Late last year, we read all the buzz about ChromeInject, a malicious DLL that was being billed as the first malware specifically targeting Firefox. It was interesting to see 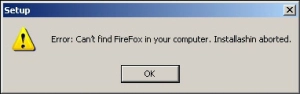 that someone built a phishing Trojan for a different browser platform, but ChromeInject was also clearly an early phase in Firefox malware development: It was fairly obvious, and it was easy to eliminate, because it generated an entry in the Plugins menu called “Basic Example Plugin for Mozilla” which you could simply disable with a single mouse click.
that someone built a phishing Trojan for a different browser platform, but ChromeInject was also clearly an early phase in Firefox malware development: It was fairly obvious, and it was easy to eliminate, because it generated an entry in the Plugins menu called “Basic Example Plugin for Mozilla” which you could simply disable with a single mouse click.
Well now it looks like the bar’s been raised. In the past few weeks, we’ve seen malware writers up the ante in their bets against Firefox. Two new spies came across the transom in the past week, and easily managed to load themselves into a freshly installed copy of Firefox 3.0.7. I should note that this isn’t due to any problem or negligence on Mozilla’s part; once you execute malicious code on your PC, any application is vulnerable. Firefox just happens to be a big target.
The first is a malicious plugin that, structurally, looks like it might be a new variant of a spy we’ve seen before: DNSChanger (we sometimes call it Trojan-Downloader-Ruin), a browser hijacking tool. Unlike DNSChanger, which modifies the DNS settings in Windows itself, this plugin doesn’t add any discernible registry keys in order to do its job. The installer drops a DLL payload into the C:Program FilesMozilla Firefoxcomponents folder, and works a little juju; then when you next start Firefox, it runs in the background.
Like DNSChanger, it injects ads or modified results when it detects search query strings sent to sites like Google, Yahoo, MSN, Altavista, Teoma, Ask, Pricegrabber, and a whole mess of other sites both in the .com and the .ru top level domains. It sends queries through the same Ukrainian IP address space — the 85.255.x.x subnet — DNSChanger used to use. It even calls itself by a cutesy name: Firesox.
In the past, we saw DNSChanger used to help fraudulent advertising affiliates boost their numbers, and to direct unsuspecting users to rogue antimalware tools by generating bogus results. It remains to be seen whether this new variant will be as prolific as the old version.
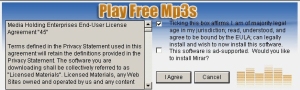
The second is a piece of adware that only installs correctly with Firefox 3.x installed — it won’t install under Firefox 2.x. We got a copy of it bundled along with the installer for a third-party Firefox plugin called PlayMP3z. The PlayMP3z installer includes a lengthy EULA, which explicitly says that the software is ad-supported and spells out the atrocious terms if you install the music streaming plugin.
But what looks like a concession to the interests of the end user, offered during installation, doesn’t turn out so rosy. During the installation, you’re given a choice to opt out of installing a well-known toolbar called Mirar Webband. We, of course, assume that Mirar is the adware client, and that if we choose not to install it, we won’t be saddled with ad popups.
But that’s misleading: Mirar is not the only adware the product installs; even if you deselect the Mirar checkbox, you still get saddled with something that calls itself Foxicle (installed under c:documents and settingsall usersdocumentsfoxicle), which itself generates popup and popunder ads.
Neither Firesox, the DNSChanger clone, or Foxicle put an obvious entry in Firefox’s plugins dialog (to get there, click the Tools -> Add Ons menu items) that signal their presence. While not widely distributed, I suspect we’ll be seeing more of them.



















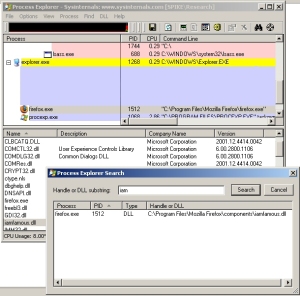

Firefox will not start at all. Re intalling does not help. i tried with a new windows user and same thing. none of the firefox utilities will start either.
firefox will not even start. computer thinks there is no firefox.exe. firefox utilities will not start either.