Relying on the systematic and persistent spamvertising of tens of thousands of fake emails, as well as the impersonation of popular brands for the purpose of socially engineering gullible users into downloading and executing malicious attachments found in these emails, cybercriminals continue populating their botnets.
We’ve recently intercepted a currently circulating malicious campaign, impersonating JJ Black Consultancy.
More details:
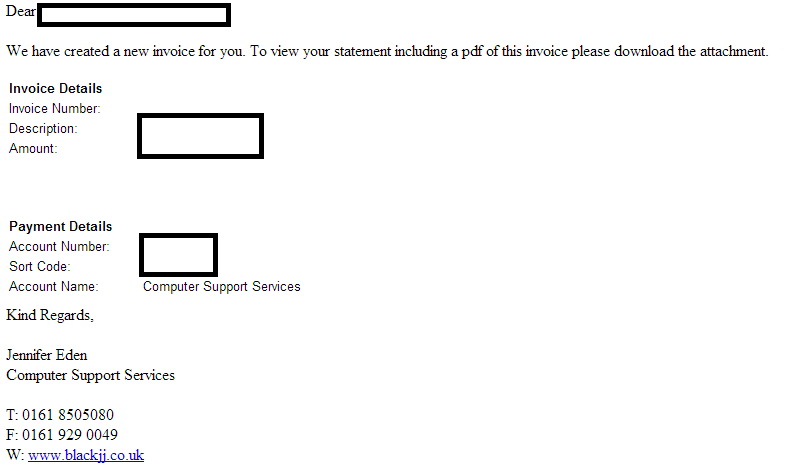
Sample screenshot of the spamvertised email:
Detection rate for a sampled malware: MD5: 57b83c8e86591dedd1f7a626bf97eff9 – detected by 3 out of 52 antivirus scanners as Win32/PSW.Fareit.E.
Once executed, the sample starts listening on ports 5954, and 7489.
It also drops the following malicious MD5s on the affected hosts – MD5: 4e551a70e04fa4a4186b2411d7c726e0
It also creates the following Mutexes on the affected hosts:
CTF.TimListCache.FMPDefaultS-1-5-21-1547161642-507921405-839522115-1004MUTEX.DefaultS-1-5-21-1547161642-507921405-839522115-1004
Local\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local\{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Local\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global\{CDAF0886-38E7-3642-11EB-B06D3016937F}
Global\{CDAF0886-38E7-3642-75EA-B06D5417937F}
Global\{CDAF0886-38E7-3642-4DE9-B06D6C14937F}
Global\{CDAF0886-38E7-3642-65E9-B06D4414937F}
Global\{CDAF0886-38E7-3642-89E9-B06DA814937F}
Global\{CDAF0886-38E7-3642-BDE9-B06D9C14937F}
Global\{CDAF0886-38E7-3642-51E8-B06D7015937F}
Global\{CDAF0886-38E7-3642-81E8-B06DA015937F}
Global\{CDAF0886-38E7-3642-FDE8-B06DDC15937F}
Global\{CDAF0886-38E7-3642-0DEF-B06D2C12937F}
Global\{CDAF0886-38E7-3642-5DEF-B06D7C12937F}
Global\{CDAF0886-38E7-3642-95EE-B06DB413937F}
Global\{CDAF0886-38E7-3642-F1EE-B06DD013937F}
Global\{CDAF0886-38E7-3642-89EB-B06DA816937F}
Global\{CDAF0886-38E7-3642-F9EF-B06DD812937F}
Global\{CDAF0886-38E7-3642-E5EF-B06DC412937F}
Global\{CDAF0886-38E7-3642-0DEE-B06D2C13937F}
Global\{CDAF0886-38E7-3642-09ED-B06D2810937F}
Global\{CDAF0886-38E7-3642-51EF-B06D7012937F}
Global\{CDAF0886-38E7-3642-35EC-B06D1411937F}
Global\{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global\{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global\{CDAF0886-38E7-3642-11EA-B06D3017937F}
Global\{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
It then phones back to the following C&C servers:
62.76.40.177
178.127.98.107
81.149.93.141
76.64.213.21
75.99.113.250
75.1.220.146
178.127.152.80
109.153.212.95
138.91.18.14
76.22.162.44
98.162.170.4
77.239.59.243
81.157.189.166
109.151.239.121
37.57.41.161
81.130.195.125
174.89.110.91
130.37.198.100
221.193.254.122
191.234.52.206
86.139.108.109
50.125.67.100
191.236.81.177
67.85.114.120
137.117.196.168
211.241.234.121
116.84.1.148
72.190.57.143
137.117.72.80
212.233.128.37
24.164.208.22
50.243.11.169
190.194.66.113
109.157.98.93
82.148.40.236
213.120.143.38
174.95.145.177
50.194.119.105
It also downloads the following malicious sample:
hxxp://62.76.40.177/2p/p.exe – MD5: 9f53ed77502c9c2e6d03e4cab3736adc – detected by 0 out of 51 antivirus scanners
Once executed MD5: 9f53ed77502c9c2e6d03e4cab3736adc starts listening on ports 3270, and 1285.
It then drops MD5: 92cdf94d187458771222ff5cdc8301e5 on the affected hosts.
It also creates the following Mutexes on the affected hosts:
CTF.TimListCache.FMPDefaultS-1-5-21-1547161642-507921405-839522115-1004MUTEX.DefaultS-1-5-21-1547161642-507921405-839522115-1004
Local\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local\{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Local\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Local\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global\{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global\{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global\{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global\{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global\{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global\{8E0327F4-1795-75EE-11EB-B06D3016937F}
Global\{8E0327F4-1795-75EE-75EA-B06D5417937F}
Global\{8E0327F4-1795-75EE-4DE9-B06D6C14937F}
Global\{8E0327F4-1795-75EE-65E9-B06D4414937F}
Global\{8E0327F4-1795-75EE-89E9-B06DA814937F}
Global\{8E0327F4-1795-75EE-BDE9-B06D9C14937F}
Global\{8E0327F4-1795-75EE-51E8-B06D7015937F}
Global\{8E0327F4-1795-75EE-81E8-B06DA015937F}
Global\{8E0327F4-1795-75EE-FDE8-B06DDC15937F}
Global\{8E0327F4-1795-75EE-0DEF-B06D2C12937F}
Global\{8E0327F4-1795-75EE-5DEF-B06D7C12937F}
Global\{8E0327F4-1795-75EE-95EE-B06DB413937F}
Global\{8E0327F4-1795-75EE-F1EE-B06DD013937F}
Global\{8E0327F4-1795-75EE-89EB-B06DA816937F}
Global\{8E0327F4-1795-75EE-F9EF-B06DD812937F}
Global\{8E0327F4-1795-75EE-E5EF-B06DC412937F}
Global\{8E0327F4-1795-75EE-0DEE-B06D2C13937F}
Global\{8E0327F4-1795-75EE-09ED-B06D2810937F}
Global\{8E0327F4-1795-75EE-51EF-B06D7012937F}
Global\{8E0327F4-1795-75EE-35EC-B06D1411937F}
Global\{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global\{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global\{8E0327F4-1795-75EE-09EE-B06D2813937F}
Global\{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
It also phones back to the following C&C servers:
178.127.98.107
81.149.93.141
76.64.213.21
75.99.113.250
75.1.220.146
178.127.152.80
109.153.212.95
138.91.18.14
76.22.162.44
98.162.170.4
77.239.59.243
81.157.189.166
109.151.239.121
37.57.41.161
81.130.195.125
174.89.110.91
130.37.198.100
221.193.254.122
191.234.52.206
86.139.108.109
168.61.87.1
137.117.196.87
70.25.45.37
67.85.114.120
137.117.72.241
138.91.4.159
178.126.1.253
197.34.35.121
72.190.57.143
188.51.30.90
24.164.208.22
191.236.81.177
50.126.86.87
117.197.245.246
58.168.141.132
72.69.51.146
190.194.66.113
174.90.83.42
191.234.43.116
2.25.191.243
99.138.53.104
99.116.64.244
137.116.229.40
2.229.17.34
85.206.54.80
104.0.129.219
71.19.196.232
Known to have phoned back to the same C&C server (178.127.98.107) are also the following malicious MD5s:
MD5: e029c548cbb0f6c6175354bc8e8354ed
MD5: ba2449a4425b9b33316d590941d32e77
Once executed, MD5: e029c548cbb0f6c6175354bc8e8354ed phones back to the following C&C servers:
178.127.98.107:6640
81.149.93.141:7325
76.64.213.21:3232
75.99.113.250:5436
Once executed MD5: ba2449a4425b9b33316d590941d32e77 phones back to the following C&C servers:
178.127.98.107:6640
81.149.93.141:7325
76.64.213.21:3232
75.99.113.250:5436
75.1.220.146:2763
178.127.152.80:1682
77.239.59.243:4106
81.157.189.166:4068
109.153.212.95:4808
138.91.18.14:2202
76.22.162.44:5877
98.162.170.4:6802
109.151.239.121:4627
37.57.41.161:2190
81.130.195.125:2607
174.89.110.91:1442
86.139.108.109:5374
130.37.198.100:2430
221.193.254.122:4753
50.194.40.50:4322
69.127.90.242:6324
137.117.197.214:8806
77.95.78.151:6221
67.186.153.229:7753
Webroot SecureAnywhere users are proactively protected from these threats.