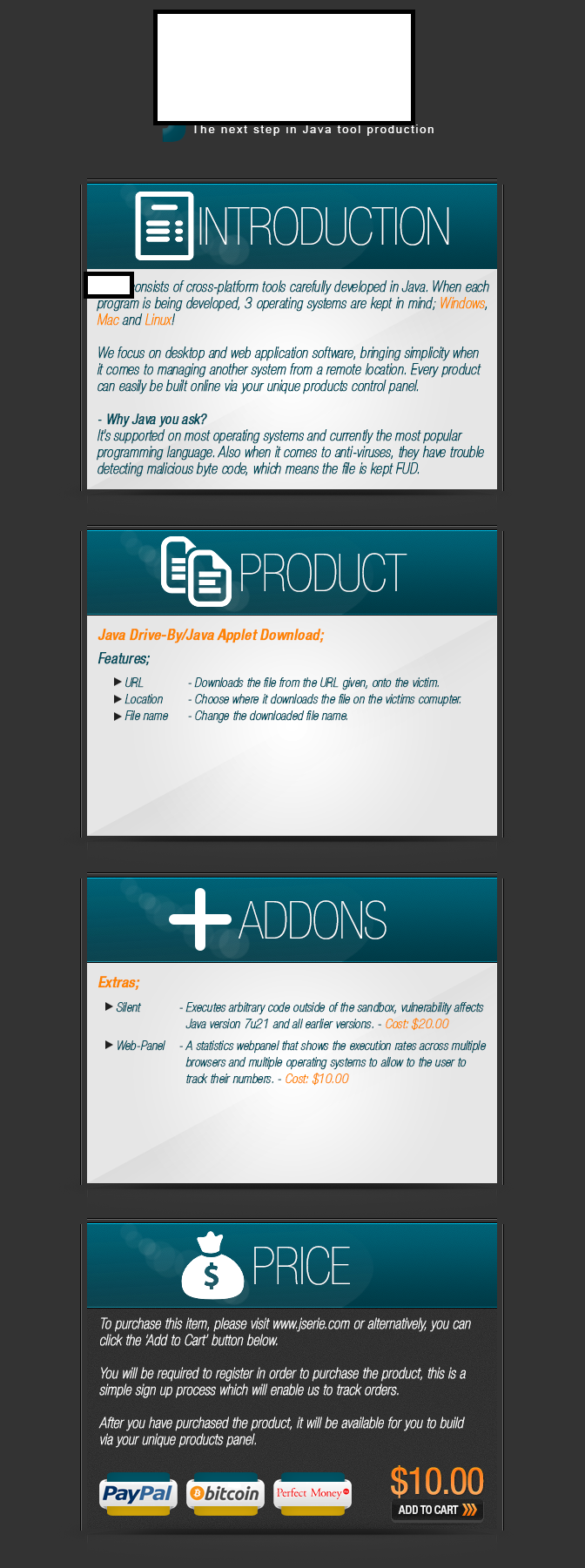
Sample screenshot of the DIY Java applet distribution platform:
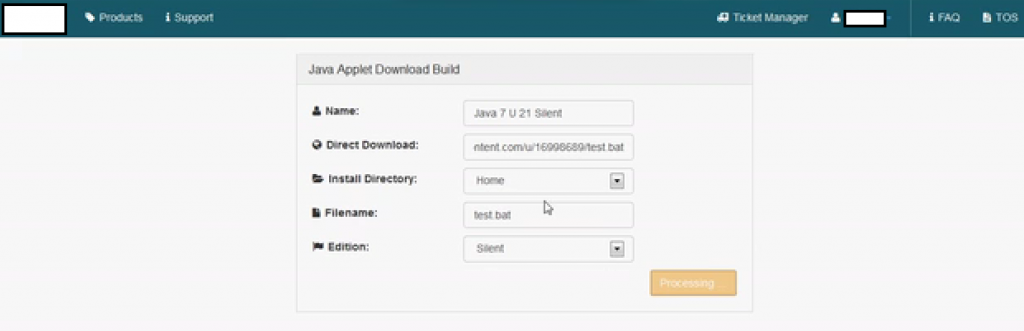
Sample screenshot of the DIY Java applet distribution platform’s Web based interface:
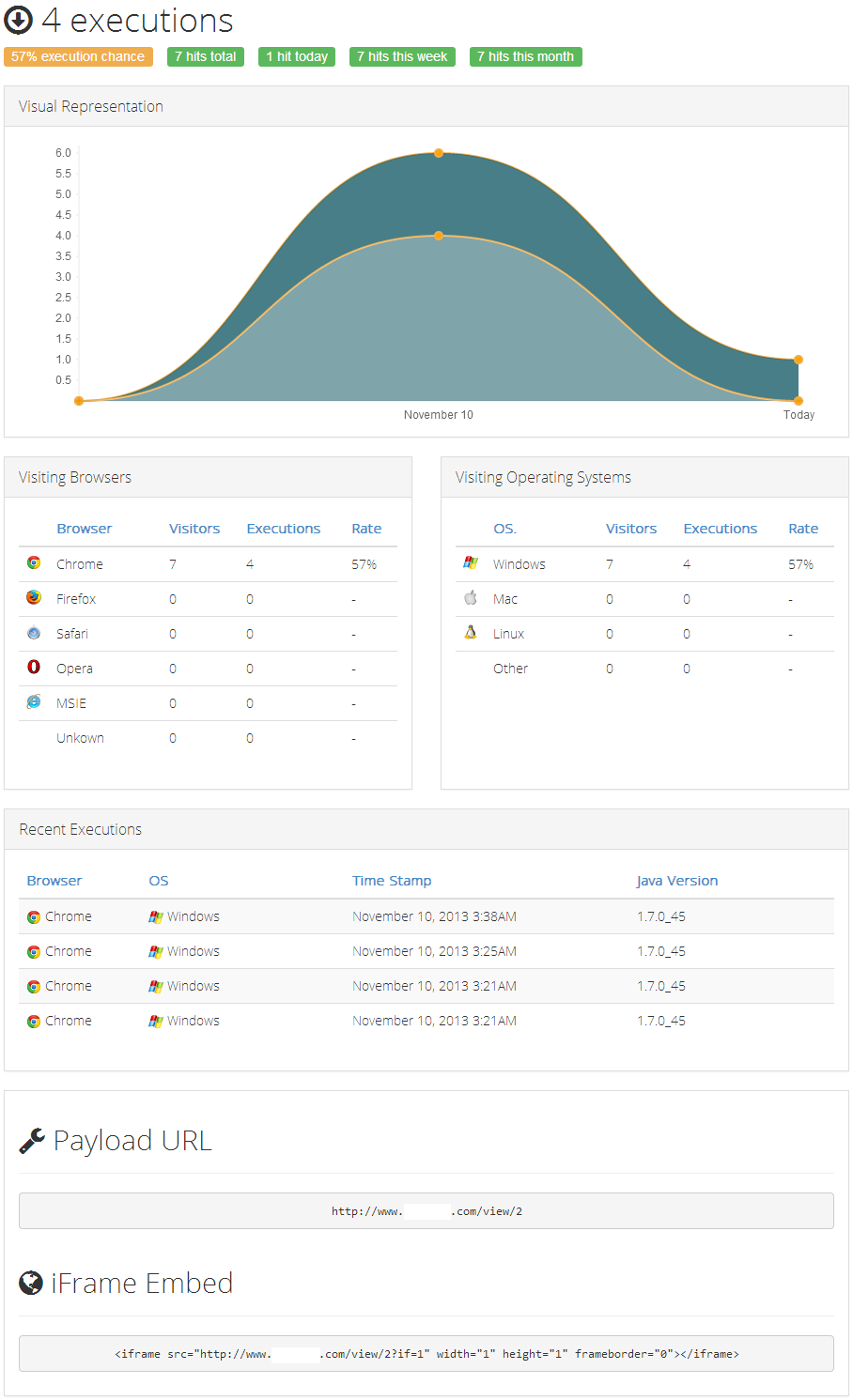
Sample screenshot of the DIY Java applet distribution platform’s statistics:
The cross-platform (Windows, Mac, Linux) Web based DIY Java applet distribution platform currently exploits a well known vulnerability in Java v.7u21, for the purpose of dropping malicious code on the exploited hosts, and supports detailed statistics for the number of successful installations.
Malicious domain name reconnaissance: hxxp://ntent.com – 50.19.104.123; 216.146.46.11
Known to have phoned back to the same IP (50.19.104.123) as the original hosting location:
MD5: f1f19a389a5705287b694a1302f1b05c
MD5: 9a04f31b23a3df208a04c61f267d26ed
MD5: 48703ab141b117be45af84aa423ee847
MD5: e96d37bcbb8fd089b41d459218460c76
MD5: cfba5f6f377d0c9055a4206ffd422fb1
MD5: f1f19a389a5705287b694a1302f1b05c
MD5: 9a04f31b23a3df208a04c61f267d26ed
MD5: 5d41b87ea2dd897dce8467d3d37012a1
Known to have been downloaded from the same IP (216.146.46.11) are also the following malicious MD5s:
MD5: 9a04fa3a72706559493a61a804806801
MD5: 63d56c0eb1eddc098c3a8236146a8dc5
MD5: 919b71d88938defae7bf544580023af0
MD5: 6fad9b57db0f373ca8cdd6750be47f30
MD5: 8fe4f12df5e8753b752046890df43c9a
MD5: 2c33da5f8f459d1f42db27fdda3aeb3a
Known to have phoned back to the same IP (216.146.46.11) are also the following malicious MD5s:
MD5: 2fa50721d5432d1ed71404c78723a789
MD5: 7d2c3f91c1e19359f508a1e89af5ac9c
MD5: d366088e4823829798bd59a4d456a3df
MD5: d448f1e0be73af1151d50774e5cdd737
MD5: bdea9256185bedd9ce70a667a9c5dd03
MD5: 3aa11e4f754ef1631aad1125e59d3aba
MD5: 64ed05b562fd38f15a27b3edbc5b9903
MD5: aef8e4b09e108ae8619133008341c09f
MD5: 2a323898d15ab57f855bdd0420887cd9
MD5: 005b9c62b51f92dca97129f30864dab8
MD5: d7c6371797a85cbd1b23c739c9e0b421
Once executed MD5: f1f19a389a5705287b694a1302f1b05c phones back to:
hxxp://buildingpower.net (178.63.70.81)
hxxp://prettypower.net (208.91.197.23)
hxxp://prettycountry.net (184.168.221.51)
hxxp://doublefamous.net (210.157.1.134)
hxxp://stillpower.net (50.19.104.123)
hxxp://eveningletter.net (112.78.117.97)
hxxp://outsidecountry.net
hxxp://buildingcentury.net
hxxp://eveningcentury.net
hxxp://buildingfamous.net
hxxp://eveningfamous.net
hxxp://eveningpower.net
hxxp://buildingcountry.net
hxxp://eveningcountry.net
hxxp://storecentury.net
hxxp://mightcentury.net
hxxp://storefamous.net
hxxp://mightfamous.net
hxxp://storepower.net
hxxp://mightpower.net
hxxp://storecountry.net
hxxp://mightcountry.net
hxxp://doctorcentury.net
hxxp://prettycentury.net
hxxp://doctorfamous.net
hxxp://prettyfamous.net
hxxp://doctorpower.net
hxxp://doctorcountry.net
hxxp://fellowcentury.net
hxxp://doublecentury.net
hxxp://fellowfamous.net
hxxp://fellowpower.net
hxxp://doublepower.net
hxxp://fellowcountry.net
hxxp://doublecountry.net
hxxp://brokencentury.net
hxxp://resultcentury.net
hxxp://brokenfamous.net
hxxp://resultfamous.net
hxxp://brokenpower.net
hxxp://resultpower.net
hxxp://brokencountry.net
hxxp://resultcountry.net
hxxp://preparecentury.net
hxxp://desirecentury.net
hxxp://preparefamous.net
hxxp://desirefamous.net
hxxp://preparepower.net
hxxp://desirepower.net
hxxp://preparecountry.net
hxxp://desirecountry.net
hxxp://strengthcentury.net
hxxp://stillcentury.net
hxxp://strengthfamous.net
hxxp://stillfamous.net
hxxp://strengthpower.net
hxxp://strengthcountry.net
hxxp://stillcountry.net
hxxp://movementsurprise.net
hxxp://outsidesurprise.net
hxxp://movementbeside.net
hxxp://outsidebeside.net
hxxp://movementletter.net
hxxp://outsideletter.net
hxxp://movementdifferent.net
hxxp://outsidedifferent.net
hxxp://buildingsurprise.net
hxxp://eveningsurprise.net
hxxp://buildingbeside.net
hxxp://eveningbeside.net
hxxp://buildingletter.net
hxxp://buildingdifferent.net
hxxp://eveningdifferent.net
hxxp://storesurprise.net
hxxp://mightsurprise.net
hxxp://storebeside.net
hxxp://mightbeside.net
hxxp://storeletter.net
hxxp://mightletter.net
hxxp://storedifferent.net
hxxp://mightdifferent.net
hxxp://doctorsurprise.net
hxxp://prettysurprise.net
hxxp://doctorbeside.net
hxxp://prettybeside.net
Once executed MD5: 9a04f31b23a3df208a04c61f267d26ed phones back to:
hxxp://strengthnation.net (192.0.80.250)
hxxp://buildingpower.net (178.63.70.81)
hxxp://prettypower.net (208.91.197.23)
hxxp://prettycountry.net (184.168.221.51)
hxxp://doublefamous.net (210.157.1.134)
hxxp://stillpower.net (50.19.104.123)
hxxp://resultsoldier.net
hxxp://brokenplease.net
hxxp://resultplease.net
hxxp://brokencondition.net
hxxp://resultcondition.net
hxxp://preparenation.net
hxxp://desirenation.net
hxxp://preparesoldier.net
hxxp://desiresoldier.net
hxxp://prepareplease.net
hxxp://desireplease.net
hxxp://preparecondition.net
hxxp://desirecondition.net
hxxp://stillnation.net
hxxp://strengthsoldier.net
hxxp://stillsoldier.net
hxxp://strengthplease.net
hxxp://stillplease.net
hxxp://strengthcondition.net
hxxp://stillcondition.net
hxxp://movementcentury.net
hxxp://outsidecentury.net
hxxp://movementfamous.net
hxxp://outsidefamous.net
hxxp://movementpower.net
hxxp://outsidepower.net
hxxp://movementcountry.net
hxxp://outsidecountry.net
hxxp://buildingcentury.net
hxxp://eveningcentury.net
hxxp://buildingfamous.net
hxxp://eveningfamous.net
hxxp://eveningpower.net
hxxp://buildingcountry.net
hxxp://eveningcountry.net
hxxp://storecentury.net
hxxp://mightcentury.net
hxxp://storefamous.net
hxxp://mightfamous.net
hxxp://storepower.net
hxxp://mightpower.net
hxxp://storecountry.net
hxxp://mightcountry.net
hxxp://doctorcentury.net
hxxp://prettycentury.net
hxxp://doctorfamous.net
hxxp://prettyfamous.net
hxxp://doctorpower.net
hxxp://doctorcountry.net
hxxp://fellowcentury.net
hxxp://doublecentury.net
hxxp://fellowfamous.net
hxxp://fellowpower.net
hxxp://doublepower.net
hxxp://fellowcountry.net
hxxp://doublecountry.net
hxxp://brokencentury.net
hxxp://resultcentury.net
hxxp://brokenfamous.net
hxxp://resultfamous.net
hxxp://brokenpower.net
hxxp://resultpower.net
hxxp://brokencountry.net
hxxp://resultcountry.net
hxxp://preparecentury.net
hxxp://desirecentury.net
hxxp://preparefamous.net
hxxp://desirefamous.net
hxxp://preparepower.net
hxxp://desirepower.net
hxxp://preparecountry.net
hxxp://desirecountry.net
hxxp://strengthcentury.net
hxxp://stillcentury.net
hxxp://strengthfamous.net
hxxp://stillfamous.net
hxxp://strengthpower.net
hxxp://strengthcountry.net
hxxp://stillcountry.net
Once executed MD5: 48703ab141b117be45af84aa423ee847 phones back to:
hxxp://mx1.games-olympic.org (95.163.104.68)
hxxp://list.newsleter.org (95.163.104.93)
hxxp://seek.newsleter.org (208.115.109.53)
hxxp://bt.newsleter.org (208.115.109.53)
hxxp://fw.newsleter.org (85.143.166.221)
Hence, the Rodecap connection. MD5: 48703ab141b117be45af84aa423ee847 phones back to newsleter.org which is a well known Rodecap C&C, which we’ve also seen in two previously profiled spamvertised malware-serving campaigns, including a direct connection to a cybercrime-friendly managed service, offering SMTP servers for rent.
Webroot SecureAnywhere users are proactively protected from these threats.