Recently in the news we saw FireEye and Fox-IT provide the ability to decrypt files encrypted by older crpytolocker variants. They used the command and control servers seized by the FBI during operation Tovar. Since they have access to those RSA keys they essentially have the password required for every single file encrypted by a Cryptolocker variant that used Evgeniy Bogachev’s botnet. That is a major portion of the traditional red GUI cryptolocker that became famous. Any previous victims from these variants that still have encrypted files left on their machine should be able to decrypt them with ease. All they have to do is upload a single encrypted file to this webpage and their server will email you your RSA key. Then you can just download their tool (dubbed “DeCryptolocker”) and input the key and it will decrypt all files that are still encrypted. Sadly, anyone that was hit with different variants of encrypting ransomware are still out of luck.
However, since the emergence of their tool to decrypt files for free, there has been a new encrypting ransomware going around that aims at scamming you into thinking this is a similar helpful tool – except that it demands something all scams do….payment.
Presenting ZeroLocker
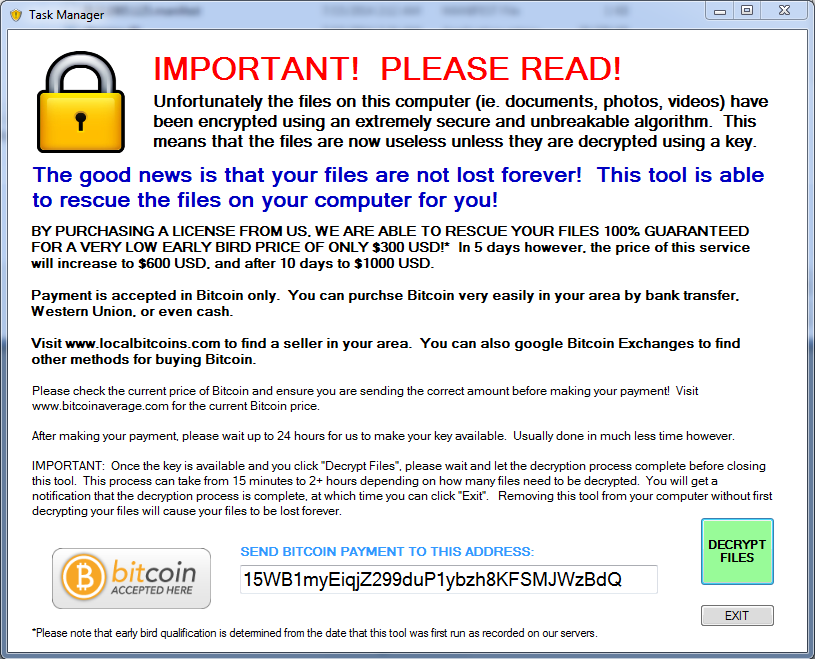
At least they have a 100% guarantee…
This newest edition to the ever popular business model that is encrypting ransomware doesn’t really have many improvements over the others we’ve already seen. Using Bitcoin for payment is standard now. This variant doesn’t show the GUI untill all encryption is completed and the computer is suddenly restarted. Upon restart this window is presented and threatens that you will lose all your files if you close or remove it. The payment structure is right where industry average is – PAINFUL. This specific variant we analyzed does not delete the VSS (Volume Shadow Service) and you can get all your files back by using programs like Shadow Explorer. Once again I expect issues like this to be fixed once this malware is adopted by more botnets for widespread distribution.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.







journaling in webroot does not work in case of this ransomware? I mean i know backup is the best option but you were advertising that roll-back feature of webroot quite a lot…is it useless at this type of ransomware?
Bobby82 In all of our tests journaling does work on this variant. However, we have seen some encrypting ransomware in the past where jounaling does not work so it’s best to use journaling as secondary backup protection
Tyler Moffitt Thanks for the reply.
Hi Guys. Any idea when will any decryption be available? The ransomware is easy to remove, but the files remain encrypted. FireEye/FoxIT can only decrypt Cryptolocker files so far. What about Zero locker?
Thanks,
Ivan I.
Systems Administrator
CUP, UK