 Today is Data Privacy Day, which is supposed to remind us all that keeping our digital secrets a secret is important and necessary. To commemorate the event, I’d like to run down some of the most serious privacy threats any of us could face on a daily basis: How a malware infection puts your privacy at risk.
Today is Data Privacy Day, which is supposed to remind us all that keeping our digital secrets a secret is important and necessary. To commemorate the event, I’d like to run down some of the most serious privacy threats any of us could face on a daily basis: How a malware infection puts your privacy at risk.
For years, it’s been clear that the creators and distributors of malicious software are after one thing above all others — money. Whether they steal it (by installing a keylogger, or just phishing) or defraud you out of it (by coercing users to pay good money for a useless security application, or holding your computer itself hostage) cash is the name of the game.
But this isn’t pickpocketry — they’re not literally taking money out of your wallet. Somewhere along the way, the Bad Guys are using your private information to do that. Here are just a few ways they accomplish this task, by hook or crook. And more importantly, some tips that you can use to put a crimp in their plans.
Tricks that demand you pay the criminals
Ransomware: A favorite dirty trick targeting people who pirate movies or commercial software is for the bad guys to sneak in a little blackmail alongside that bootlegged copy of Adobe Creative Suite. When executed, a ransomware program prevents you from doing anything at all on the computer until you pay up. In essence, your computer is held hostage, sometimes under threat of embarrassment or worse if a member of your household (or an employer) will inadvertently encounter the pornographic banner some ransomware variants display. The earliest ransom demands simply included an eGold account code where you could deposit the ransom, but the latest iterations of this travesty are a more subtle, potentially harmful threat to your privacy: They tell you to use your mobile phone to send a text message to a phone number, and you’ll receive in return a code which unlocks the computer. What victims aren’t told is how much this will cost them. Not only do the criminals have your mobile phone number, but they can charge almost anything to your mobile phone bill, and they do.
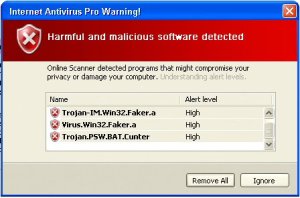
Rogue antivirus: Well documented by now, the rogue antivirus phenomenon is one of the most potentially lucrative online criminal enterprises. It also blurs the line between ransomware and a simple fraud: If the fake AV is the trap, its lure is the dreaded fakealert, which aims to convince victims they are in the middle of an attack. That, and the fake “results” these rogues often “discover” on a victim’s computer, constitute the fraud angle. But many rogues also refuse to let users remove them easily, or prevent you from using your own applications, and that crosses the line into ransomware. Victims who willingly pay the money are providing a complete financial portfolio — including full address and credit card details — to a criminal organization that has no qualms about abusing the data or reselling it to others for that purpose.
Tricks where the criminals simply take what they want
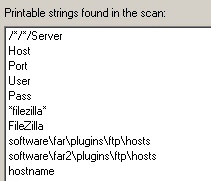
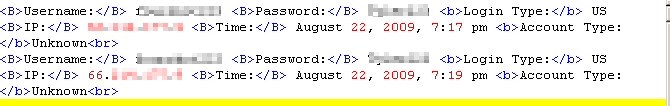
Password stealers: The people who distribute Trojan applications like Trojan-Backdoor-Zbot, in the guise of a wide variety of frauds, make no distinction between your credit card or email password. The Trojan simply takes every piece of information that’s potentially of value — Web site passwords, browser cookies, email account logins, FTP account passwords, bank information, and more — then sends it to the criminals, who can sort it out later. Zbot is one of the most well known and prolific of these types of spies, but there are hundreds of others. The mere presence of these malicious programs on your computer constitute the worst kind of privacy threat — the one you don’t know is happening right under your nose, that hands your most sensitive data right to the people who plan to abuse it.
Game phishers: A curious subset of the criminal underworld simply steals the player’s login credentials to the most popular of the persistent, multiplayer online games. Once these crooks have a login, they take control of the victim’s account and strip any of the virtual goods of value from the account holder’s characters in the game. Some of the games most frequently targeted by these Trojans include World of Warcraft, Lineage, Aion, and any other large multiplayer game with a large customer base and unique, tradeable items. Though the game publishers struggle to prevent it, these virtual goods can be traded or fenced for real-world money in various online auction houses or trading depots.
Social network worms: The value of word-of-mouth advertising is far greater than any other kind. Criminals who operate worm networks such as Koobface violate your privacy in an unprecedented way, by turning your social networking account into a mouthpiece for their own infection. Victims not only find that the worm sends messages to everyone they know, but that those messages invariably lead to files that can infect others. Sometimes the worm even creates new accounts using your computer. Once established on a victim’s computer, the worm also downloads additional threats, including rogue antivirus products and keyloggers, which add greater injury to the victim’s privacy.
What you can do to protect yourself
Don’ts
- When in doubt about a dire-sounding financial warning you receive via email, don’t follow the link; Call your bank or credit card company. The telephone call is free, and at the worst, you’ll have wasted a few minutes of your time.
- Don’t follow any links you receive in email, instant messages, or over social networks unless you know exactly where they lead or what they do. Sometimes, just one inadvertent click can lead to disaster.
- If you haven’t explictly tried to download an application or installer, but your browser is prompting you to run an application, don’t do it. Close your browser immediately, using the Alt-F4 key combination.
Dos
- Do install NoScript for the Firefox browser. It is the single most protective plugin you’ll ever use.
- Do ask knowledgeable friends, family, or colleagues questions for advice about unexpected messages or warnings that appear on your computer.
- Do use a good, reputable antivirus and antispyware product, and keep it up to date.





















The problem with disabling some of the firefox items is that certain scripts are needed for “legit” cheating of online games. By legit I mean non hacking scripts that assist with online games… I guess that is the rusk for cheating 🙂
I must say that the scripts are really something that has been scaring me like hell. I have gone ahead and added to “noscripts” plugin you mentioned above.
It is so difficult these days to get an honest opinion about internet security issues without getting loads of commercial garbage shoved down your throat.
It is sadly something that puts me of from looking for solutions to problems I regularly run into, but glad I stumbled on this article as it actually only give the information I needed.
Now I hope the noscripts plug in sorts out at least some of the problems. Thank you!
I’ve been into onlin games for a while, but luckily had no problems 🙂 Thanks for the info and advice on Noscript for Firefox.
Yeaah that’s good advice on pressing Alt F4, as soon as something tries to run and I’m prompted for it. I always type in fresh urls to go to sites, and especially if it’s something important like banking. Rather than relying on the links. I think it’s important to be able to invade others privacy, if they’re menacing, as in my blog article on the importance of a reverse cell phone look up.
The Alt F4 is such a great shortcut. That’s going to save me a lot of reaction time. Thanks again!
Excellent article. I had not heard of the ransomware attack before. Do programs such as Norton, MacAfee, or Spybot work against ransomware?