Just like today’s modern economy, in the cybercrime ecosystem supply, too, meets demand on a regular basis.
With malware coding for hire propositions increasing thanks to the expanding pool of talented programmers looking for ways to enter the cybercrime ecosystem, it shouldn’t be surprising that cybercriminals are constantly releasing new malware loaders, cryptors, remote access trojans, or issuing updates to web malware exploitation kits on a periodic basis, using the outsourcing market model.
Continuing the “Peek inside…” series, in this post I’ll profile the Elite Malware Loader. In the wild since 2009, the malware loader is still under active development according to a recently spotted advertisement within the cybercrime ecosystem.
Key features of the Elite Malware Loader include:
[+] Coded in pure WinAPI C++/Asm.
[+] Build size: 11 kb
[+] Protocol encrypted with dynamic key
[+] Random file names
[+] Resident
[+] Works in windows xp sp1/2/3, vista
[+] URL encrypted in build
[+] Firewall bypass: windows firewall, outpost, McAffee
[+] Can execute multiple commands in simultaneously
[+] Can be used after execution, without reboot
Screenshots of the Elite Malware Loader:
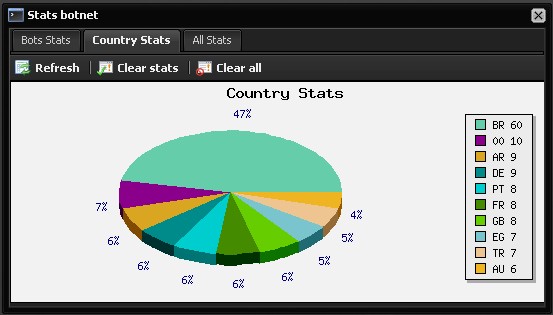
As you can see in the attached screenshots, the malicious attackers advertising the malware loader, has already managed to infect 60 PCs located in Brazil.
What’s particularly interesting about the Elite Malware Loader is that it’s released by a Russian malware coder known as Lonely Wolf, and that according to the description of the malware loader, it’s capable of bypassing Microsoft Window’s Firewall successfully.
The malware loader appears to be under active development by third-party coders, modifying its leaked source code for their own needs. This open source malware is highly modular, allowing third-party authors to innovate on the basis of using its source code.
The latest modifications in “Elite Loader 4.0” are courtesy of the M4x123 malware coder:
- The Gui (Webpanel) based on the Original Webpanel but with new Statistics and some other Modifications
- The Bot itself is coded fully in C++, all API Calls are Encrypted with XOR, my Routine.
- Current BotSize 12KByte. I think i will make it smaller.
- May I Include some Kiddy shit like DDOS or Something like ZeuS (Form Grabber)
- I’m thinking about to include Reverse Proxy and a scripting Engine (Like Visual Basic Syntax ^_^)
Webroot’s security researchers will continue monitoring the development of this loader to ensure that Webroot SecureAnywhere customers are protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.